
Narong Jongsirikul - Fotolia
Chinese threat group 'RedEcho' targeting Indian power grid
The Chinese nation-state actor's targets include 10 different Indian power sector organizations, but Recorded Future said there's no evidence RedEcho triggered blackouts.
As concerns about nation-state threat activity around the world continue to increase, a new report by Recorded Future has identified a previously unknown threat group attacking critical infrastructure.
A China-linked advanced persistent threat (APT) group dubbed "RedEcho" has been targeting India's power sector, according to research released Sunday by Recorded Future's Insikt Group. According to the report, the newly identified actor is conducting multiple intrusions against Indian critical power infrastructure, acting as potential "pre-positioning" for future escalation.
The security intelligence vendor identified the state-sponsored actor "through a combination of large-scale automated network traffic analytics and expert analysis," with data sources including "the Recorded Future Platform, SecurityTrails, Spur, Farsight, and common open-source tools and techniques," the report reads.
Insikt Group had been observing the intrusions since early last year.
"Since early 2020, Recorded Future's Insikt Group observed a large increase in suspected targeted intrusion activity against Indian organizations from Chinese state-sponsored groups. From mid-2020 onwards, Recorded Future's midpoint collection revealed a steep rise in the use of infrastructure tracked as AXIOMATICASYMPTOTE, which encompasses ShadowPad command and control (C2) servers, to target a large swathe of India's power sector," the report reads.
Targets identified include 10 different Indian power sector organizations, "including 4 of the 5 Regional Load Despatch Centres (RLDC) responsible for operation of the power grid through balancing electricity supply and demand." Recorded Future further identified two Indian seaports among the threat actor's targets.
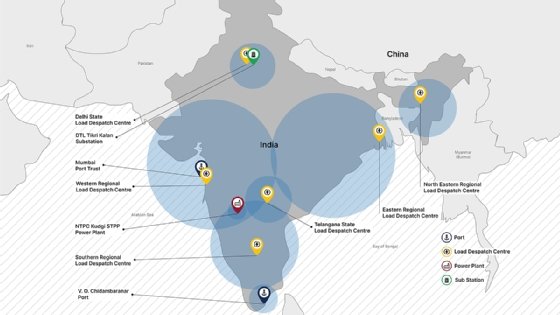
While there were identified similarities between this activity and previously reported Chinese nation-state actors, Insikt Group chose to track it as a "closely related but distinct" threat actor due to a lack of firm evidence.
The report cites a worsening relationship between China and India as a reason for this new cyberconflict, most visible through Himalayan border clashes last May, which resulted in at least 20 combat deaths.
In determining the motive for RedEcho's intrusions, Insikt Group wrote that while targeting critical Indian infrastructure offers "limited economic espionage opportunities," the attacks "pose significant concerns over potential pre-positioning of network access to support Chinese strategic objectives."
"Pre-positioning on energy assets may support several potential outcomes, including geostrategic signaling during heightened bilateral tensions, supporting influence operations, or as a precursor to kinetic escalation," Insikt Group wrote.
A New York Times article that broke the news of Recorded Future's RedEcho research reported possible connections between the threat actor's actions and power outages in Mumbai occurring in October. The Recorded Future report did not connect the Mumbai outage to RedEcho or any specific threat activity, saying such a link "remains unsubstantiated." SearchSecurity asked Recorded Future about possible connections between the outages and this campaign.
"At this time we cannot confirm that the RedEcho activity group nor this campaign is linked to the power outages experienced in the Mumbai region in October 2020. Initial reporting on the incident indicated that the outage was caused by 'tripping at the Padgha-based load despatch centre in the Thane district,' but subsequent but unverified reporting suggests that malware may have been involved," a spokesperson said in an email.
The spokesperson further wrote that the Maharashtra State Load Despatch Centre, referenced in reporting as the victim of this potentially involved malware, "was not found in our datasets tied to this campaign nor in our visibility into AXIOMATICASYMPTOTE infrastructure."
UPDATE: Indian Minister of Power R. K. Singh said Tuesday that "human error" caused last October's power outage in Mumbai -- not a cyber attack. Singh said that while cyber intrusions did take place, they were unrelated to the outage and ultimately failed to reach the dispatch centres' operating systems. He declined to attribute these attacks to China, citing a lack of evidence.
During a live briefing Monday morning, Recorded Future CEO Christopher Ahlberg provided an overview of the report and further stressed that there is currently no evidence that threat actors caused the Mumbai blackout. But he noted that even the intrusions from RedEcho were extremely dangerous. "The activity puts civilian critical infrastructure at risk and should not be done," he said.
Ahlberg also said that despite ongoing de-escalation activities between China and India, this by no means signals the end of RedEcho or campaigns like it.
"It's also important to remember that cyber activity in times of war and in times of peace," he said. "It's a perfect asymmetric tool and has historically not been curtailed by diplomacy."
Ahlberg also pointed out that Recorded Future first notified Indian authorities on Feb. 10 of this year, and the company has made repeated attempts since. After SearchSecurity asked about the Indian government's responsiveness, the spokesperson wrote back saying that Indian officials thanked and acknowledged receipt of the information, and that while no further information was provided, "it is evident that the relevant authorities in India were responsive and acted on the intelligence" based on recent statements by India's Ministry of Power.
Attacks on critical infrastructure have been an ongoing issue. Last month, a Florida city's water supply was almost poisoned with lye when a threat actor gained access to water treatment controls via TeamViewer. And last week, a new report by industrial cybersecurity vendor Dragos identified an increase in APTs targeting industrial control systems (ICS) and operational technology (OT) within enterprises and government organizations that manage critical infrastructure.
Alexander Culafi is a writer, journalist and podcaster based in Boston.







