
Getty Images/iStockphoto
Many Exchange servers still vulnerable to ProxyNotShell flaw
A new exploit chain using one of the ProxyNotShell vulnerabilities has bypassed Microsoft's URL Rewrite mitigations from September and put Exchange servers at risk.
Approximately 60,000 IP addresses with internet-facing Exchange Server instances are still vulnerable to ProxyNotShell flaw CVE-2022-41082, according to cybersecurity nonprofit Shadowserver Foundation.
ProxyNotShell refers to a pair of Exchange Server zero-day vulnerabilities first disclosed in September that were chained together by threat actors in a series of targeted attacks. One flaw, CVE-2022-41040, is a server-side request forgery flaw, and the other, CVE-2022-41082, is a remote code execution bug. The name ProxyNotShell is a reference to ProxyShell, a now-infamous series of flaws disclosed in 2021.
Microsoft did not patch ProxyNotShell until its November Patch Tuesday release. Until then, the company urged customers to mitigate the vulnerabilities by applying URL Rewrite instructions for the Autodiscover endpoint at the center of the exploit chain.
However, CrowdStrike published a blog post last month revealing that a new exploit chain, referred to as "OWASSRF," bypassed Microsoft's URL Rewrite mitigations. OWASSRF combines ProxyNotShell bug CVE-2022-41082 with elevation of privilege flaw CVE-2022-41080, and it has been used in several Play ransomware attacks in recent weeks.
CrowdStrike urged organizations to apply the November Patch Tuesday fix, which addresses the new chain. OWASSRF is considered particularly dangerous because it affects organizations that applied mitigations under the impression that patching ProxyNotShell was not necessary. CrowdStrike and Rapid7 have both observed an increase in Exchange Server compromises where OWASSRF was the suspected cause.
Shadowserver, a cybersecurity nonprofit dedicated to data collection and analysis, has been scanning for IP addresses with instances of Microsoft Exchange Server that are likely vulnerable to CVE-2022-41082. On Dec. 21, the day after CrowdStrike's research went live, Shadowserver found 83,946 vulnerable IP addresses. As of Jan. 2, that number dropped to 60,865.
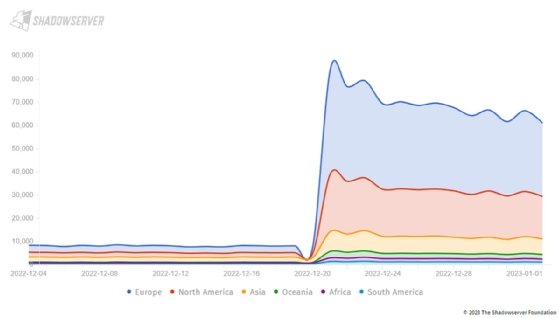
Shadowserver CEO Piotr Kijewski told TechTarget Editorial that compared with other recent Exchange Server security issues, the new exploit chain has not reached similar awareness levels.
"My personal take is that there is a bit less of awareness of this current issue, and hence the patching is slower," he said. "Previous messaging on this issue focused a lot on mitigations initially, which as it turns out now were insufficient. The latest patches from [Microsoft] on Nov. 8 were not hyped as much as they should have been."
Kijewski added that due to the way Shadowserver's Exchange scanner is set up, it is unlikely that many of the tracked vulnerable Exchange instances are honeypots set up by researchers.
"The Exchange scan is built from three scans and four processing scripts that extract different vulnerabilities and information," he said. "The first [scan] is a HEAD request and the other two are GET requests that we expect to have to follow redirects on. So these would have to be real instances set up as honeypots for us to collect information on them, which means that by definition we are likely to pick up less of them."
Microsoft did not respond to TechTarget Editorial's request for comment.
Alexander Culafi is a writer, journalist and podcaster based in Boston.






