
Getty Images/iStockphoto
Fallout from REvil arrests shakes up ransomware landscape
Russian authorities recently announced more than a dozen arrests of alleged REvil members, heightening concern among ransomware affiliates on the dark web.
While the arrests of reported REvil members may have reduced ransomware activity, infosec analysts say the impact will likely be short-lived.
Last month, the Russian Federal Security Service (FSB) announced it had "stopped" REvil operations, arrested more than a dozen members and confiscated millions in cash. It's unclear how much these arrests affected REvil operations; the ransomware as a service (RaaS) group was also knocked offline in October following a reported cyber offensive operation led by the U.S. Cyber Command.
But infosec analysts believe the REvil arrests have had an impact. With one of the most notorious gangs -- responsible for high-profile attacks like the one against JBS Foods that resulted in an $11 million ransom -- seemingly out of commission and under scrutiny from Russian law enforcement, the ransomware landscape may be altered, with the fear of potential jail time trickling down to other groups.
Prior to the arrests, REvil gained a reputation for its ego; the operators and their affiliates were unafraid to hit a wide range of targets, from point-of-sale terminals to managed service providers and a foreign currency exchange. It seemed no target was out of reach; even celebrities like Lady Gaga and Madonna were affected after the Russia-based ransomware group hit an entertainment law firm. As highlighted in the report "A History of REvil" by Jon DiMaggio, chief security strategist at Analyst1, one of the group's "targeting choices" even involved supply chain organizations.
That ego is what DiMaggio attributed with REvil's downfall. In the report, he noted that if it had "targeted smaller, non-essential organizations," perhaps its operations would still be intact.
Several factors contributed to that ego, including timing, DiMaggio told SearchSecurity.
Ransomware attacks against enterprises, he said, weren't as common until 2015 or 2016. REvil filled a gap left behind by GandCrab and gained attention in its early attacks from the criminal community, Russian forums and Telegram channels. It was one of the first groups to appear approachable, and they would respond, whether it was to a security researcher or another criminal.
"They just came in with such momentum," DiMaggio said. "So many people were drawn to them because they were doing these big attacks, but then coming out and talking about it, which up to that point really hadn't been done. It almost gave them this celebrity status."
Russian government intentions
Several of the most prolific ransomware gangs have been tied to Russian-speaking threat actors over the years, and some analysts believe the Russian government's crackdown on REvil may not be entirely genuine. Trustwave security researcher Ziv Mador published a blog post last month that examined the fallout on dark web forums. One forum member broached the idea of the operation being "faked or was only a show for international consumption."
"One possible reason for the FSB to fake or not follow through on these arrests could be that it's just trying to placate the U.S. and avoid additional economic sanctions," Mador wrote in the blog.
While DiMaggio said protection from the Russian government didn't lead to REvil's ego, it may have allowed the group to feel safe to operate, even if the group didn't realize it themselves.
"Not having a fear of being arrested allowed them to be approachable and allowed them to feel safe to talk and to do interviews with researchers, so I think that's what made them feel safe to do all this stuff, which then led to their widescale popularity," DiMaggio said.
In his report, DiMaggio examined conversations held on dark web forums over the past several years and found that "ransomware criminals believed they were untouchable." The most common concern he observed was being arrested outside of Russia.
Similarly, Ryan Olson, vice president of threat intelligence for Palo Alto Networks' Unit 42 group, said if groups have been operating in a country without arrests, it gives the impression that the government wouldn't hand them over.
"You probably feel more safe living in that space, where you don't have to worry about extradition or cooperation from law enforcement," Olson said.
Coveware CEO Bill Siegel said Russian law enforcement possibly coddling ransomware gangs is nothing new. There is a long history of these activities being "state ignored" or "state condoned," he said in an email to SearchSecurity.
A Coveware quarterly report referred to the arrests as "an unprecedented action for the Russian government to take."
As for the cybercriminal underworld, DiMaggio said, the biggest accusation against REvil regarding law enforcement was that one of the key operators in the group was cooperating with U.S. authorities after being arrested.
Recently, a feud broke out between LockBit and BlackMatter that appeared to be tied to the REvil arrests and the breakdown of trust they represented. The feud stemmed from accusations of REvil members being undercover law enforcement agents or working with law enforcement directly.
