Getty Images/iStockphoto
FBI: Ransomware hit 649 critical infrastructure entities in 2021
The FBI's Internet Crime Complaint Center found ransomware was a top threat to critical infrastructure security in 2021, hitting a wide range of organizations.
U.S. critical infrastructure sectors suffered a wave of ransomware attacks in 2021, according to new data collected by the FBI's Internet Crime Complaint Center.
The FBI's annual Internet Crime Report published Tuesday revealed the FBI's top reported incidents to its Internet Crime Complaint Center (IC3) over the last year, which included ransomware, business email compromise (BEC) and the use of illicit cryptocurrency. While all three exploits yielded high returns for threat actors, ransomware posed the biggest threat to critical infrastructure organizations, with an alarming 649 complaints.
The FBI said it began tracking reported ransomware incidents involving critical sectors in June. Between May and June, two notable ransomware attacks occurred; one against Colonial Pipeline Co., which affected the U.S. gas supply, and another against meat processing company JBS Foods.
The report highlighted 16 sectors overall "whose assets, systems and networks, whether physical or virtual, are considered so vital to the United States that their incapacitation or destruction would have a debilitating effect" on public health, safety and other critical elements.
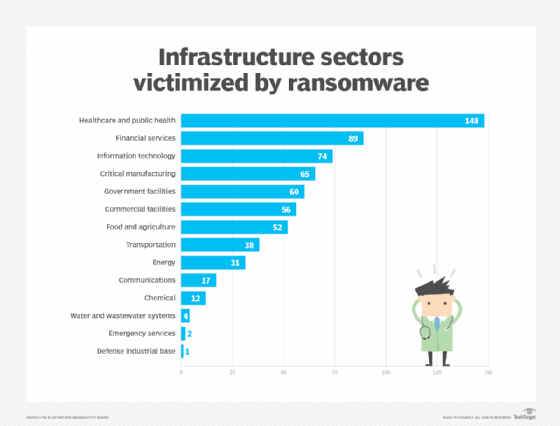
"Of the 16 critical infrastructure sectors, IC3 reporting indicated 14 sectors had at least one member that fell victim to a ransomware attack in 2021," the report said.
Healthcare and public health topped the list, with 148 reported ransomware incidents. Financial services came in second, suffering 89 attacks. The IT sector also took a hit, with 74 victims affected by ransomware. Critical manufacturing wasn't far behind, with 65 reported incidents. Similar figures were found in Dragos' Year in Review 2021 report, which cited mounting concern over ransomware attacks against the manufacturing sector.
Phishing emails, remote desktop protocol (RDP) exploitation and the exploitation of software vulnerabilities "remained the top three vectors for initial intrusions," according to the IC3. The report also noted a connection among popular vectors and the increased use of remote work and schooling.
Three primary ransomware-as-a-service gangs were responsible for the majority of the attacks: Conti, LockBit and REvil. Each ransomware group appeared to have preferred targets, according to the IC3 report.
"Conti most frequently victimized the critical manufacturing, commercial facilities and food and agriculture sectors. LockBit most frequently victimized the government facilities, healthcare and public health and financial services sectors. REvil/Sodinokobi most frequently victimized the financial services, information technology and healthcare and public health sectors," the report said.
BlackBerry researchers also observed a strong link between ransomware and attacks on critical infrastructures last year. In its 2022 Threat Report, Conti was highlighted for its attacks against manufacturing and healthcare service providers in the U.S., as well as Japan and Europe.
REvil, which was behind the JBS Foods attack, was shut down this year but Conti and LockBit remain high threats to date, as do ransomware attacks against critical infrastructure sectors.
"The IC3 anticipates an increase in critical infrastructure victimization in 2022," the report said.
Last week, President Joe Biden tightened transparency timelines for cyber attacks against critical industries. He signed a federal law that requires critical infrastructure entities to report a cyber attack in 72 hours and a ransom payment in 24.
Though critical infrastructure entities suffered substantial losses from ransomware attacks in 2021 – more than $49.2 million, according to the IC3 report -- phishing was the top cybercrime observed by the FBI in 2021. The report cited an increase over the last five years. During a panel at the SecureWorld Boston conference earlier this month, Stephen Dougherty, financial fraud investigator for the U.S. Secret Service, said even "sophisticated victims are falling for phishing attacks."
While data breaches experienced a slight increase between 2020 and 2021, extortion decreased, according to the report. When broken down by victim loss, BEC was the main culprit, with more than $2 billion in losses. One reason was attributed to BEC attacks evolving to use "virtual meeting platforms to hack emails and spoof business leaders' credentials to initiate fraudulent wire transfers." The FBI found those transfers were "often immediately transferred to cryptocurrency wallets and quickly dispersed, making recovery efforts more difficult."
Similarly, Dougherty, who specializes in BEC crime, said funds are going directly to cryptocurrency, and threat actors are investing that money right back into their programs. During the panel, he estimated that the numbers from BEC attacks in 2021 would be "alarming." The IC3 report now confirms that.
"They're getting better phishing kits, they're getting more sophisticated, they're getting better money launderers," he said during the panel. "They're even tailoring their attacks and recruiting specific people to make their attacks better. For instance, say if they're attacking a German company and they see a bunch of emails in German that they've hacked, they'll recruit a German speaker to write a well-crafted, well-thought-out email to launch their BEC attacks."
For ransomware attacks, the IC3 offered immediate action steps including deploying system updates, implementing user training and phishing exercises to raise awareness, and securing and monitoring RDP.