
beebright - stock.adobe.com
Mitre ATT&CK: How it has evolved and grown
Adoption of the Mitre ATT&CK framework, which saw version 8.0 released Tuesday, has grown rapidly over the last years, though challenges still remain for enterprise users.
While the Mitre ATT&CK framework started off as an internal Excel spreadsheet, it has evolved into a global knowledge base of threat activity, techniques and models that's become indispensable for many organizations.
The public release of the framework in 2015 garnered little fanfare, but today it is widely popular among enterprise organizations, governments and security vendors. Not only does the Mitre ATT&CK framework provide a common knowledge base of adversary activity in the wild, it also helps organizations to prioritize threats, evaluate security methods, and vet products and services.
The ATT&CK framework is also commonly used by government agencies such as the Cybersecurity and Infrastructure Security Agency (CISA) in alerts and advisories about threat activity. It was recently used in a joint cybersecurity alert from the FBI and CISA regarding a Russian state-sponsored advanced persistent threat (APT) actor was compromising U.S. government targets.
"See the ATT&CK for Enterprise framework for all referenced threat actor tactics and techniques," the alert said.
ATT&CK has evolved significantly over the last five years. Mitre released version 8.0 of the framework Tuesday; in particular, the ATT&CK for Enterprise threat model will add new adversary tactics for activity such as reconnaissance.
Mitre ATT&CK principal cybersecurity engineer Adam Pennington said ATT&CK is similar to an encyclopedia that describes various activities that adversaries perform as they work their way through an intrusion.
"It consists of information on over 160 of these behaviors in our main framework, so it's something that people are using these days in order to be able to describe those activities with a consistent language and be able to have different options that they can leverage to respond to those," he said.
Over the last couple of years, Pennington said Mitre has seen an explosion of use as it became more widely adopted throughout the security community.
"It's seen a lot of organic growth through word of mouth as people have embraced it and talked to us about various needs. We've gone from what was originally 40 to 50 behaviors, up to now over 160," he said. "We're covering areas we didn't use to like mobile devices and industrial control systems, as well as a lot more information for people to be able to help themselves and how to stop specific behaviors. We're taking free, open source public reporting, figuring out which behaviors are in it from ATT&CK and publishing that ourselves."
During a session at the Forrester Security & Risk Global 2020 virtual conference last month, Forrester Research senior analyst Brian Kime said it was in late 2017, early 2018 when ATT&CK began to take over as the most popular of the intrusion frameworks.
"It's popular because it helps us build resilient security architectures. It provides us with a method of modeling threats and this will allow us to build detections and collect the right telemetry across our environments from the perimeter down to the end points," he said in the session. "ATT&CK by itself it not a threat intel, but it should be a component of a threat profile."
Sekhar Sarukkai, McAfee fellow and vice president of its cloud business unit, said the framework's increasing use over a short amount of time is also attributed to trust, and the recent distribution of that trust from internal networks to the cloud.
"Traditional security assumed that everything was near controlled, but the new reality is that trust has become completely opened up because of the cloud. Today, there's no enterprise that has everything in their control," Sarukkai said. "Secondly, during the last few months with COVID, work from home required a distributed fashion where it naturally dovetails with the distributed trust model and required the security teams to look at other ways to defend its security posture."
Additionally, Kime said in his session that the framework provides a way to cluster threat activity and drive patterns. "Instead of presenting a SOC [security operations center] analyst with individual events, we can present them with a pattern of events that helps them better understand."
ATT&CK-ing the cloud
The frameworks' popularity, along with the rapid cloud adoption, inspired a report by graduate student researchers, Jasdeep Basra and Tanu Kaushik titled, "MITRE ATT&CK as a Framework for Cloud Threat Investigation." In the report, Basra and Kaushik interviewed and surveyed security professionals about how to address cloud security challenges, such as identifying and mitigating threats in hybrid environments.
The joint report, produced by McAfee and the Center for Long-Term Cybersecurity (CLTC) at the University of California, Berkeley, found that 87% of survey respondents agree that adopting the ATT&CK for Cloud matrix will improve cloud security in their organizations. However, it also found that only 49% of respondents felt highly confident in the ability of their security products to detect adversary tactics and techniques in each of the ATT&CK matrices.
Sarukkai said incorporating the cloud dimension into the ATT&CK framework is crucial because so many threats will cross the "silos" of internal networks, endpoint devices and external cloud services.
While the framework was originally focused more on endpoint threats, Sarukkai said an increasingly common attack vector today is a threat actor compromising a cloud administrative account.
"That typically happens through traditional malware and through endpoint and then once they've gotten compromised the admin then becomes the launching pad to attack the cloud. That's one direction where attacks are going from the device to cloud," he said. "Another common attack vector we saw was around COVID-related campaigns. There was a spike in external threats. In that case, it's an example of how a bad actor can compromise the cloud environment and then expand out into the endpoint."