Azim Khodjibaev, senior intelligence analyst at Cisco Talos, told SearchSecurity the final allegation made by LockBit was that the REvil bust was a major political plan between Russia and the U.S. to cooperate more on ransomware disruption. It was allegedly a bone thrown to President Joe Biden by Russian President Vladimir Putin, he said, in order to show or hint at the possibility of cooperation.
Olson cited the types of attacks he observed last year against critical infrastructures, especially against the Colonial Pipeline Company, that may have shifted from a law enforcement focus to a wider government response.
"That changed the game a bit around who needed to talk to who and who was actually engaged in the fight as well," he said.
Impact on ransomware landscape
Despite remaining questions around government motivations, analysts and vendors agree that the reported REvil arrests will have a level of impact.
Following the arrests, Hold Security observed the resignation of key members from various ransomware gangs, including TrickBot and Conti. In a tweet on Friday, the Milwaukee-based security consulting company said its dark web sources reported that "Trickbot gang lost its key members over the past 24 hours. Looks like Russian government actions are driving ransomware gangs to close their doors."
Alex Holden, chief information security officer at Hold Security, told SearchSecurity that several members mentioned moving on to other projects, but a majority of them just said, "I'm done."
"Conti group members were mentioning that if the Russian government ever starts enforcing the law and starts arresting the ransomware groups, they would exit the same business day. That seems to be happening today, and it's absolutely been brewing over the past months," Holden said.
Mador also documented post-arrest dark web chatter and found "a great deal of anxiety and consternation" from forum participants "regarding the FSB arrests and how those actions will impact them in the future."
"From the conversations we've observed, it is clear that these people no longer believe Russia is a safe harbor for their activities," Mador wrote in the blog post. "This level of worry and fear expressed by Dark Web forum members is something we have not seen before."
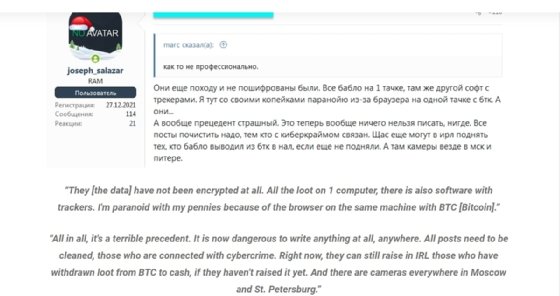
Mador concluded that the long-term impact remains to be seen.
"There is a strong chance that the FSB's activity has a long-term impact on cybercrime, but only if the Russian government follows through and prosecutes those arrested to the full extent of their law. Russian prisons are no walk in the park, and cybercriminals know that," he wrote.
Olson also believes it may be too early to determine the true impact. The Unit 42 team did observe a drop-off in ransomware activity in January, compared with December and November, but nothing significant.
"Arresting one group itself, taking those players off the board doesn't have a big impact as there are so many people launching ransomware attacks, especially with the ransomware-as-a-service model," Olson said.
Since ransomware affiliates are separate from the operators that produce the malware and perform encryption, Olson said, they can simply move to a new RaaS operation if one or two groups are shut down.
Though the arrests of a single group's players may not have a huge impact on the overall ransomware landscape, Siegel said any action that increases the perceived risk of arrest is good.
"Even if these arrests are for show, or the actors don't get our definition of 'justice,' you can't deny that these actions were disruptive and raise the risk profile," he said. "That is a positive."
The Coveware report determined that the arrests decreased the "addressable market of cyber criminals willing and able to execute these attacks, as not all of them are willing to risk jail time or western extradition for the money they earn."
Emsisoft analyst Brett Callow said law enforcement action will have ransomware gangs worried.
"They don't operate in a vacuum and [they] share resources and personnel with other operations. So, when one gang gets compromised and its members arrested, others will invariably wonder whether they may be impacted too," Callow said in an email to SearchSecurity.
But the short-term progress may not last long. If not for the recent escalation at the Ukraine-Russia border, DiMaggio believes the impact made by the REvil arrests would have been greater. Now, he thinks things may get worse.
"I think that not only are they not going to be afraid, I feel like they're going to be encouraged. They'll be encouraged to do attacks like the Colonial Pipeline or to hit financial institutions," he said. "It's really the first time in my career I will say I am really concerned as to what's coming."





