
Getty Images/iStockphoto
Dragos: ICS/OT ransomware attacks up 87%
Ransomware attacks against industrial organizations remains a growing problem, according to ICS/OT vendor Dragos' new 'Year in Review 2022' report.
Ransomware attacks against industrial organizations are up 87%, according to new research from Dragos' "ICS/OT Cybersecurity Year in Review 2022" report published Tuesday.
Dragos' "Year in Review" series is an annual report in which the industrial cybersecurity vendor reveals the threats and trends in the operational technology (OT) space. Because OT is a broad category that encompasses the hardware and software that enables critical and typically industrial processes, it can include manufacturing, healthcare, municipal water and power, oil and gas, and much more.
Among the most significant findings in the report were those involving ransomware. Dragos tracked 605 ransomware attacks against industrial organizations in 2022 -- an 87% increase from the prior year. Dragos gave multiple reasons for the trend in its report, including political tensions such as Russia's invasion of Ukraine, and "the continued growth of ransomware as a service (RaaS)."
The vendor also found 35% more ransomware groups had attacked ICS/OT organizations in 2022 than 2021. Asked why this might be occurring, Dragos director of intelligence content Thomas Winston pointed to the constant metamorphosis of ransomware gangs.
"Based on the information Dragos has at this moment, the apparent reason [for the increase] is the shutting down and then rebranding of ransomware groups, and the distribution of RaaS services, which lowers the barrier to entry for would-be ransomware adversaries," he told TechTarget Editorial.
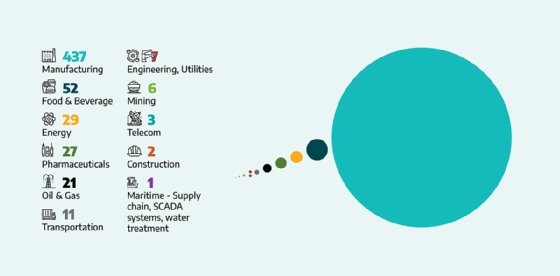
The report provided multiple examples of attack campaigns affecting the industrial sector. Dragos said it identified several Conti victims in the automotive industry in 2022, as well as multiple LockBit variants affecting victims in sectors like construction, electric and manufacturing.
The Year in Review report also included statistics about the organizations Dragos engaged with last year. The ICS/OT security vendor said that among these customers, 80% had limited visibility into their OT environments; 50% of engagements identified problems with network segmentation; and 53% had undisclosed or uncontrolled external connections to the OT environment.
These three issues are compounded by an increase in identified vulnerabilities. Dragos investigated 27% more flaws in 2022 than 2021. In addition, 20% of investigated flaws resided deep within the OT environment, and 12.5% of advisories were "extremely critical."
Dragos furthermore identified issues with the way these vulnerabilities were reported. Of the 465 advisories Dragos analyzed, 34% contained errors of some kind, while 14.9% of the 2,170 CVEs the vendor analyzed had CVSS scoring errors. Outside of the errors, 30% of advisories contained no patch whatsoever, and 75% contained no vendor mitigations.
"This advice is critical for network defenders if they are unable to apply any available patches or if no patch was provided," the report read. "Dragos provided mitigations for the 53% of advisories that contained no mitigation from either vendors or ICS-CERT."
However, the report noted that vendors and CERTs have improved at generating security advisories for ICS and OT flaws. Dragos said that although vendors aren't fully providing mitigations themselves, "they are on the right path."
OT powers and regulates critical infrastructure technology, but as a dedicated cybersecurity category it's only about a decade old. As such, the OT security landscape today is defined by its significant growth as well as major consequences.
Alexander Culafi is a writer, journalist and podcaster based in Boston.






