
Brian Jackson - Fotolia
'FragAttacks' eavesdropping flaws revealed in all Wi-Fi devices
Security researcher Mathy Vanhoef said every Wi-Fi device is impacted by at least one of the 12 vulnerabilities, and most devices are vulnerable to several of the flaws.
A newly disclosed set of eavesdropping vulnerabilities are said to be present on virtually every Wi-Fi device currently in use.
Branded as "FragAttacks" (short for "fragmentation and aggregation attacks"), the 12 vulnerability package centers around the way data is moved between devices on the same network, specifically with the structure of the frames that encapsulate the data moving from point to point.
Mathy Vanhoef, a postdoctoral researcher at New York University, found that plaintext data could be placed into specific fields of the data frames and, thanks to fundamental flaws in the Wi-Fi protocol, would be executed as instructions without being properly authenticated or sanitized. Vanhoef's research claims the bugs are so deeply embedded into the fundamental components of Wi-Fi that they are present on versions of the standard that date as far back as 1997.
"The discovered vulnerabilities affect all modern security protocols of Wi-Fi, including the latest WPA3 specification," Vanhoef noted on the FragAttacks research website. "Even the original security protocol of Wi-Fi, called WEP, is affected."
To be clear, these attacks would require the threat actor to be on the local network alongside the targets; these are not remotely exploitable flaws that could, for instance, be embedded in a webpage or phishing email. The attacker would either have to be on a public Wi-Fi network, have gotten access to a private network by obtaining the password or tricked their mark into connecting with a rogue access point.
Thus far, there have been no reports of the vulnerabilities being exploited in the wild. Vanhoef opted to hold the public disclosure until vendors could be briefed and given time to patch the bugs. So far, at least 25 vendors have posted updates and advisories. Both Microsoft and the Linux Kernel Organization were warned ahead of time, and users can protect themselves by updating to the latest version of their operating systems.
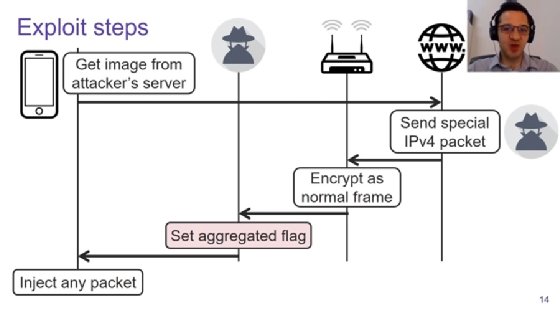
In a presentation set for the Usenix Security conference, Vanhoef explained how by manipulating the unauthenticated "aggregated" flag in a frame, instructions can be slipped into the frame and executed by the target machine. This could, for example, allow an attacker to redirect a victim to a malicious DNS server.
In other instances, the attacker can take advantage of the way data frames are broken down and reassembled to allow an attacker to potentially change the user's decryption key and read data.
There are also flaws in the way access points store and transmit data from fragmented packets that would potentially allow an attacker to slip malicious code into the access point's memory under the guise of fragmented packets that would then be transmitted and reassembled by victims when they reconnected to an access point.
Finally, there is a subset of issues Vanhoef classifies as "other implementation flaws." These include bugs that result in a failure to authenticate handshake frames and flaws that allow frames to include mixtures of plaintext and encrypted data within the same frame, thus leaving the door open for data tampering.
Vendor and industry responses
As mentioned earlier, several vendors have already patched the FragAttacks flaws that impact their products. Microsoft quietly slipped a number of fixes into the March edition of Patch Tuesday, and Vanhoef said that the Linux kernel itself has also been patched, meaning most well-maintained distros should also have a fix.
In both cases, users and admins can protect themselves by making sure all their firmware is up to date.
Cisco classified the flaws as a 'medium' risk due to the lack of remote exploit capability, while Intel also said the bugs are a moderate risk on its wireless networking gear.
Netgear said that the FragAttacks bugs are present in a number of its routers, extenders and cable modem gateways. The vendor is advising users to update their firmware and make sure their Wi-Fi networks are properly secured with strong passwords.
The Wi-Fi Alliance said its members are taking swift action to make sure the decades-old bugs do not reemerge in new gear.
"There is no evidence of the vulnerabilities being used against Wi-Fi users maliciously, and these issues are mitigated through routine device updates that enable detection of suspect transmissions or improve adherence to recommended security implementation practices," the Alliance said in a statement. "Wi-Fi Alliance has taken immediate steps to ensure users can remain confident in the strong security protections provided by Wi-Fi."
Vanhoef also pointed out that users and administrators can minimize the risk of attack by following some basic best practices.
"In regards to the discovered Wi-Fi vulnerabilities, you can mitigate attacks that exfiltrate sensitive data by double-checking that websites you are visiting use HTTPS," he wrote.
"To mitigate attacks where your router's NAT/firewall is bypassed and devices are directly attacked, you must assure that all your devices are updated. Unfortunately, not all products regularly receive updates, in particular smart or internet-of-things devices, in which case it is difficult (if not impossible) to properly secure them."







