
Arsgera - Fotolia
US defense contractor BlueForce apparently hit by ransomware
The Conti ransomware operators demanded nearly $1 million in bitcoin during ransomware negotiations and threatened to publish the defense contractor's data on its leak site.
U.S. defense contractor BlueForce has apparently been hit in a ransomware attack, according to a Conti ransomware chat and Hatching Triage sample.
The Hatching Triage page for the ransomware sample included a ransom note claiming to be from a threat actor who infected the victim with the Conti ransomware strain. The sample was shared with SearchSecurity by TechTarget sister site LeMagIT.
"All of your files are currently encrypted by CONTI strain," the note read. "As you know (if you don't - just "google it"), all of the data that has been encrypted by our software cannot be recovered by any means without contacting our team directly. If you try to use any additional recovery software -- the files might be damaged, so if you are willing to try -- try it on the data of the lowest value."
The note included both a standard URL and a .onion link to an active chat between a Conti operator and a negotiator who claimed to be from BlueForce Inc., a Virginia-based defense contractor that aims to "create and further develop the nexus between DoD [Department of Defense] and DoS [Department of State] with a skillfully blended mix of cross functional defense, interagency and international development expertise" according to its website.
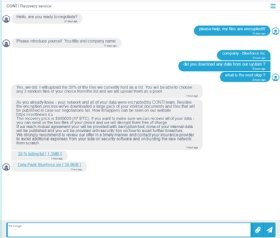
The chat's original message from the ransomware operator, dated April 9, asks if the victim is ready to negotiate. Over two weeks later, the supposed victim replies, saying "please help, my files are encrypted!!!" After the ransomware operator asked the victim to identify themselves, someone in the chat responded Thursday morning and identified themselves as BlueForce and asked for next steps, as well as whether any data had been encrypted.
The threat actor responded in the affirmative and demanded 17 bitcoins (worth nearly $969,000 as of this writing). In addition, the response included a list and data pack of files in order to verify that Conti had breached the company and exfiltrated data. The chat has not been updated since.
BlueForce did not respond to SearchSecurity's request for comment.
Conti ransomware was first reported in mid-2020, and like many other modern ransomware families, it extorts victims by not only encrypting data, but threatening to publish it, too. Recent Conti victims include a number of London schools, as well as fashion retailer FatFace. It was also a member of the Maze ransomware cartel when it was active.
Alexander Culafi is a writer, journalist and podcaster based in Boston.





