
Cisco Talos: Destructive malware, supply chain attacks rising
At RSA Conference 2022, Cisco Talos discussed how adversaries have evolved and changed their tactics, leading to major shifts in the threat landscape.
The use of destructive malware is becoming incredibly common and will likely continue for the foreseeable future, Cisco Talos warned during RSA Conference 2022.
Nick Biasini, head of outreach at Cisco Talos, and Pierre Cadieux, senior manager of incident response at Cisco Talos, hosted a session Tuesday that detailed the current threat landscape and provided actionable steps for enterprises to defend themselves. Key takeaways included the heightened importance of securing credentials and an increase in supply chain threats, destructive attacks and zero-day exploitation.
To convey how dangerous adversaries have become, Biasini emphasized new tactics developed over the years including the targeting of critical infrastructure, dropping false flags and a shift from covert operations to driving public attention.
Weaponized exploit markets are also becoming more common in use, and Cadieux expressed concern over how few organizations patch well. Even more alarming is an increase in actors who can deploy damaging attacks with destructive malware.
"Every major country out there has some sort of offensive capability, and instead of having to develop those exploits in-house, they are able to buy them," Biasini said during the session. "Anyone with a deep pocket has the ability to launch very sophisticated attacks."
The breadth of adversaries has increased as well contributing to software supply chain risks. The technology supply chain, which he described as more of a web, is becoming a bigger and bigger problem. There's an array of avenues for adversaries to take advantage of, including open source libraries and vendors exchanging data.
Biasini referenced CCleaner, a utility program that was compromised by threat actors in 2017, as a prime example. Attackers injected malicious code into CCleaner, which ended up being installed on millions of systems. It highlighted a willingness, he said, for actors to compromise more than 3 million systems, just to gain a foothold into 50 targets.
"This gives you a clear idea of the challenges we face as enterprises from these types of sophisticated actors," Biasini said during the session.
Threat actors adapt
As work environments changed, attackers have developed new methods to gain access such as designing malware to compromise at-home routers. Cyclops Blink is one recent example that was attributed to Russia and infected over 500,000 devices. Biasini said at-home routers provide a foothold for actors to deploy a variety of attacks, and detection capabilities for home networks are limited, which adds to the problem.
As defenders, Biasini said it's challenging to differentiate between a home user logging in legitimately and an actor who's been sitting on a router and is also using their credentials to log in.
"At this point for enterprises, you should start treating home Wi-Fi like you would public Wi-Fi because at this point, there's no difference between the network at your house and the network you're connecting to at your local coffeehouse," he said during the session.
Another attractive target for actors is Security Assertion Markup Language (SAML) tokens, a vector present during the SolarWinds supply chain attack. They allow access to both on-premises and cloud environments, but more importantly, they can be used to bypass multifactor authentication (MFA), a security feature repeatedly pushed by the infosec community.
"What does that tell you? It tells you MFA works," Biasini said during the session. "It actually does slow down their progression, which is why we see them try to abuse trust to gain access to resources."
Zero-day exploitation has also caused broader damage. For example, the Kaseya supply chain attack saw REvil ransomware actors use the vendor's software to gain access to managed service providers (MSPs) and then infected their customers, which were smaller businesses with limited resources. Biasini described it as a services-based supply chain attack.
"If you told me 15 years ago that a criminal organization would use multiple zero-days to launch a supply chain attack against MSP customers, I would have laughed," Biasini said during the session. "Yet, here we are with organizations that are funded almost as well as nation-states today."
Another fear Biasini expressed was nation-states' desire to copy one another. One example he provided was the DNS-hijacking campaign Cisco dubbed Sea Turtle in 2017. He warned that if another less careful or less sophisticated nation-state undertook such an attack, the consequences could be more dire.
"There's a real possibility that nation-states could do something that could greatly impact one of the foundations of the internet, causing a lot of unintended consequences. Something that was supposed to be localized could cause ripples," Biasini said.
What can be done?
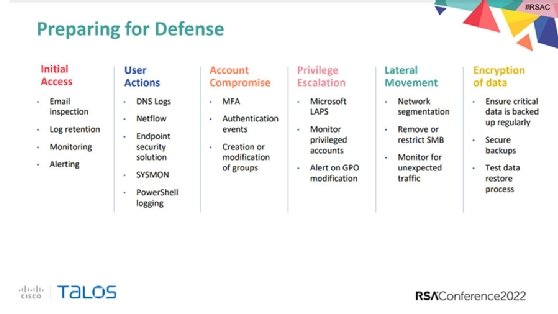
Though MFA has become a target for adversaries, Cisco Talos recommended implementing it for all accounts along with limiting Windows tools to trusted accounts, network segmentation, centralized logging and staying up to date with patching. Cadieux emphasized that a good plan to access logs is critical.
When it comes to compromised credentials and the targeting of an Active Directory (AD) environment, the only thing that can help is password resets, he said. However, it's not something that can be done at the drop of a hat.
"If you haven't done it in a large environment, you should consider how you'd do that and how you'd test it," Cadieux said during the session. "Knowing this will likely be your future if you have an AD environment, you should at least have an approach ready."
Additionally, enterprises need to understand how their backup infrastructure works. It is critical in the event of a ransomware attack, Cadieux warned.
"We see adversaries potentially target backup infrastructure every time," he said. "You have to expect that."






