
agcreativelab - stock.adobe.com
Remote work increases demand for zero-trust security
One year after lockdowns and office closures prompted a massive, hurried move to remote work, many enterprises are reexamining their security posture.
While many enterprises have been moving toward a zero-trust security approach, remote work spurred by the COVID-19 pandemic accelerated it tenfold.
One year since lockdowns and office closures started, infosec experts say enterprises are transitioning from VPNs to zero-trust networks (ZTN). A zero-trust model is useful for securing remote employees' devices because it makes no assumption that the person logging in with a username and password is who they claim to be. Instead, a ZTN verifies each access request with additional data signals such as geolocation and user behavior, making access easier to control and manage, particularly when there is an influx of users working from different locations.
Gartner analyst Rob Smith told SearchSecurity that zero-trust network access (ZTNA) is a very high-profile item he talks about in almost every single discussion with enterprises. The whole point behind zero trust, he said, is that it does not matter what the device is; a user is given appropriate access based on the posture of the device. That can include if the device is patched, who owns it and what network it is using.
"Maybe you had 5,000 employees going to half a dozen offices. You now need to realize you have 5,000 offices, and making that transition from a management and security perspective is radical. It's throwing 40 years of IT out the window and now rebooting and doing everything right from scratch," he said. "And that's where we are."
One example he gave was of a global insurance company that, on any given day, had about 500 remote workers. Overnight, they went to 50,000.
"And of the 50,000, over 20,000 did not have PCs, so 20,000 bring-your-own devices, you have no choice but to go to a zero-trust model instantly," Smith said.
Amol Kabe, senior director of product management for Google Cloud Security, said his company has also seen a lot of organizations start the zero-trust journey, especially when the pandemic first hit, and the question of how users can still be productive arose. One client example he provided was a company who initially said they would test out Google's zero-trust offering with 100 people.
"The client decided over the course of the day, they didn't even let us know, in two days, they went to 12,000 people."
Google has been running in the zero-trust arena for over a decade, first internally with its own ZTN deployment and then with its commercial offering, BeyondCorp. Kabe said the goal is to create an authorization model where there is no difference between a public and private application.
However, enterprises are frequently still in the beginning stages of the transition.
"No one was prepared. No one. I don't care who you were -- government, finance, military -- pick any vertical you can think of. No one was prepared. And because no one was prepared, disaster recovery just did not work," he said.
There have been three phases since the initial move to remote work, according to Smith. Transitioning to the cloud and zero-trust market is the final phase.
"First phase was 'we're all home, let's get back online as quickly as possible.' The second phase was 'let's try and secure with what we have,' and phase three where almost everyone is now, is 'let's reboot and do it right.' And in that phase, zero trust is one of many possible answers," Smith said.
Christian Espinosa, managing director of infosec services firm Cerberus Sentinel, agreed that many organizations are moving toward zero trust after learning lessons with the past year of remote work. Prior to the pandemic, a VPN may have sufficed, but the recent surge in remote workers who have access to the corporate network through personal devices requires additional precautions.
"A VPN provides secure communication [encryption] and authentication, and some minor endpoint security, but it isn't enough, especially if the endpoint that is VPNing into the corporate environment is a personal device," he said in an email to SearchSecurity. "A personal device should definitely have zero trust."
Kabe also told SearchSecurity that with the onset of the pandemic, zero trust has gone from being a "nice to have" to an "absolute must have" to get work done. "Across the board it's an industry phenomenon where everyone is looking for zero-trust approaches."
Can your enterprise make the move?
While security experts agree that a ZTN is more secure for the evolving work environment, it is not suitable for every enterprise.
Some, like medium-size enterprises, are 100% in the cloud already and have been prior to the pandemic; many major cloud providers have identity and access management (IAM) offerings that allow customers to, for example, deploy continuous authentication systems for privileged users. "But the bigger and older you are as an enterprise, the more likely you are to have things that just won't die on the network. If you're a midmarket enterprise, you could throw away your VPN today. Ultimately, it comes down to the use case," Smith said.
According to Smith, there are four variables to determine a use case: user, device, data and location.
