
Getty Images/iStockphoto
SolarMarker malware spread through advanced SEO poisoning
Sophos discovered SolarMarker malware was being distributed through fake SEO-focused topics in Google Groups, as well as malicious PDF files.
A malware actor used their own brand of SEO poisoning to distribute malicious files, according to research published Tuesday by Sophos.
Sophos' latest report concerns SolarMarker, a backdoor and information-stealing malware that was initially detected in late 2020. The malware was typically installed when victims visited a Google search result that has been planted near the top of a search due to threat actors' search engine optimization (SEO) poisoning. These links are designed to get a user to download a fake Windows installer running a PowerShell script.
While SEO poisoning itself is a well-known technique, the effectiveness of this particular approach is one thing that makes this campaign stand out, Sophos said in its report.
"These SEO efforts, which leveraged a combination of Google Groups discussions and deceptive web pages and PDF documents hosted on compromised (usually WordPress) websites, were so effective that the SolarMarker lures were usually at or near the top of search results for phrases the SolarMarker actors targeted," the report read.
SophosLabs senior threat researcher Sean Gallagher, who co-authored the report, said one reason this is unusual is that a significant amount of SEO poisoning comes from "downloader-as-a-service" operations and not individual operators.
"SEO poisoning used to be a lot more common of a technique, but it's been much more rare recently because it's not as effective for targeted attacks," he told SearchSecurity. "Most of the SEO poisoning we see now is part of paid malware distribution services, which we see as a small but pervasive part of information-stealing malware and crypto-fraud malware operations; it's rare for a malware operator to create their own SEO poisoning infrastructure, but it still happens."
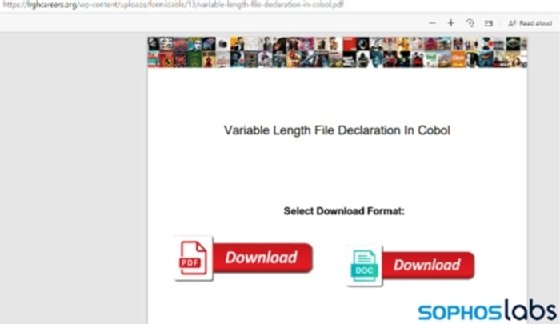
The report touched on three SEO manipulation methods used to distribute SolarMarker. With the first, operators created Google Groups with 500-600 fake posts named after various search terms to make the group appear populated. The post comments would contain PDF links that redirected to malicious .msi installs.
In the second method, SolarMarker actors created a malicious PDF file to appear in search results. The PDF contained links to PDF or document downloads for the search result, which then redirected to a Windows installer.
With the third method, threat actors used deceptive WordPress sites containing HTML code.
"The HTML source for these malicious pages contain link collections for other search terms, all connected to other malicious pages on the same compromised server, as part of the mechanism behind the fraudulent SEO campaign," the report read.
A few of the search terms SolarMarker exploited included "university," "worksheet," "application" and "handbook." One example offered by Sophos included "good-choice-bad-choice-worksheet-for-kids.msi."
The SEO poisoning was so effective, the report added, that some search terms placed links for all three listed methods within the top 10 Google search results.
Sophos, which first detected the SolarMarker SEO poisoning in October, said the campaign appears to have ceased, but the threats still linger.
"There are currently no active SolarMarker-spreading campaigns, as the final download site used by the operators of the campaign was shut down," the report read. "But SolarMarker deployments remain active, and while we've seen a decline in detections of the malware since November of 2021, the malware has not disappeared. It may be just a matter of time before a new campaign using new infrastructure is launched."
Asked whether search engine operators can do more to limit the spread of malicious SEO manipulation, Gallagher answered in the affirmative.
"Google and other search engine operators can do more to tweak algorithms to look for fraudulent sites by looking for link farms of unrelated search terms on a page and demoting its page rank or flagging it as potential spam, and by following links deeper in indexing to look for unrelated file downloads," he said.
Alexander Culafi is a writer, journalist and podcaster based in Boston.







