
Getty Images
Emsisoft releases DeadBolt ransomware decryption tool
Emsisoft's DeadBolt ransomware decryption tool fixes broken decryptor keys issued by threat actors, and works only if the victim has paid the ransom and received a key.
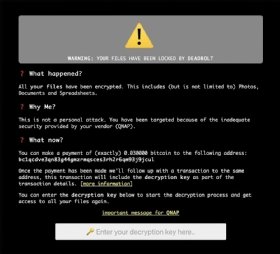
A decryption key is now available for DeadBolt ransomware only a few days after the strain first appeared. The catch, however, is that it requires a decryption key provided by threat actors to work.
The key, released Friday by security vendor Emsisoft, arrives only a few days after the DeadBolt ransomware gang began targeting the customers of QNAP network-attached storage (NAS) devices. Customers affected by the ransomware were told to pay 0.03 bitcoin (approximately $1,150 USD as of this writing) to have their files decrypted.
The ransom note that victims received also included a note for Taiwanese hardware vendor QNAP. According to the note, DeadBolt exploited a zero-day vulnerability that enabled the gang to attack vulnerable QNAP NAS devices exposed to the internet. QNAP was then told to pay 5 bitcoin for vulnerability details or 50 bitcoin for vulnerability details and a mass decryption key.
Whether this decryption tool would have even worked remains in question, as a user on the QNAP NAS community forums claimed to have paid the ransom and received an invalid key. In addition, Emsisoft CTO Fabian Wosar tweeted that a firmware update by QNAP is the cause of decryption issues.
QNAP users who got hit by DeadBolt and paid the ransom are now struggling to decrypt their data because a forced firmware update issued by @QNAP_nas removed the payload that is required for decryption. If you are affected, please use our tool instead. https://t.co/6fvO8ntvrU
— Fabian Wosar (@fwosar) January 30, 2022
Emsisoft's decryption tool allows customers who paid the ransom to implement their decryption key correctly.
Emsisoft threat analyst Brett Callow said that due to DeadBolt's encryption, the only data recovery option for victims (other than resetting the device and applying a backup) is to pay the ransomware gang.
"DeadBolt's encryption seems to be secure, meaning the only way for victims to recover the data is to pay the ransom. Our decryptor is designed to help those who do pay," Callow said. "QNAP's forced update removes the ransomware payload and, without that, the decryptor supplied by the criminals will not work. Our decryptor addresses that problem."
QNAP published a blog last Wednesday with instructions for customers to protect their vulnerable devices.
QNAP has not responded to SearchSecurity's request for comment at press time.
Alexander Culafi is a writer, journalist and podcaster based in Boston.







