
Getty Images/iStockphoto
CrowdStrike threat report: Breakout time decreased 67% in 2021
CrowdStrike's latest research shows threat actors have reduced the time it takes for them to move laterally in victim environments, thanks in part to ransomware as a service.
The amount of time it took a threat actor to move laterally across a network decreased by 67% between 2020 and 2021, according to CrowdStrike's latest Threat Hunting Report released Wednesday.
The report, titled "Nowhere to Hide, 2021 Threat Hunting Report: Insights from the Falcon OverWatch Team," is the latest in a series of annual studies published by CrowdStrike's managed threat hunting team. The roughly 70-page report covers all manner of insights related to threat response and represents the period between July 1, 2020 to June 30 of this year.
One of the key statistics in the report involves breakout times -- the time it takes for a threat actor to move laterally from one compromised host to another within the same network.
The average breakout time in the past year was 1 hour 32 minutes, down from 4 hours 37 minutes in 2020. The report adds that "OverWatch found that in 36% of those intrusions, the adversary was able to move laterally to additional hosts in less than 30 minutes." Conversely, CrowdStrike's 2019 report showed an increase in breakout time from 1 hour 58 minutes to 4 hours 37 minutes.
Param Singh, vice president of Falcon OverWatch at CrowdStrike, told SearchSecurity that he sees two reasons why the average breakout time decreased: ransomware as a service and the move to bigger targets. Specifically, ransomware as a service has lowered the barrier for would-be cybercriminals to conduct attacks, and the ecosystem has created more powerful tools and methods to deal with larger networks.
"If you go back five years, ransomware attackers were going after individuals. Today, they are going after big healthcare and other big organizations -- big game hunting. That's one reason," he said. "The other reason is ransomware as a service, because a lot of these tools are now pre-built for them. And they don't need to invest time and money and energy into building these tools. They can buy them off the shelf, which helps them get access into an environment and move very, very quickly."
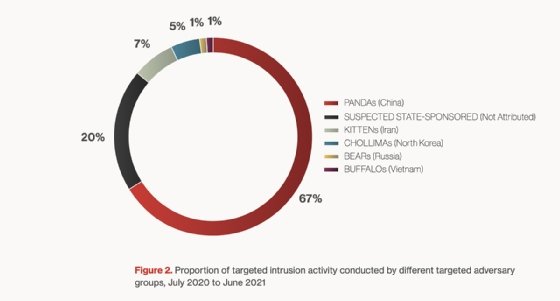
Of the intrusions tracked by the Falcon OverWatch team last year, 75% were financially motivated, 24% were state-sponsored "targeted" intrusions and 1% was attributed to hacktivism.
On the financial front, the Russian cybercrime gang known as Wizard Spider was by far the most prolific adversary group, featuring double the number of intrusions than any other group Falcon OverWatch observed. They're known for using Conti and Ryuk ransomware; the latter was called out in the report as a common ransomware family seen last year.
Russia's representation on the financially motivated cybercrime side contrasts with nation-state intrusions recorded in the past year. Over half of the targeted intrusions were credited to China, with non-attributed intrusions, Iran and North Korea following distantly behind. Russia and Vietnam only carried a sliver each of the total pie chart seen in the report.
The reason for this, Singh said, has less to do with Russia being less prolific in cyberespionage and more to do with how Falcon OverWatch tracks intrusions. Much of what OverWatch tracks are corporate-focused intrusions and threats, and China has a deeper focus on economic espionage than Russia does. The politically motivated activity Russia is known for isn't the focus.
"It's not that the attacks are not happening; it's that the motivation for China versus Russia is different," Singh said. "And Russia is more in the long game. We do have good visibility when it comes to threat intelligence and other areas -- for example Cozy Bear and some other things. But when it comes to OverWatch, we are mostly focused on corporations. And across corporations, you will see more [attacks attributed to] China because it is economic espionage, whereas if you're focused more on the think tanks and the political side, you will see more [attacks attributed to] Russia."
Telecommunications represented a major target of nation-state attacks in the last year, according to the report, with the number of intrusions doubling year over year. "China-nexus adversaries" were the main actors responsible, followed by "Iran-nexus adversaries," CrowdStrike noted.
Infiltrating telecom organizations serve several nation-state objectives.
"Targeted intrusion adversaries will often conduct operations against telecommunications providers to fulfill their surveillance, intelligence and counterintelligence collection priorities," the report reads. "This includes accessing information such as call detail records (CDR) and, in the case of mobile providers, short message service (SMS) communications."
Common techniques used to gain initial access include supply chain compromise, spear phishing and vulnerability exploitation.








