
Getty Images/iStockphoto
Zoom launches Okta Authentication for E2EE to verify identity
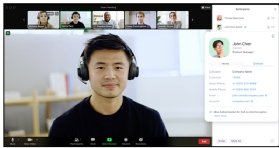
Authenticated Zoom attendees will get a blue shield icon next to their participant name to give enterprises additional security during sensitive meetings.
Enterprises users can now further authenticate Zoom meeting attendees to decrease the threat of participant impersonation as deep fakes become a growing concern.
The new security feature, Okta Authentication for End-To-End Encryption (E2EE), launched Monday and is available for all paid Zoom customers. Once it is enabled under the security tab, verified Zoom meeting participants will have a blue shield icon next to their names to confirm their identities.
The new verification feature goes beyond the standard login and passcode system for Zoom meetings. Depending on the customer's configuration, users can be authenticated automatically by their Zoom account administrator or be redirected to an Okta portal to complete the authentication process with login credentials and two-factor authentication.
"Okta Authentication for E2EE is another tool in the toolbox to help make virtual environments safer and more secure," Josh Parecki, head of trust & safety and associate general counsel at Zoom, told TechTarget Editorial. "Customers who choose to enable this feature will better be able to identify people who aren't authenticated via Okta, and can choose whether or not they want them in their virtual environments."
While Zoom and Okta partnered in the past for E2EE options, the new tool adds another layer of trust as threats to video conferencing grow.
A rapid rush to remote work in 2020 during the COVID-19 pandemic accelerated the need for video conferencing platforms. Zoom was faced with increasing security demands to support a massive number of new users. Even as security measures improved with features like the waiting room, Zoombombing became a persistent problem. Unauthorized users interrupted meetings with inappropriate images, video and text.
Chris Niggel, Okta's regional CSO for the Americas, said one of the challenges with Zoom is that once participants are in a meeting, there is no authentication to the individual unless the camera is turned on or the users know one another.
"Because you have the capability to change your name or change your image, and if you've never heard me speak before or if I was just quiet throughout the meeting, you have no way to verify that it was me, or somebody pretending to be," he said.
Okta has observed an increase in phishing threats and identity forgery among its customers. Niggel said identity forgery is evolving with artificial intelligence tools, such as computer-generated voices, which could be used to compromise a Zoom meeting. As enterprises continue to use Zoom for sensitive conversations, verifying individuals is necessary to maintain that trust, he said.
More alarming than voice generators is the use of deepfakes, which have become extremely realistic. Niggel said it's approaching the point where deepfakes should be considered a serious threat. Developing protections now against the burgeoning threat is imperative, he added.
"The capabilities exist," he said. "It's not a stretch to consider some threat actor generating a deepfake of an individual then joining meetings to gain intelligence about their competition or anything else."
Those types of advanced attacks may still be theorical at this point. "As of now, we're not receiving reports from customers related to deepfake-related abuse," Parecki said.
Still, he said Zoom's trust & safety and security functions are designed with "a continuous feedback loop that includes not just these teams, but also our engineering, product, and other teams" so the company can quickly identify and address emerging threats.
The new authentication tool, which was introduced in a blog post on Monday, aims to protect against various impersonation methods, including deepfakes. Once an organization's Zoom administrator turns on Okta Authentication for E2EE inside a meeting, employees will be prompted to authenticate with Okta using their organization's identity flow. That could include touch or face identification, Niggel said.
If the user is who they say they are, a blue shield will appear next to their name in the participants list. Additionally, if users hover over the blue icon, a card displaying the person's company domain and corresponding Okta-verified email address will be available.
However, users can choose not to authenticate and remain in the meeting. It will be up to the enterprise to mandate authentication for meetings.
"We've all been in a Zoom meeting where a weird number pops up and then you ask, 'Who's that phone number? Who else is listening to this call?'" Niggel said. "It helps solve for this problem in a trustworthy, unobtrusive way."







