
Verizon DBIR: Ransomware dominated threat landscape in 2021
Though ransomware became an increasingly large threat to enterprises last year, Verizon's Data Breach Investigations Report found the model may not be as profitable as expected.
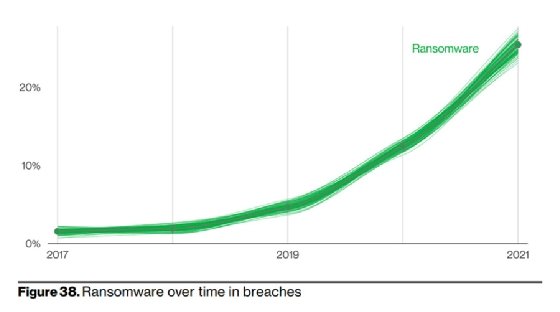
Nearly 25% of all data breaches examined in the 2022 Verizon Data Breach Investigations Report 2022 involved ransomware, an ominous sign for enterprises.
For the fifth consecutive year, ransomware continued its upward trajectory in the annual Data Breach Investigations Report (DBIR), which analyzed 23,896 incidents in 2021 with over 5,000 confirmed data breaches from an array of organizations, sectors and regions. Now in its 15th year, the DBIR did not include ransomware until 2013, when sufficient data emerged to grant concern. In the relatively short time since its inclusion, ransomware activity has steadily increased as a major threat.
Last year was no different and marked a significant increase year over year, which highlights another problem. Despite ongoing warnings and alerts, ransomware gangs continue to ravage enterprises and public sector entities.
"This year ransomware has continued its upward trend with an almost 13% increase -- a rise as big as the last five years combined (for a total of 25% this year)," the 2022 Verizon DBIR read.
That number excludes extortion groups like Lapsus$ that steal and ransom confidential data but do not deploy actual ransomware, Alex Pinto, team manager at Verizon DBIR, told SearchSecurity.
Whether data is exposed or not, the real damage from ransomware comes from the disruption of victims' business operations. Pinto said ransomware has evolved into an ideal attack for cybercriminals looking to earn illicit revenue.
"You're just selling back to the people who you stole from in the first place," he said. "They are the perfect customer for you, and this is what makes it so appealing as a vector of growth in the way that financially motivated breaches play out in the threat landscape."
The report emphasized that on its own, ransomware is simply a way to profit off a compromised organization.
"Ransomware operators have no need to look for data of specific value, e.g. credit cards or banking information. They only need to interrupt the organizations' critical functions by encrypting their data," the DBIR read.
Threat vectors and patterns
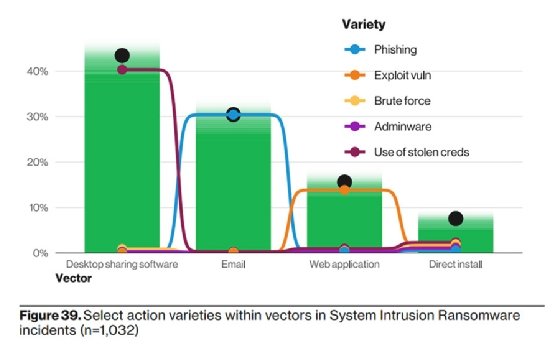
The Verizon DBIR team determined that attackers utilized stolen credentials, phishing, exploiting vulnerabilities and botnets to compromise an enterprise network, and all four paths enabled ransomware attacks. Though the ransomware strains and groups causing that damage varied, the DBIR noted the vectors were less diverse. Desktop sharing software, which was a concern in last year's report as well, accounted for 40% of ransomware incidents, while 35% involved the use of email.
To make matters worse, ransomware was present in almost 70% of malware breaches, according to the report.
Malware is one of seven actions highlighted in the report that represent the steps leading up to an incident or breach and are broken down by variety and vector. Ransomware was one of the three most common actions along with phishing and downloaders, according to the report. During a ransomware attack, the most common malware included droppers, which the report noted aligns with email being a popular initial access point.
"If attackers have credentialed remote access, they can leverage that directly. Otherwise they must make their own remote access by emailing either malicious links or attachments," the DBIR read.
Ransomware played a role in third-party breaches, where it accounted for one of five top action varieties. Additionally, it was the number one threat to "very small businesses," a new category featured in the report. The DBIR team included the section to assist businesses that lack the security resources of large corporations. Ransomware accounted for nearly 80% of the attacks against very small businesses.
"Especially those in these specific small companies, which are less than 10 employees, they have been severely hit by ransomware," Pinto said.
The ransomware economy
Another novel addition to the 2022 Verizon DBIR was an economic analysis from the threat actors' perspective. The DBIR team combined many factors including phishing test success rate data, criminal forum data and ransomware payment data to conduct simulations. It also compared small-time cybercriminals with large criminal enterprises and accounted for outsourced labor, the cost of access and lateral movement.
The majority of access did not even cost a dollar, according to the report. That is in part due to the commonly used and cost-efficient initial access point mentioned earlier: email.
After 300 simulated ransomware scenarios based on dark web forum data, the DBIR team determined the actors made over $600,000, though the median profit was just over $100. Sixty percent of the simulated incidents made no profit.
Puzzled by the findings, which varied greatly, the DBIR team broadened its scope to 500 ransomware actors. Out of the new pool, 1.4% showed a loss.
"However, the median profit after 300 incidents was $178,465, with the top simulated earner making $3,572,211," the DBIR read. "The takeaway is that ransomware is more of a lottery than a business."
That is in stark contrast to conventional wisdom about ransomware-as-a-service outfits; threat analysts and researchers have found some major RaaS groups have made tens of millions of dollars in just a few years of existence. Equipped with customer service representatives and communication support, many ransomware groups act like legitimate businesses. However, the DBIR analysis reveals that business may not always be as lucrative as advertised.
It also revealed important lessons for enterprises.
"If an actor has to pay for services to break in rather than just an access product, you've made yourself much less of a target," the DBIR read. "Use antivirus to remove bots, implement patching, filtering, and asset management to prevent exposed vulnerabilities and standardize two-factor authentication and password managers to minimize credential exposure."
Addressing email, which is the largest vector according to the Verizon DBIR, is also essential in preventing ransomware attacks. The DBIR team recommended locking down exposed infrastructure and focusing on vectors like Remote Desktop Protocol (RDP) and email, as well as conducting email training to heighten employee awareness.
The risks associated with RDPs as a common infection vector for ransomware continue into 2022. They were included in a recent joint cybersecurity advisory that recommended enforcing multifactor authentication to secure remote desktop access.







