
14 flaws in NicheStack put critical infrastructure at risk
The vulnerability disclosure process for Infra:Halt, a set of flaws impacting critical infrastructure, took nearly a year, due to the nature of supply chain vulnerabilities.
Forescout Technologies and JFrog have discovered 14 vulnerabilities impacting the NicheStack TCP/IP stack, which can be found in operational technology systems used in critical infrastructure.
The vulnerabilities, collectively named Infra:Halt, were disclosed in research released Wednesday by Forescout. NicheStack is a TCP/IP stack released in the mid-1990s and used in operational technology (OT) hardware that monitors and controls the function of physical devices. Two of the 14 vulnerabilities are critical flaws capable of remote code execution (RCE), and the rest allow for denial of service, DNS cache poisoning, information leak and TCP spoofing.
The two RCE flaws disclosed in the report are CVE-2020-25928, which has a CVSS score of 9.8, and CVE-2021-31226 with a CVSS of 9.1. The former is an out-of-bounds read/write bug that occurs when "the routine for parsing DNS responses does not check the 'response data length' field of individual DNS answers," according to the Forescout report. The latter is a heap buffer overflow vulnerability.
In addition to these two critical vulnerabilities, 10 are rated high severity and two are rated medium. To date, Forescout has seen no evidence of exploitation.
Forescout Vice President of Research Elisa Costante said the disclosure process for the vulnerabilities began last September -- nearly a year ago -- which is far longer than the standard 90 days given for vulnerability disclosures. She said part of the reason for this was the complex nature of supply chain vulnerabilities.
"Some stories are very complex, and this one was one of those," she said. "It took a long time for [NicheStack publisher HCC Embedded] to release the patch and actually be educated about what to do and how to do things."
According to a Wayback Machine archive of NicheStack developer InterNiche's now-defunct website, the company's source code has been utilized by many manufacturing, device and industrial vendors including Samsung, UPS, Sony, Philips, Cisco and more.
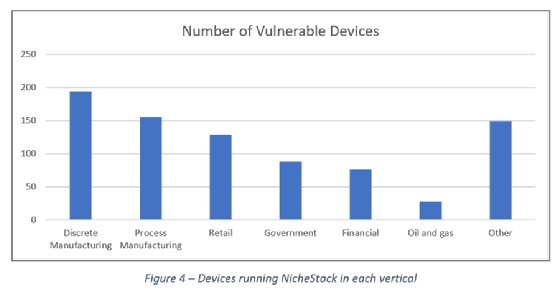
According to a March Shodan query referenced in the research, 6,431 device instances were found using the stack, and more than 2,500 device instances from 21 vendors were found in a Forescout query of its own Device Cloud database. Forescout did not disclose the names of the vendors, but researchers noted in the report that NicheStack is used in Siemens' programmable logic controllers, as well as products from Emerson, Honeywell, Mitsubishi Electric and Schneider Electric.
From these queries, the stack was found used in government, energy and power, oil and gas, manufacturing, networking, and finance, among others. Just under two-thirds of the 6,400 Shodan instances (about 4,000) were based in Canada and the U.S.; Spain (530), Sweden (513) and Italy (346) made up a large portion of the remainder.
HCC Embedded, which acquired NicheStack in 2016, has made official patches available upon request, but due to the particularly challenging nature of updating OT devices -- Forescout uses the phrasing "notoriously difficult" in its blog -- Forescout offered a separate mitigation strategy available in its reporting.
The strategy includes taking complete inventory of devices running NicheStack, enforcing segmentation controls and proper network hygiene, monitoring patches released by affected device vendors and monitoring network traffic for potential malicious packets. Forescout also released a script for its EyeInspect product to scan for exploitation attempts utilizing the Infra:Halt vulnerabilities.
Costante said there are multiple roadblocks that make patching difficult for OT devices affected by the flaws. Many devices may need to be taken offline for updating, and specialist engineers may need to be on site to apply updates directly. As she explained, "Even with our deployments, our engineers may need to actually be flown in a helicopter to a platform in the ocean where those devices are."
In addition, the life of OT devices can sometimes be measured in decades, rather than years, and these devices can be running critical operations, which may need to be taken offline to apply patches. These factors add additional layers to the challenge that may necessitate an alternate mitigation strategy.
The Infra:Halt vulnerabilities were discovered as part of Forescout's Project Memoria initiative, which was started to research and secure TCP/IP stacks with peers in the security research community. In December of last year, the initiative was responsible for disclosing 33 TCP/IP vulnerabilities in four open source stacks, collectively dubbed "Amnesia:33." Forescout estimated that approximately 150 vendors and millions of IT, OT and IoT devices were affected by the Amnesia:33 flaws.
Alexander Culafi is a writer, journalist and podcaster based in Boston.






