
Gorodenkoff - stock.adobe.com
Maze gang shuts down its ransomware operation
Maze ransomware has shut down, according to an announcement it posted Sunday, although some evidence suggests that Maze operators have resumed attacks under a different name.
It appears that we have finally reached the end of the Maze.
The notorious Maze ransomware gang has shut down a little more than a year after its founding, according to an announcement posted to Maze's data leak website Sunday.
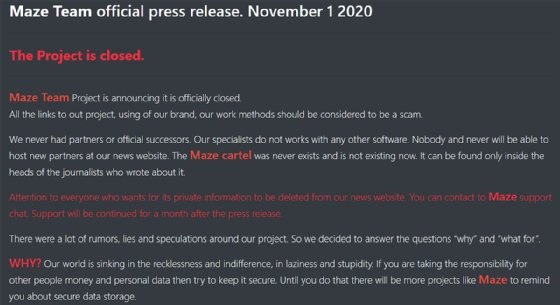
"Maze Team Project is announcing it is officially closed. All the links to out (sic) project, using of our brand, our work methods should be considered to be a scam," the announcement read. "We never had partners or official successors. Our specialists do not works (sic) with any other software. Nobody and never will be able to host new partners at our news website. The Maze cartel was never exists (sic) and is not existing now. It can be found only inside the heads of the journalists who wrote about it."
Regarding the claim that the "Maze cartel" never existed, evidence points to the contrary. In June, the ransomware gang began listing attacks and leaked data from other types of ransomware besides Maze, such as Ragnar Locker, under the heading "Maze Cartel provided by Ragnar." In comments to BleepingComputer, which first reported the formation of the cartel, Maze operators confirmed they were working with other ransomware groups, treating them as partners in a business venture rather than competitors.
The announcement, which they refer to as a press release, said that for one month, the ransomware group's "support chat" can be contacted about removing personal data leaked by the group on their news site. However, because the data was only leaked because ransomware victims wouldn't pay their ransom, it is unknown if this is being offered as a free or paid "service."
In addition, the group claims that they had the opportunity to potentially "cut the access to internet for 35 states" but they decided not to.
"How come that you don't understand that right now a hacker attack is enough for a large area or a country to lose the access to internet, water, gas and electricity. As an instance we had the access to state life support systems of New Yorks (sic) and to major internet providers. A good attack was able to cut the access to internet for 35 states. We didn't attack those objects but their security is still disgusting," it read.
A significant portion of the post is devoted to sharing the official reasoning behind why Maze exists. However, outside of a passing reference to the group's intention to "remind you about secure data storage" in launching ransomware attacks, most of the "reasoning" consists of statements about how the world is becoming a "digital detention camp" and how the advancement of the connected digital age is turning people into a "controllable flock."
Peter Mackenzie, incident response manager at Sophos Rapid Response, told SearchSecurity that he saw three likely scenarios for Maze shutting down. One, "They believe law enforcement are getting close to finding them so they want to get out before they get caught;" two, "They are simply quitting while they are ahead;" and three, what he says is the most likely option, "They aren't really going, just rebranding and moving to a new ransomware family."
Jeremy Kennelly, analysis manager for Mandiant Threat Intelligence, said it's plausible that Maze has truly shut down, possibly because of internal conflicts or increased law enforcement scrutiny. "Services of this sort may also be deprecated in order to enable their operators to found a parallel operation using different malware or a different profit-sharing or operational model," he said in an email to SearchSecurity. "We assess with high confidence that many of the individuals and groups that collaborated to enable the Maze ransomware service will likely to continue to engage in similar operations -- either working to support existing ransomware services or supporting novel operations in the future."
Kennelly emphasized that many of the claims made by Maze in Sunday's announcement are misleading.
"It is important to note that despite this press release claiming otherwise, Mandiant has collected significant evidence suggesting that Maze was operated via a profit-sharing arrangement where multiple discrete criminal groups collaborated to perpetrate their crimes - one group operating the central Maze infrastructure and various other individuals and teams working together to obtain access to victim networks and deploy Maze ransomware," he said, adding that threat groups such as FIN6 have worked with Maze to further monetize intrusions.
At the end of the announcement, Maze cryptically spoke of its future.
"We will be back to you when the world will be transformed. We will return to show you again the errors and mistakes and to get you out of the Maze," it read.
Two recently emerged ransomware variants known as Egregor and Sekhmet have been observed by threat researchers as sharing similarities with Maze, and some speculate that the gang is going for a rebrand rather than shutting down entirely.
Mackenzie said that the theory holds weight.
"As Maze attacks have reduced over the previous month, Egregor attacks have increased," he said. "While this could just be a coincidence, the TTPs of an Egregor attack are very similar to a Maze attack, adding weight to the theory it might be the same people."
Launched around mid-2019, the Maze ransomware gang gained notoriety for pioneering the data theft and public shaming tactics that have become widespread today. Compared to earlier ransomware efforts that would primarily encrypt files and demand a ransom, Maze would take things further by encrypting and then stealing the victim's data before publishing it on a public-facing website. Other groups have adopted these tactics since.
Some of the group's notable victims include Cognizant, LG Electronics and Pitney Bowes, though evidence and published leaks suggest Maze has hit at least 100 organizations, and perhaps far more than that, over its lifetime.
In March, toward the beginning of the coronavirus pandemic, Maze gained attention for promising to stop attacks against medical facilities and hospitals. Shortly after this announcement, they leaked data of a medical research company, and in May, they published data from two separate cosmetic surgery practices.








