
Getty Images/iStockphoto
Hive ransomware claims hundreds of victims in 6-month span
Group-IB research has revealed that Hive ransomware-as-a-service operations are back and busier than ever, with a rapidly growing victim list over a short amount of time.
In less than six months, Hive ransomware affiliates have affected hundreds of companies, according to new research by Group-IB.
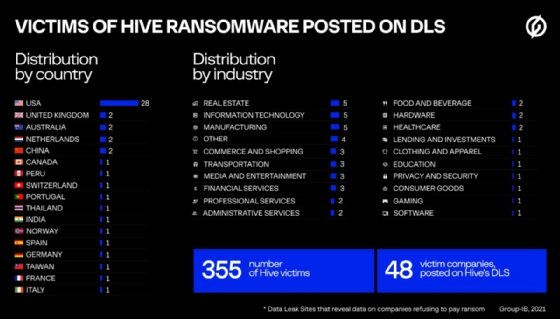
Threat analysts determined that as of mid-October, 355 companies had fallen victim to the ransomware as a service (RaaS) operation, which was first detected in June. A large portion of those victims amounted in just one month. From September to October, the number of victims grew by 72%, from 181 organizations to 312, according to a blog post Sunday by the Singapore-based security vendor.
Oleg Skulkin, head of digital forensics at Group-IB, attributed the rapid increase in such a short time span to the recent shutdown of many RaaS operations. One example is the ransomware gang BlackMatter, which claimed to have ceased operations in early November.
"Ransomware affiliates had to find new opportunities, and Hive's owners provided them with the needed infrastructure," Skulkin said in an email to SearchSecurity.
The threat of Hive ransomware became dire enough that in late August, the FBI issued an alert detailing its indicators of compromise and tactics, techniques and procedures. It encouraged users to review and apply mitigations to prevent falling victim to an attack.
Most of the Hive victims were from the United States, according to the Group-IB blog, with main industries including IT and real estate. One of the first victims that analysts found was Altus Group, which ransomware affiliates attacked in June. The blog also addressed one significant victim outside the U.S. -- MediaMarkt, a European consumer electronics retailer that suffered a Hive ransomware attack in November.
Group-IB analysts attributed the "main factors of the rise of the ransomware empire" to the use of double-extortion tactics and data leak sites (DLS), as well as the "active development of the RaaS program market," both of which apply to Hive.
"Throughout its history, the Hive DLS featured information about 48 companies (including those whose data had been removed from the DLS at some point), which refused to pay the ransom," the blog said.
However, that number represents just a drop in the bucket. Through an API error in Hive's DLS and admin panels, analysts were able to identify the exact number of attacks and estimate the number of companies that paid a ransom to secure their data.
"By Oct. 16, Hive's API held records of 312 companies that most likely fell victim to Hive's operators," the blog said. "It was also discovered that 104 companies out of 312 had negotiated with Hive's operators and their data had not been listed on DLS."
The fact that Hive even used an API to run the DLS and admin panels surprised the intel team. Aside from Hive, the only group that used APIs was Grief, previously known as DoppelPaymer, which was responsible for an attack in November against Manutan, a French office equipment supplier.
Despite the similarity, Skulkin said they have not observed any overlaps with other ransomware groups based on the Hive code analysis. "At the same time, some affiliates may have jumped to this RaaS following the shutdown of other affiliate programs," he said.
Hive's operations
Group-IB's researchers found that Hive affiliates employ several initial compromise methods to pursue victims, including vulnerable remote desktop protocol servers, compromised VPN credentials and phishing emails. The data encryption, according to the blog, is often carried out during nonworking hours or the weekend.
"For each upcoming attack of their affiliates, Hive RaaS owners build a personalized ransomware kit. This kit contains different versions of the ransomware customized for various operating systems," the blog said. That includes Windows, Linux, FreeBSD and ESXi versions 4.0 and higher.
Once a victim is infected, affiliates deliver the ransom note that contains a link to Hive's website with login credentials. There is even a Hive "sales department" that can chat with the victim. If the victim pays the demand, they can download a decryptor with a how-to guide.
"However, some victims claim they experienced problems decrypting their data after receiving the decryptor," the Group-IB blog said.
Aside from the use of APIs, another aspect that sets Hive apart is that the RaaS operation "does not write its metadata directly in the encrypted file." According to the blog, that can complicate the file recovery process "since the operating system will likely rewrite data in the same clusters."
Samples analyzed by Group-IB included communication from a threat actor known as "kkk" who was communicating in Russian. While Skulkin said they can definitely tell Hive operators are Russian-speaking individuals, they do not have any information on the group's location.
Group-IB, originally headquartered in Russia, relocated to Singapore in 2018. In September, its founder and CEO, Ilya Sachkov, was charged with treason and arrested in Moscow. He was accused of "transferring intelligence data to foreign special services," according to an unnamed government source cited by state-owned Russian news agency Tass.







