
denisismagilov - stock.adobe.com
Cyber insurance carriers expanding role in incident response
While cyber insurance has its benefits, infosec professionals expressed concern that carriers have too much influence over incident response decisions, especially with ransomware.
Cyber insurance carriers have played a significant and growing role in incident response. But some infosec professionals believe they may have too much influence.
The cyber insurance market has grown increasingly contentious over the past several years as premiums surged, standard security requirements constantly expanded and carriers found it difficult to measure cyber risk. A steady rise in ransomware attacks that led to business disruptions and stolen data concerns only added to the challenges.
As an increasing number of organizations of all sizes adopt cyber insurance policies, carriers are becoming more and more involved in incident response (IR). While there are pros and cons to this trend, some security experts and enterprises worry the insurers may be overstepping boundaries.
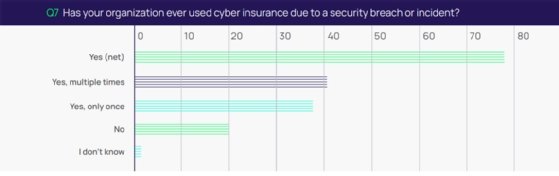
Privileged access management vendor Delinea published a report in November titled "Cyber Insurance – If you get it, be ready to use it" that surveyed more than 300 IT security professionals located across the U.S. The report revealed that almost 80% of respondents have used their cyber insurance policies, and half of those have used it multiple times.
However, it also showed that some policies require organizations to contact their insurance company about a ransomware attack prior to anyone else, including law enforcement and IR teams.
"Many companies worry that insurance companies have too much influence over ransomware response," the report read. "Based on the data in this survey, some carriers want to be involved in the decision whether to pay the ransom."
Joseph Carson, chief security scientist and advisory CISO at Delinea, has seen attackers demand multi-million-dollar ransoms from organizations and hundreds of thousands of dollars from individuals.
"That's why insurers are stepping in, saying they want to take the cheapest path," Carson said.
While cyber insurance carriers play a significant role in ransomware response, more than 50% of IT professionals surveyed by Delinea said their policies don't cover costs related to ransomware attacks, such as data recovery.
Insurance carriers' role in cybersecurity has been a point of contention for some time. Even as the cyber insurance market was in its infancy several years ago, infosec professionals and vendors expressed frustrations with the growing influence carriers exerted during IR engagements. As the cyber insurance market grew rapidly over the last five years, that influence has become more entrenched, according to experts.
Ransomware response
As the cyber insurance market has expanded and evolved in recent years, carriers have implemented stricter policy requirements for their clients to control costs and rising loss ratios, which are costs and claims payments divided by total premiums. While carriers have long required organizations to adopt basic security best practices such as multifactor authentication, some providers have raised prices -- and even rejected coverage -- for organizations using specific technologies that, for example, have experienced frequent zero-day attacks.
That trend has continued in other aspects of cyber insurance policies. Carson was surprised to see some that insurance companies have added clauses around notification requirements, a newer trend that was observed by his industry peers as well. Because time is so important in IR cases, prompt notification is beneficial. Even if authorities can't seize the ransom payment or trace the wallet back to the ransomware group, it provides data for defending against future threat activity.
"If it's part of the process to notify the insurer, it's okay. But putting clauses that, otherwise, you're opting out if you notify in any other order could present problems because incident reporting and getting as much intelligence as possible is so critical," Carson said.
Kurtis Minder, CEO and co-founder of cybersecurity reconnaissance vendor GroupSense, similarly said insurance policies are dictating how clients behave during incidents. If enterprises do things in the wrong order -- such as engaging IR firms first -- it can put the reimbursement at risk.
Another area Carson highlighted where insurers are becoming increasingly involved in is with ransomware payment clauses. Recovering and restoring from backups, if the enterprise has a good program in place, can be more costly than the demand. The monetary demands are significantly increasing, Carson said.
In some ransom demand cases, insurers will issue a check to the cryptocurrency broker. Other times the victim will pay up front and submit a reimbursement request. The former applies to larger enterprises usually paying in the millions, Minder said, while smaller, regional enterprises will have to come up with the front capital and get reimbursed.
Ransomware remains a growing problem for all size of enterprises as threat actors leverage older, known vulnerabilities and take advantage of unpatched environments.
