
More than 1,000 malware packages found in NPM repository
Researchers with WhiteSource were able to find some 1,300 examples of malware hiding under the guise of legitimate JavaScript packages on the NPM repository.
More than 1,000 pieces of malware have been removed from the NPM repository following an investigation into the presence of malicious JavaScript packages.
In a new report published Wednesday, open source security firm WhiteSource said that it ran its Diffend automated scanning tool through the JavaScript repository and found roughly 1,300 libraries that exhibited malware behavior. All of the libraries have since been reported and removed.
Designed to help JavaScript developers keep tabs on updates to their applications' dependencies, the NPM repository functions as a one-stop shop to find and maintain up-to-date libraries.
Unfortunately, according to the WhiteSource team, the repository also allows attackers an opportunity to slip malware into applications without any warning to the developer.
"Even as developers increasingly depend upon JavaScript to create rich online functionalities, the JavaScript ecosystem is under constant attack from malicious actors," the report said.
"A popular attack method is through JavaScript packages installed using various package managers, which are tools that automatically handle the dependencies of a project."
In most cases, the researchers found that the bad libraries were being offered as impersonations of popular legitimate JavaScript packages. The attackers were either copying the name of a specific package or typo-squatting with names that were one or two characters off.
In some cases, the infection attempts were a bit more targeted. The researchers found one particular piece of malware impersonating a library used in-house by food delivery service GrubHub, presumably in an attempt to get the malware onto the work system of one of the company's developers.
Either way, the apparent intent of the attackers was to infect not only the application and its developers, but people who used the application. By getting into a popular application at the developer level, the attackers would be able to potentially infect thousands of enterprises that rely on it, similar to what happened in 2020 with the SolarWinds supply chain attack.
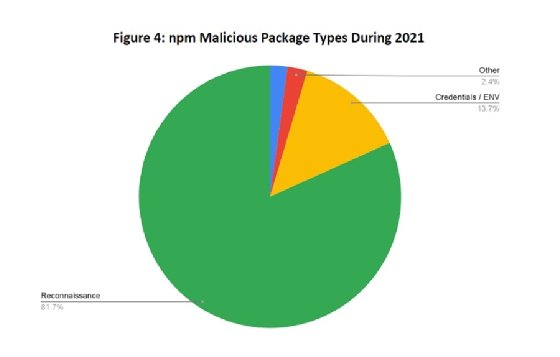
As for the malware itself, the WhiteSource crew found the bad libraries were performing fairly common attacks, such as searching for login credentials or collecting cryptocurrency wallet keys. Other aims include the installation of botnet clients and stealing personal data from victims. According to the report, nearly 14% of the malicious packages discovered were designed to steal sensitive data such as credentials.
Not every one of the 1,300 libraries found was outright malware, however. The researchers noted that some of the samples they collected appeared to be experimental libraries that were being used by security researchers to test applications.
Regardless of the use case, the security firm says that there is little that can be done by administrators or enterprises to prevent such attackers. Rather, the researchers said, it is the developers who need to keep a close eye on their code and make sure that the JavaScript libraries they are using are genuine and trusted.
"Without question," WhiteSource said, "the best defense against malicious activity in NPM packages is a knowledgeable developer community."
In related news, NPM, Inc., a subsidiary of GitHub that maintains the open source software, announced on Tuesday that it is implementing mandatory two-factor authentication for the maintainers of top 100 NPM packages.








