bexxandbrain - Fotolia
Dell BIOSConnect flaws affect 30 million devices
Eclypsium researchers discovered vulnerabilities that, if exploited, can allow remote code execution in a pre-boot environment for 128 different Dell products.
Security vendor Eclypsium has discovered four vulnerabilities that impact 128 Dell device models, and an estimated 30 million individual devices, that allow threat actors to remotely execute code in a pre-boot environment, according to new research released Thursday.
The report, titled "BIOS Disconnect," centers on vulnerabilities involving Dell's BIOSConnect tool in SupportAssist. SupportAssist is a general support tool that comes preinstalled on most Dell Windows computers and tablets, and BIOSConnect is a tool within it used for firmware updates and remote operating system recovery.
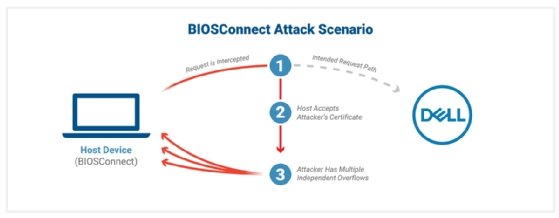
The core vulnerability involves an insecure TLS connection between Dell and the BIOS. The report explains that the BIOSConnect TLS connection will accept "any valid wildcard certificate."
"When attempting to connect to the backend Dell HTTP server, the TLS connection from BIOSConnect will accept any valid wildcard certificate. This allows an attacker with a privileged network position to impersonate Dell and deliver attacker-controlled content back to the victim device," the report reads.
Eclypsium principal researcher Jesse Michael told us the certificate Eclypsium successfully used in the attack scenario cost the company around 70 or 80 Euros.
The other three vulnerabilities are overflow vulnerabilities enabled by the insecure TLS connection being exploited and allow arbitrary code execution at the BIOS/Unified Extensible Firmware Interface (UEFI) level. That said, as Scott Scheferman, Eclypsium's principal cyber strategist, explained, there are cases where these additional vulnerabilities aren't necessary to execute malicious code on a target system.
"If you have Secure Boot disabled, for example, you don't need the three buffer overflows," Scheferman said.
"All three vulnerabilities are independent, and each one could lead to arbitrary code execution in BIOS," the report said.
The vulnerability CVEs are CVE-2021-21571, CVE-2021-21572, CVE-2021-21573 and CVE-2021-21574. Michael said all four vulnerabilities can be exploited remotely. The vulnerability chain, according to the report, has a cumulative Common Vulnerability Scoring System score of 8.3, which is considered "high" in terms of severity.
The 128 Dell models impacted include personal and business desktops, laptops and tablets. This includes, as the report said, "devices protected by Secure Boot and Dell Secured-core PCs." Michael said that while the class of vulnerability is common, these specific vulnerabilities were exclusive to Dell.
Asked about what surprised him most about the vulnerabilities, Scheferman pointed to Dell being at the center of it.
"Absorbing it for the first time, the first thing that went through my mind was, how does a major OEM get TLS wrong where it matters most to the device's trust?" he said. "How did you get it wrong in the year 2021 when TLS has been beaten up on for 30 years?"
While Eclypsium has seen no threat activity related to the Dell BIOSConnect vulnerabilities to date, including both exploitation and scanning, Scheferman said exploitation could have significant consequences.
"The impact of this vulnerability, were it to be exploited in the wild as part of a campaign, could be tremendous because you get persistence at the UEFI, and all the security controls on the operating system -- AV, EDR, SIEM, SOAR, XDR, all that stuff -- none of that would ever see this happen because that operating system is off. It's happening at the UEFI. You have omnipotence and a kind of indefinite persistence if you gain access there," he said.
Michael said the vulnerabilities were first discovered in March. After informing Dell, Michael said Eclypsium gave them the industry-standard 90-day disclosure timeline, plus an additional two weeks.
However, as this report goes live, not every issue will be fixed.
UPDATE 6/24: Dell informed SearchSecurity that it has fully remediated the vulnerabilities for all affected products.
"[Dell is] having some issues getting some of the fixes out, so they're getting some fixes out now and will be pushing more fixes out and, I think, have everything out by the end of July," Michael said.
According to the report, Dell said "a majority" of the updates are scheduled to go live Thursday.
As for current mitigations, the report recommended users apply updates as soon as possible using methods other than BIOSConnect. It further recommended disabling BIOSConnect and listed two methods for doing so. Dell also published an advisory further detailing recommended mitigations and workarounds.
Alexander Culafi is a writer, journalist and podcaster based in Boston.