
Askhat - stock.adobe.com
Sophos: Log4Shell impact limited, threat remains
Sophos threat researcher Chet Wisniewski detailed the unexpectedly limited impact Log4Shell had on organizations but warned of future exploitation and risks.
While Log4Shell saw limited mass exploitation, the threat remains a concern for the future, according to new research by Sophos.
The flaw, tracked as CVE-2021-44228, was discovered in December in the open source Log4j 2 software package developed by the Apache Software Foundation. It quickly gained attention due to its broad use and inclusion in a high number of software products, cloud services and web applications. More alarmingly, the flaw enabled threat actors to remotely execute malicious code.
Research from several security vendors showed widespread scanning and attempted exploitation of Log4Shell, which was soon leveraged by nation-state actors.
In a blog post Monday, Chet Wisniewski, principal threat researcher at Sophos, said while damage was more limited than anticipated, the flaw will "likely be a target for exploitation for years to come." It could be buried deep in many digital applications and products, he said.
"Sophos believes that the immediate threat of attackers mass exploiting Log4Shell was averted because the severity of the bug united the digital and security communities and galvanized people into action," Wisniewski wrote.
Prior instances of mass exploitation, such as the SolarWinds supply chain attacks and the ProxyLogon vulnerabilities in Microsoft Exchange Server, revealed organizations are slow to patch. They also highlighted the danger of backdoors, which are difficult to discover, and the impact on high-profile targets. This time, it appears enterprise security teams, infosec vendors and cloud services were quicker to act.
Sophos, which tracked the flaw since Dec. 9, reviewed the scans for exposed instances of Log4j and observed attacks. Wisniewski noted patterns in the first few days were "typical" for a newly reported vulnerability. However, there was a significant increase in scanning activity in just one week. Numbers peaked between Dec. 20 and the 23, according to the blog.
"The numbers simply confirm that a great many people, with good or bad intentions, were trying to gauge how vulnerable others were to the threat by looking for the number of potentially exposed systems," he wrote.
The blog post covered Log4Shell's global impact as well. While examining geolocations of callback destinations, Sophos discovered India topped the list, followed by the U.S., Turkey, Brazil and Australia. He attributed it potentially to the high number of bug bounty participants in those countries.
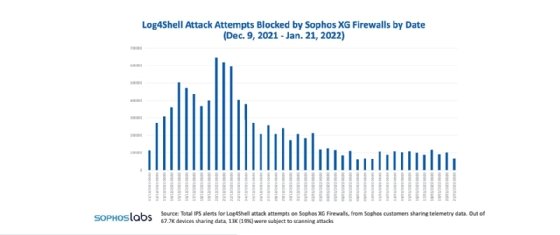
Attacks decline, for now
Beginning in late December though January of this year, Wisniewski said Sophos observed a decline in attack attempts, but those that did occur had a higher likelihood of being "real attacks." Still, Sophos research determined that the "overall number of successful attacks to date remains lower than expected."
He attributed that to two factors. First, Wisniewski said, by January only a handful of Sophos Managed Threat Response Team customers experienced intrusion attempts that used Log4Shell, and a majority were cryptominers.
"Another possible reason for the limited mass exploitation could be the need to customize the attack to each application that includes the vulnerable Apache Log4J code," Wisniewski wrote.
Though fallout appears limited now, it may not bode well for the future. Wisniewski noted that in the past, Sophos observed nation-state threat actors from countries such as Iran and North Korea install backdoors before targets could patch, and then wait months before attacking. Additionally, he said "unknown internally vulnerable systems may never be known or discovered, and these will remain a security risk."
After a review of the scans, patterns and attack detections, Sophos determined that risks associated with the Log4j flaw will "likely continue for years."
"The urgency of identifying where it is used in applications and updating the software with the patch remains as critical as ever," he wrote.