Sarukkai said increasingly SOC teams are seeing that and saying they can't just look at silos to feel confident in their security postures. The report found that 45% of global survey respondents identify the lack of interoperability with their security products as the biggest challenge with the ATT&CK framework and 43% cite the challenge of mapping event data to tactics and techniques.
In addition to interoperability, the report determined that a large percentage of enterprises do not correlate events from the cloud, networks and endpoints to investigate threats; only 39% of enterprises do.
"The data indicates that's the challenge customers are facing -- 83% of respondents said that ATT&CK framework was very comprehensive, but they are manually looking at mapping some of these techniques into their framework," Pennington said. "And the flip side is they're seeing it's becoming intractable because of the nature of these attacks, which are cross-silo. If you look at the data, less than 20% of these customers have fully adopted ATT&CK from an operational perspective, so they can't automate because of the lack of this support."
Pennington said SOC teams want the data and visibility provided by various security products, from endpoints and mobile to network and cloud, to be normalized on the ATT&CK framework and presented on some type of dashboard and fed into other products like SIEMs.
According to the CLTC report, 79% said the framework would make them more comfortable with cloud adoption. "That sort of translates to with better security, you're more likely to enable businesses to go to the cloud and for businesses to be more effective," Sarukkai said.
ATT&CK challenges
The cloud matrix is just one of a collection of matrices, Kime said.
"MITRE ATT&CK is not just one framework; it's a collection of matrices based on the type of environment you're defending. The one that most people refer to when speaking about it is the enterprise matrix, but you can filter it down based on operating system and cloud platform," Kime said in the session.
Most of what goes into the ATT&CK matrixes are suggestions from the community. "It started off as something completely us where we were putting it out there, but a majority of things going in today are thanks to people contributing back," Pennington said.
Despite its gaining popularity, as the data from the joint study found, users continue to have difficulty learning to use the framework.
There are two fundamental challenges, Sarukkai said.
"A lot of tools didn't have the ability to support it. Enterprises who don't have these products end up doing it manually which they means they aren't fully able to adopt the Mitre ATT&CK framework because they are getting inundated with instances and because they don't have the tooling they need to be effective. That's the biggest reason," he said.
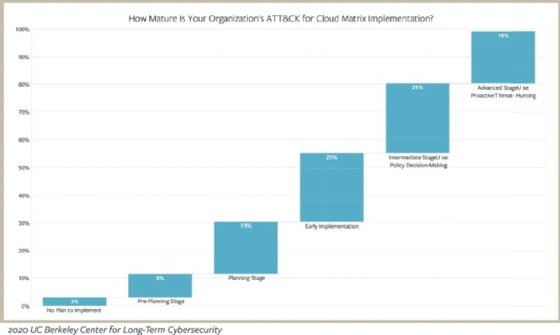
The second problem, Sarukkai said, is that organizations want to use ATT&CK to automate remediation and help alleviate the workload on SOC analysts. But such use requires a level of maturity with ATT&CK, and the report found that just 19% of respondents have reached that maturity level.
The biggest challenge, according to Pennington, is people being overwhelmed.
"We recognize that. ATT&CK for Enterprise, the main knowledge base people are using, is 156 high-level behaviors as of right now. And so, if an organization is going in and trying to just go across and immediately in one pass figure out what their stance is against 156 behaviors, they'll be overwhelmed, and we've seen that," he said. "We're tried to release a number of resources over the past year, how to get started, how to prioritize, and plan on releasing more free training in the future."
While it's useful for prioritizing threats, there are some things ATT&CK is not, Kime said.
"It's not something you do. It's not a process. It is not really something you operate and install and it's not a technology or a product. It's also not something that you aspire to do all of because many of the MITRE techniques are actually legitimate things that users and system administrators do, so having a goal of alerting on every type of technique is actually a pretty poor strategy," he said during his session.
An ever-evolving framework
According to Sarukkai, outsourcing security operations through the use of the Mitre ATT&CK framework is where the evolution may lead overtime. The CLTC report found 69% of respondents said they would be more comfortable outsourcing security operations through the framework.
"Today, the biggest challenge with security is getting trained staff who know what cybersecurity is about and the fact they are more willing to look at outsourced SOC in essence because they now feel like they have a more common lingo for which they can work with third parties," he said.
One of the next steps in the framework's evolution, announced Tuesday with ATT&CK 8.0, is the inclusion of techniques that adversaries use to attack network devices like routers and switches. Another addition in the new version is "resource development," which delves into how threat actors collect the necessary pieces they need to accomplish an intrusion. Those pieces can include compromised assets like servers or virtual machines, as well as SSL certificates and legitimate administrative tools.
Pennington said the effort over the last five years to make security products more compatible has paid off. In the beginning, organizations mostly used the framework for intrusion detection sensors. But that has changed drastically, thanks to customer-driven efforts to further utilize the framework in their overall security postures.
"In terms of ATT&CK adoption and people needing it, I think it has improved quite a bit."








