
James Thew - Fotolia
Russia using Kubernetes cluster for brute-force attacks
The NSA warned that Russian state-sponsored hackers launched a new container-based campaign aimed at breaching networks and stealing essential data from multiple industries.
The NSA is sounding the alarm over a fresh wave of Kremlin-backed attacks on both the U.S. government and private sector companies.
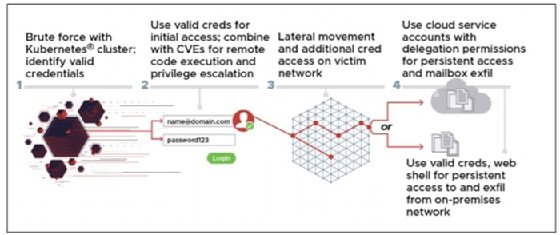
The intelligence agency issued an alert Thursday over what it describes as brute-force password attacks that are being launched from a specially-crafted Kubernetes cluster. The attacks have been attributed to a unit within Russia's foreign intelligence agency, the General Staff Main Intelligence Directorate (GRU); the NSA said it's the same GRU unit that has been identified as the APT28 or Fancy Bear threat group, which has been responsible for several attacks on U.S. targets, such as the 2016 breach of the Democratic National Committee.
In this case, the NSA warned, European companies are also in the crosshairs. In addition to government agencies, the GRU hackers have been going after media companies, defense contractors, think tanks and political groups, and energy providers, among other industries.
"This campaign has already targeted hundreds of U.S. and foreign organizations worldwide, including U.S. government and Department of Defense entities," the NSA said in the alert. "While the sum of the targeting is global in nature, the capability has predominantly focused on entities in the U.S. and Europe."
The NSA declined to comment on what the success rate of the attacks has been, and just how many networks have actually been compromised by the hackers.
The brute-force attacks are part of a larger effort to harvest credentials and gain a foothold in networks. After the automated brute-force operation nets valid user accounts, the attackers shift to a more hands-on approach.
The stolen accounts are used to log into the targeted company's network, where the attackers then look to exploit elevation of privilege and remote code execution vulnerabilities to obtain administrator rights; these vulnerabilities include two Microsoft Exchange Server flaws, CVE 2020-0688 and CVE 2020-17144. From there, the hackers look to move laterally through the network, eventually arriving at a mail server or other valuable data cache.
Once the data and account details have been collected and uploaded to another server, the attackers install web shells and administrator accounts, giving them persistence on the network and the ability to get back in at a later date.
While the NSA says that most of the attacks were launched from behind the cover of Tor and multiple VPN services, the attackers did get sloppy on occasion, and some of the attacks went directly from the Kubernetes cluster, allowing investigators to collect a handful of IP addresses.
To combat the brute-force attacks, the NSA is advising administrators to take some basic steps to limit access attempts or initiate a lockout after a number of failed attempts. Those who want an extra layer of security can also consider multifactor authentication, CAPTCHAs and check for commonly used passwords that are easy to guess.
Organizations should also make sure servers and network appliances are up to date with security patches and firmware updates in order to prevent elevation of privilege and lateral movement, should the attackers manage to get valid credentials.
"The scalable nature of the password spray capability means that specific indicators of compromise (IOC) can be easily altered to bypass IOC-based mitigation," the NSA cautioned. "In addition to blocking activity associated with the specific indicators listed in this Cybersecurity Advisory, organizations should consider denying all inbound activity from known TOR nodes and other public VPN services to exchange servers or portals where such access is not associated with typical use."







