
Dragos: Ransomware topped ICS and OT threats in 2021
Whether ICS and OT networks were intentionally targeted or not, ransomware was found to be the No. 1 compromise to industrial organizations last year.
Ransomware posed one of the biggest risks to the industrial sector throughout 2021, according to a new report by Dragos Inc.
The industrial security vendor published its "Year in Review 2021" report Wednesday, which documented cyberthreats, vulnerabilities, assessments and incident response observations for industrial control systems (ICS) and operational technology (OT). The annual review highlighted new trends and threat groups, as well as ongoing issues related to vulnerabilities and patching.
Most notably, Dragos discovered a growing concern over ransomware attacks, particularly against the manufacturing sector.
"During 2021, cyber risk to industrial sectors grew and accelerated largely led by ransomware," the report said.
Three heavily reported attacks included the Colonial Pipeline Co., JBS Foods and a water treatment facility in Oldsmar, Fla. While the Colonial Pipeline attack affected only IT systems, and the FBI seized back a portion of the ransom paid by the company, it represented an increasing threat to ICS and OT environments.
Dragos CEO and co-founder Robert M. Lee addressed the concerns during a media preview of the 2021 report last week. Very rarely, he said, is ransomware going to be a national security event like it was with the Colonial Pipeline, for example. One reason contributing to it gaining national attention was that Colonial "did the right thing, taking down their operations environment proactively," he said, which temporarily halted pipeline operations. While rarely gaining national attention on the level of Colonial Pipeline, such ransomware attacks are becoming common.
While testifying at the Committee on Energy and Commerce of the House of Representatives last year, Lee said he believed a significant number of ransomware cases go unreported. During the media preview, he cast doubt on the idea that ransomware attacks have scaled back in light of recent law enforcement efforts.
"I would disagree with some of the public commentary I've heard from various government officials and others that based on the actions of the administration, we've seen a decrease in ransomware cases. I think there's a decrease in people reporting it to the government, but not a decrease in actual cases," Lee said. "It continues to be a constant theme in our life getting called in."
Attacks by sector
While compiling the report, Dragos found that ransomware became the "number one cause for compromises in the industrial sector." Breaking it down further, manufacturing led the list by a landslide, accounting for 65% of all ransomware attacks. Food and beverage came in second at 11%, and transportation came in a close third with only 8%. The most common manufacturing subsectors affected were metal components, automotive and technology.
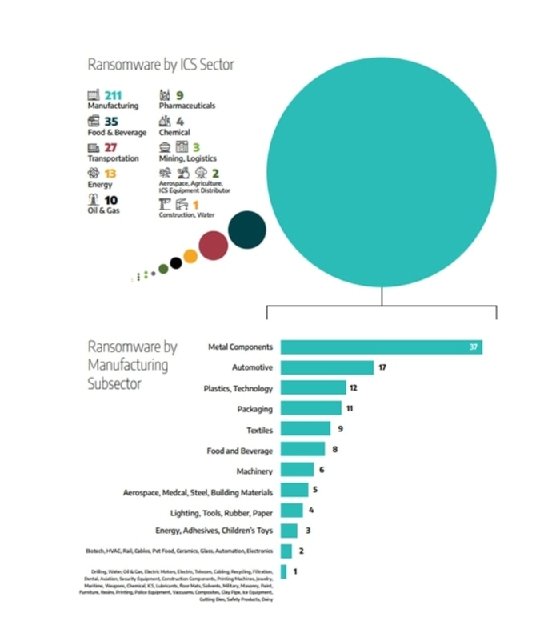
The report referred to 2021 as a pivotal year as the ransomware as a service (RaaS) business model grew rapidly. The use of affiliates increased the number of adversaries, but decreased the bar of sophistication; they could simply purchase the ransomware and necessary software without a high level of knowledge.
Two of those gangs, Conti and LockBit 2.0, were responsible for the majority of 2021 ransomware attacks. Operators behind the variants caused 51% of total attacks, with 70% of their malicious activity targeting manufacturing, according to the report.
"These are troubling trends when paired with the Dragos services team finding that the manufacturing sector is often the least mature in their OT security defenses," the report said.
Though the increase in RaaS contributed to the spike, Dragos said a key factor was the "digital transformation of the industrial sectors and the increased connectivity between IT and OT." The pandemic fueled a digital transformation and a forced rush to remote work, which "increased the overall risk."