Because all users don't have the same requirements, some need zero-trust access, and some do not. It's also important to understand what kind of applications, data and content they need access to. Is it on premises or in the cloud? Additionally, Smith said location matters because every state and country has different laws.
"Last year at this time, if you would have asked me about 'bring your own PC,' I would have said not even one percent of Gartner clients are actually doing bring your own PC. But then when the lockdown happened, organizations had no choice because people got sent home with no computers. So, now two thirds of Gartner clients are doing bring your own PC on some level. And that could be just a handful of devices or literally tens of thousands," he said. "So, the transition to bring your own PC, as you do that, that really pushes you more toward zero-trust model or another model, like desktop as a service."
Certain sectors like financial services may require a specialized security posture, Smith said. For example, a zero-trust model may not be the best fit for a financial services organization that still has most of its operations on premises rather than in the cloud.
Like Smith, Kaspersky researcher Dmitry Galov said organizational use of zero trust is complicated because zero trust involves many aspects, from network segmentation to continuous authentication, and there are many ways to create a ZTN. "It is important to note that you can use several approaches at once, segmenting the corporate network," he said in an email to SearchSecurity.
Another challenge is that zero trust is a journey, Kabe said. "You can start small, identify either a function or a population that you target for success, and then you start expending."
Pandemic highlights VPN shortcomings
As remote work surged during the pandemic, many organizations found their VPNs struggled to handle the massive increase in usage. In addition to VPNs being contoured to an on-premises environment, the model does not always protect against complex attacks.
Galov said though it is still a popular method, it will not hold up when it comes to attackers that gain access to the internal network after compromising individual users. There have been several instances recently where threat actors gain access using an employees' credentials. "In order to solve such problems, one can use a zero-trust model, in which it is necessary to pass authorization each time a user tries to access a certain resource."
While nothing is 100% effective, zero trust provides a degree of assurance about the state of the devices, and the state of the location where people are accessing from. "With VPN you have unfettered access to the entire network. Zero trust allows you to have a granular control over kinds of access, and which user population has access to that application," Kabe said.
When the pandemic first hit, enterprises tried to make it work with an existing VPN model by adding more hardware. However, Kabe said there is only a finite amount of capacity and you must install that VPN hardware in an office somewhere. Offices were left mostly empty after the pandemic began.
"With zero trust, you can basically say I want all my corporation to be able to access this application in zero-trust manner, and overnight you can do it," Kabe said.
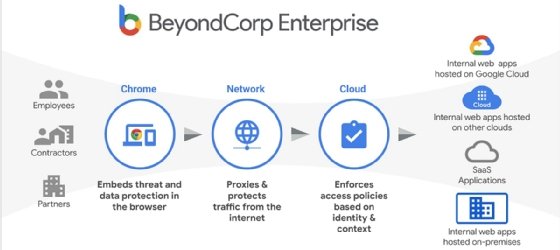
Google launched BeyondCorp Enterprise, which replaced BeyondCorp Remote Accesss, in January two months before the pandemic hit the U.S., and Kabe said the response has been phenomenal. The new offering takes Google's zero-trust concept and melds it with threat and data protection through the company's Chrome web browser. "The primary reason is with COVID, everyone is working from home. So, by definition everyone is remote. Partners can be productive, the supply chain, call center -- because everyone is running remotely."
Microsoft also launched a new initiative to adapt to the security challenges of remote work: a passwordless ecosystem within Azure Active Directory. During a Microsoft Ignite 2021 session last month, Joy Chik, corporate vice president of Microsoft's identity division, introduced new ways to verify users without the use of passwords. It is part of the software giant's strategy to create more reliable and secure authentication options using zero trust.
While zero trust is not the only answer, it is a component of a broader security solution, said Smith. "This whole market is converging to a single framework of what we're calling SASE -- Secure Access Service Edge. What is your plan to supply the broader cloud ecosystem with all these security concepts?"
While the market is moving toward the cloud, and the benefits of a ZTN outweigh a VPN, particularly in the post-pandemic work era, it does not mean VPNs will be obsolete. "The reality is, as long as there is on-premise, a VPN will still be used," Smith.








