
adam121 - Fotolia
Chinese APT used stolen NSA exploit for years
Check Point's report details how a zero-day exploit credited to a Chinese nation-state threat group "is in fact a replica of an Equation Group exploit code-named 'EpMe.'"
A nation-state threat group cloned and used a U.S. government cyberweapon years before it was exposed by the Shadow Brokers in 2017.
A China-based advanced persistent threat group, known as APT31 or Zirconium, utilized a Windows zero-day exploit belonging to the Equation Group -- an American APT widely understood to be a part of the Tailored Access Operations group at the National Security Agency (NSA) -- for several years, according to research released by Check Point Software Technologies on Monday.
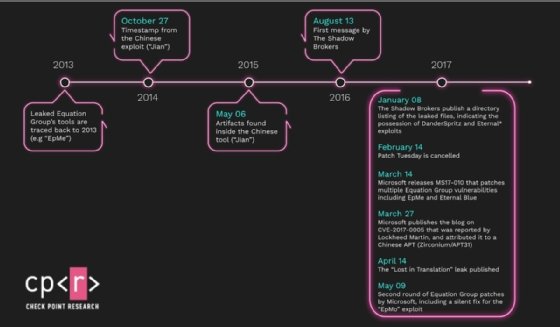
The new report, titled "The Story of Jian -- How APT31 Stole and Used an Unknown Equation Group 0-Day," explains how a zero-day "attributed by Microsoft to the Chinese APT31 (Zirconium), is in fact a replica of an Equation Group exploit code-named 'EpMe.'" The clone, nicknamed "Jian" by Check Point, was created in 2014 and used from 2015 until it was discovered in an attack on government contractor Lockheed Martin in 2017. Microsoft disclosed and patched the privilege escalation vulnerability, CVE-2017-0005, in March 2017.
EpMe was part of Equation Group's DanderSpritz attack framework that includes a wide variety of hacking tools and four local privilege escalation exploits, including EpMe along with ElEi, ErNi and EpMo (all four are abbreviations of larger internal code names). Check Point's research also references the "NtElevation" modules within DanderSpritz responsible for elevating privileges of malware implants.
But these hacking tools, along with others, were exposed by threat actors referring to themselves as the Shadow Brokers. The group first emerged in 2016, publicly releasing a cache of cyberweapons and exploits belonging to the NSA's Equation Group. The Shadow Brokers continued releasing these hacking tools in 2017, including a cache known as "Lost in Translation" in 2017.
First discovered six years ago, the Equation Group is known for its large number of international cyber attacks as well as its authorship of the EternalBlue exploit, which was later used by threat actors in the WannaCry and Petya cyber attacks. Its practices were initially reported by Kaspersky in 2015 and further disclosed by The Shadow Brokers in a series of leaks spanning between 2016 and 2017.
EpMe and EpMo origins
It's unclear how Chinese threat actors came into possession of the EpMe exploit. In the report, Check Point researchers theorized that either EpMe was obtained via an Equation Group operation on a Chinese target; an Equation Group operation on a third-party network also monitored by the Chinese APT; or an APT31 attack against Equation Group infrastructure.
While the report's title uses the word "stole," a Check Point spokesperson said it's difficult to determine whether or not APT31 or another group obtained the exploit by infiltrating Equation Group servers.
"We believe that the first two options are more likely, but we don't know for sure how exactly was the exploit acquired by APT31," the spokesperson said. "Theoretically, since the leaked Equation Group files are dated to 2013, it is possible that whoever leaked the files could share them with other entities."
X0rz, an anonymous security researcher who has analyzed Shadow Brokers' activity, told SearchSecurity via Twitter direct message that it's unlikely Chinese threat actors discovered the vulnerability on their own or obtained it through a zero-day broker because "Jian" shared artifacts from EpMe and other DanderSpritz exploits. "APT31 probably got it from incident response, RAM analysis, or packet capture," they said.
At the time EpMe was disclosed and patched in March 2017, the flaw was not identified as one of the exploits exposed by the Shadow Brokers. At the same time, Microsoft appeared to also patch a flaw for EpMo, a similar privilege escalation exploit for Windows, but Check Point researchers said they could not find a Common Vulnerabilities and Exposures (CVE) identification for that vulnerability.
Check Point researchers also noted that EpMo, unlike the others NSA exploits leaked by the Shadow Brokers, was never publicly discussed until Check Point's research, despite being publicly accessible on GitHub postings since 2017, including one from x0rz.
X0rz said via direct message that they had "no idea" why EpMo had not been reported on previously, though they did mention it was a local privilege escalation (LPE) exploit. "LPE means you already need to execute code on your target, so it's less 'dangerous' than Eternalblue or DoublePuslar," they said.
A Check Point spokesperson told SearchSecurity in an email that EpMo's newly discovered status may be the result of the exploit being buried in the "Lost in Translation" leak by the Shadow Brokers.
"As far as we managed to find, it seems we are the first to analyze the entire "NtElevation" exploitation module of DanderSpritz. This includes all exploits contained in it, including EpMo," the spokesperson wrote. "We think that as it was buried deep in the dump, other exploits such as Eternal Blue received the public's attention, especially when they were placed in a folder with the clear name of 'Exploits.'"
Security news director Rob Wright contributed to this report.
Alexander Culafi is a writer, journalist and podcaster based in Boston.