Of all the operations environments Dragos investigated, 70% had one or more remote accesses and external connections from their OT systems to third parties such as internet providers, service providers and others.
"I think the larger public is generally unaware of just how connected these plants are, and sometimes a lot of the CEOs and boards of these companies are very unaware of how connected they are," Lee said during the media preview.
The reality is that all the different operations and IT networks are connected, Lee said, and most of them are connected to other people's IT networks, like an operations and maintenance provider. To that end, companies protecting their own IT networks may be irrelevant to most of the risks that an OT environment will face.
Those risky connections are one reason Lee said contributed to President Biden's push for further visibility into operations environments. The issue can arise even when OT is not the end target.
"In some cases, adversaries gain access to the IT networks of an organization or its supply chain to get information about the ICS of the target," the report said.
While ransomware groups will directly target OT systems, some infections occurred indirectly when attacking enterprise IT networks. Many of the ransomware cases the vendor dealt with in 2021 involved an attacker compromising the IT network, using the shared credentials and ending up in the operations networks, Lee said. Whether it was intentional or not, it did cause disruption to those environments.
"In 2021, 44% of Dragos services engagements included findings related to shared credentials," the report said.
Threat groups
Dragos identified three new threat groups in 2021, which makes a total of 18 groups the security vendor currently tracks. However, that represents maybe 20% of what's actually out there, according to Lee. The goals of the groups may differ, from looking to steal intellectual property to preparing access or capabilities for future attacks.
"Dragos tracks a number of groups that have targeted industrial networks but do not show the intention of disrupting them; this is much more common in reality than is publicly reported," the report said.
Lee noted that Dragos' assessment may be affected by maturity level, and the groups predominantly featured are based on data from the more mature industries that have the resources to fully investigate incidents. Still, the most newsworthy of the new groups due to its level of sophistication, according to Lee, was one Dragos refers to as Kostovite. Dragos discovered that Kostovite possessed a "high level of operational discipline and network device knowledge," according to slides from Lee's presentation.
Based on Dragos' analysis, Lee said Kostovite was getting long-term access for future disruptive actions. While targeting renewable energy operations in North America and Australia, not only did the group leverage a zero-day vulnerability to gain remote access capabilities, it also specialized in "living off the land," or using legitimate tools and commands to commit intrusions.
"They didn't use anything that wasn't native to that environment. No introduction of malware, no introduction of tools and infrastructure that wasn't already available. Basically, being extraordinarily stealthy," Lee said during the media preview.
To address remote access threats, Dragos said the "most effective control" is multifactor authentication or "alternate controls such as jumphosts with focused monitoring."
The future of ransomware attacks against critical infrastructures is looking dim, according to the report. While Dragos acknowledged that increased law enforcement pressure has forced groups to shift tactics and regroup, the vendor estimated that "more strains with OT/ICS capabilities will be developed in 2022."
Additional concerns
Emerging groups weren't the only threat to ICS and OT. Ongoing problems with patching and vulnerabilities also contributed to the security problem. More than twice as many common vulnerabilities and exposures were published in 2021 than the year before, according to the report. Even when advisories alerted enterprises to an issue, oftentimes there was no mitigation.
"Of the advisories that Dragos tracked in 2021 that did not initially have a patch, 92 percent had no mitigation and 96 percent had no alternate mitigation," the report said. "A full 19 percent had neither a patch nor any mitigation. Dragos also discovered that 65 percent of advisories contained a patch to fix the vulnerability, but no alternative mitigation if patching was not an option."
Even if a patch was available, Lee said patching can be extremely hard to accomplish in these industrial organizations, as it can introduce a lot of risk associated with downtime -- especially in facilities that operate around the clock.
"That's just not really feasible, especially against a risk that we may not fully understand," Lee said during the media preview.
Though the government and regulators increasingly push patching requirements and a focus on addressing flaws, Lee said it is misaligned with the risk and nature of those vulnerabilities. "It's just not really a place we should be focusing in the community," he said.
Instead, he advised defenders to focus on the common tactics, techniques and behaviors of the two primary groups responsible for attacks last year, Conti and LockBit 2.0, and to engage in detection and preventive work against the two strains.
"In my opinion, every single industrial company out there must be doing a tabletop exercise around ransomware inside of the operations environments or already done one, because it's just absolutely prolific and hitting a lot of people," Lee said.







