
Getty Images/iStockphoto
Check Point: Ransomware attacks lasted 9.9 days in 2021
Check Point Research and Kovrr found ransomware attack victims paid out 89% of the ransom demand on average in 2019. The figure dropped to 27% in 2020 before rising to 49% in 2021.
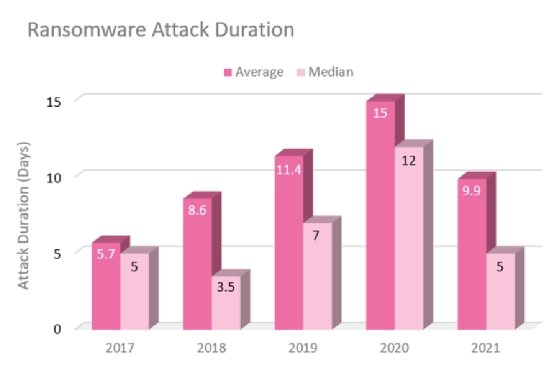
It took organizations an average of 9.9 days last year to resume business operations following ransomware attacks, according to a Check Point Research post published Thursday.
Check Point's post, titled, "Behind the Curtains of the Ransomware Economy -- The Victims and the Cybercriminals," combines data from cyber risk quantification provider Kovrr with insights from the Conti ransomware gang leaks that started in late February.
Among the most notable findings in the report were the data points about the length of ransomware attacks and the financial impact on victims. According to Kovrr data, the average length of a ransomware attack, which was defined as the amount of time between the start of an attack and the victim's normal business operations resuming, was 5.7 days. That length of time gradually rose to a peak of 15 days by 2020, before dropping to 9.9 days in 2021.
One potential reason for 2020's peak and 2021's drop off may have to do with the rise of "double extortion" ransomware, in which the victim is extorted both for the decryption of their encrypted files and by the threat of having their data leaked.
"We believe that 2020's peak and the decline in 2021 are mainly due to the rise in double-extortion attacks that started in 2020," the report read. "These attacks caught organizations off guard and resulted in long negotiations between attackers and victims. As this trend gained popularity and continued into 2021, organizations established better response plans to mitigate ransomware events, thus lowering the duration of an attack."
Kovrr's data also highlighted the importance of ransomware negotiations, as the ratio of ransom demand to ransom payment dropped significantly between 2019 and the two following years. In 2019, victims paid about 89% of the ransom demand. In 2020, ransom payments dropped to about 27%, before rising again in 2021 to 49%.
Check Point argued that two reasons for this are that organizations are implementing stronger ransomware response plans and that larger "big game" targets were being targeted more in 2020 and 2021. These larger targets allow for wider ranges of negotiations, and moreover, these targets likely have greater resources to negotiate than smaller ransomware victims.
The jump between 2020 and 2021 was likely due to "the fact that ransomware actors have become more efficient at calculating their extortion demands," Check Point said.
As for the financial impact of ransomware attacks, Kovrr provided several examples of large companies that were attacked, how much insurance paid, and what the impact against the organization was. An unnamed prepackaged software that was hit by NotPetya ransomware in June 2017 suffered $68 million in lost revenue, $24 million in response costs and $50 million in other losses; the insurance payment itself was $30 million.
Check Point's report also covers multiple angles of the inner workings of the Conti ransomware gang, a prolific ransomware actor that was first tracked in 2020. The leaks referenced in Check Point's report came from an alleged researcher with sympathies to Ukraine who leaked massive amounts of data after Conti proclaimed support for Russia shortly following the nation's invasion of Ukraine. Leaked data included internal chat logs, Conti ransomware source code, internal documentation such as training materials and more.
From these leaks, Check Point found that Conti uses different formulations, often based on an organization's revenue, in its initial demands depending on the organization. When it does make a demand, Conti will offer discounts if the victim pays within a matter of days. If the victim doesn't pay, Conti first threatens to leak a small amount of data; after that point, either an agreement is reached or all the victim's data is dumped.
Akamai, which also analyzed the data, weighed in earlier this month to say Conti operated on a low-tech but effective ransomware model.
The sheer quantity of data found in the Conti leaks provides a rare opportunity to see how a gang operates from the inside. Sergey Shykevich, threat intelligence group manager at Check Point Software Technologies, called the leak "especially useful."
"The industry had some information about the size and the robustness of Conti group, but the leaks allowed us to understand a lot of tactical day-to-day details about the group," he told SearchSecurity. "The leaks were especially useful to understand how the members of this group think and what are their considerations in each and every stage of their ransomware operation, as well as how different parts of this group cooperate among themselves to create a robust ransomware operation."
He continued, "Not every ransomware group operates the way Conti operates, but Conti is a good prototype for the major Eastern European ransomware groups."
Alexander Culafi is a writer, journalist and podcaster based in Boston.