Minder believes cyber insurance carriers often influence a company's decision to pay the ransom, mainly because the money is not coming out of the victim's pocket. That, combined with attacker's extortion threats regarding exposure of sensitive data, increases the chances of an enterprise paying the ransom.
Minder has observed threat actors only becoming more ruthless in exploiting enterprises. For example, earlier this month the Alphv ransomware gang leaked photos of cancer patients after Lehigh Valley Health Network declined to pay the ransom.
"I've been in cases where I'm certain I could negotiate the threat actor much lower, but the insurance company steps in and says, 'Nope, that's good enough,'" Minder said. "We understand you want to get the customer up and running, and there's operational interruption that could drive that. But in some of these cases, that wasn't true. It was more extortion driven. So now we're, like, overpaying the bad guys."
On the other hand, Delinea's report showed that 70% of respondents said their policies don't cover ransomware payments at all. Kevin McGowan, strategic vice president at cyber insurance vendor Resilience, said the insurer is typically not going to say whether an organization should pay nor if they should report the incident to the authorities. It is ultimately up to the enterprise, he said. After an attack, he said it's important to notify law enforcement and the cyber insurance carrier immediately.
Panels present additional concerns
To deter organizations from paying ransoms, which are requested in cryptocurrency, the U.S. Treasury Department issued sanctions against illicit cryptocurrency exchanges as well as individual threat actors and ransomware groups. While Carson said the sanctions have made a positive impact and coincide with a decrease in the number of ransomware victims, insurance carriers and organizations will find loopholes and alternative ways around them.
However, Minder said that in cases he's worked, insurance carriers will show due diligence in checking entities sanctioned by the Office of Foreign Assets Control. But the Treasury Department's list is comprised of names and entities, which threat actors know.
"They know that if their name shows up on this list, verbatim, it's less likely they're going to get paid. So what they do is change their name," Minder said.
Minder's primary concern over insurance carrier's role in IR is the panels, or list of approved vendors that clients can use, which he described as arbitrary. That can include forensics teams, privacy law firms and IR providers. He questioned whether the participants and people on those panels are there because they're effective or because their rates are lower. Based on his involvement in a handful of IR cases with different insurance companies, Minder said there doesn't appear to be a litmus test for the panel.
Carson also observed carriers bringing their own team of experts, including ransomware negotiators, to ensure the incident has the cheapest impact to the insurance company. Ray Komar, vice president of tech and cloud alliances at Tenable, said one of the first calls enterprises make after an incident is to the insurance company. Being on those panels is important as an IR provider.
Komar also emphasized how the cyber insurance market is driven by ransomware. Last month, Tenable launched a new cyber insurance tool as part of its Vulnerability Management platform to help customers get insured. The report summarizes exposure information relevant to cyber insurance carriers and is intended to address the long list of standard requirements.
The new tool represents Tenable's perspective on cyber insurance, which should increasingly focus on preventative measures rather than post-attack fallout. "We feel there's been a disproportionate amount of attention on the IR side of cyber insurance," Komar said. "It's an important facet, but it's better to get in front of it."
Another way to get in front is to go back to the basics. Minder said enterprises should be focusing on basic cyber hygiene, such as implementing multifactor authentication and having good backups, which cyber insurance is positively influencing.
"I think it's actually helping to bring the number of attacks down just because people are being forced to use good cyber practice in the organization, especially small and medium-sized business who didn't really pay attention. Now their insurance company is forcing them to do it," Minder said.
While infosec experts agree cyber insurance is improving security postures with the growing list of standard requirements, Carson said many insurers want to be first with the best policy and may not be evaluating properly.
"You're getting this competitive side. But it's important that there's a baseline you meet to be insurable," he said.
McGowan acknowledged a volatility has grown within the cyber insurance market over the last couple of years, which he said correlated with ransomware activity. Most enterprises are doing the best they can to implement strong controls. But as losses mounted, especially due to ransomware, insurance rates increased.
"What we are trying to do -- and [what] other carriers are trying to do better -- is connect insurance policies to data in a better way," McGowan said. "It's about sharing information and not looking at the insurer as an adversary but as a partner."
Carson echoed the sentiment that cyber insurance is a way to bolster defenses. But based on the Delinea report findings, he was concerned that organizations are viewing policies as an alternative to their enterprise security strategies. It should be an addition, he said, not an substitute.






