
designsoliman - Fotolia
Surge in ransomware attacks threatens student data
Ransomware attacks are not the only threats facing K-12 schools during the COVID-19 pandemic. Cybercriminals are stealing and exposing students' personal data as well.
Student data has become increasingly threatened as cyberattacks on schools intensify this year.
This tactic of data exfiltration and extortion, which has become especially prevalent in ransomware attacks, puts additional pressure on schools to pay hefty ransoms in order to protect the privacy of its students. On top of demands caused by the frenzied switch to remote learning, schools must adapt to new threats like these each day.
For example, the Clark County School District (CCSD) in Nevada was hit by a ransomware attack on Aug. 27, which may have resulted in the leak of student data. When it came time to make the decision whether to pay, the school system declined. The district posted an update on Sept. 28 saying it was aware of media reports claiming student data had been exposed on the internet as retribution for not paying the ransom.
"CCSD is working diligently to determine the full nature and scope of the incident and is cooperating with law enforcement. The District is unable to verify many of the claims in the media reports," the update read.
On Sept. 30, the district posted a Notice of Data Privacy Incident on its' website, which mentions the possibility of leaked data.
"While CCSD's investigation is ongoing and has been unable to determine whether any specific file containing sensitive information was actually accessed or acquired by the unauthorized actor, CCSD's investigation determined that certain current and former employee information may have been accessed or acquired by the unauthorized actor. Therefore, in an abundance of caution, CCSD is notifying individuals, including certain current and former employees, of this incident whose name and Social Security numbers were present in the affected systems at the time of the incident."
Brett Callow, threat analyst at antimalware vendor Emsisoft, said the CCSD data was posted on the Maze ransomware group's leak site, which exists on both the clear and dark webs [Maze's website was offline at press time]. Maze pioneered the tactic of extorting victims through threatening to leak confidential data. In addition to CCSD, Callow said there's been a significant uptick in the number of successful attacks on school districts in recent weeks.
"At least 12 districts have been hit this month alone, with the attacks interrupting education at up to 595 schools. Data was stolen and published in five of those 12 cases," he said.
One month after the ransomware incident impacted CCSD, reports of another threat began rolling in: phishing phone calls. The district took to Facebook to address concerns.
"The Clark County School District (CCSD) has received reports of some individuals receiving phishing phone calls by numbers that appear to be connected to CCSD. These calls are not being made by CCSD schools and appear to be a third-party spoofing caller ID and using robocalls to attempt to phish and demand payment. Please know that CCSD would not demand payment by phone. CCSD is aware of the matter and is investigating. If you receive such a phone call, please disregard it."
It's unclear if the phishing calls are related to last month's ransomware attack. SearchSecurity reached out to CCSD for comment but have not heard back.
The threat of data exposure may pressure victims to pay ransoms. But Bill Conner, CEO of security vendor SonicWall, said when it comes to deciding whether to give into the blackmail, once you pay, you'll be on the list forever, "They'll just keep coming back to that school. And once they hit one, they'll go to the next one."
Once the threat of stolen data becomes an issue, Conner thinks of it more as identity theft.
"You can pick age, gender and access that. Once you steal that data, it becomes valuable on the dark web on many different attributes," he said. "Even if you do pay, there's a 50% chance you might not be able to recover your data anyway. Even if they get the data back, it doesn't mean there's not a copy somewhere in the wild."
Popular targets
Threat actors have long targeted K-12 schools and higher education in the past, but such attacks have increase amid the shift to remote learning during the COVID-19 pandemic. "They are extremely vulnerable even more than they were one year ago," Conner said.
New research by endpoint security vendor Absolute Software examined the effects of distance learning on endpoint health, device usage, safety and security as schools adapt to remote and hybrid learning models in the 2020-2021 school year. It determined that 60% of all malware attacks, particularly ransomware, occur in education.
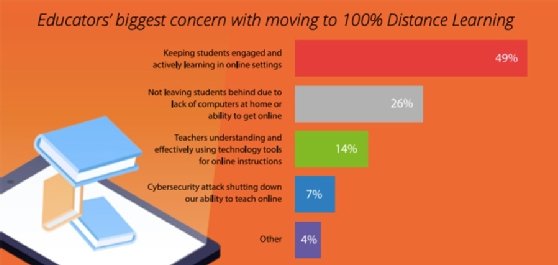
Endpoint protection vendor Morphisec also released new research, which examined COVID-19's impact on the new, virtual school year and consisted of over 500 teachers and administrators across the U.S. who were surveyed in July. According to the report, "despite ransomware attacks increasing in number and sophistication, over half of K-12 educators say their institution has not warned them about the specific dangers of ransomware. In fact, across both K-12 and higher ed institutions, just 13% of educators say they feel ransomware poses the most significant risk as they move to distance learning environments."
As evident from the Nevada School District ransomware attack, Fairfax County Public Schools and others, ransomware is posing one of the largest threats. Because COVID-19 brought on a need to switch to remote learning so quickly, schools did not have much time to adjust, making them all the more vulnerable.
Andrew Homer, vice president of security strategy at Morphisec, said schools' boards are putting tremendous pressure on educators to figure out distance learning and security simultaneously, while teaching.
"Distance learning just massively opened up a huge attack surface because now you're using unhardened collaboration applications like Zoom and at the same time, these machines are now remote so how are you going to update them, patch them?" he said. "These are all unforeseen things. They are being pressured to do more with less and these kids in K-12 are the less responsible folks around security hygiene. It's the perfect storm type scenario."
Awareness around the expanded attack surface is another concern and is not well understood by the teachers, faculty and staff who are actually deploying the distance learning solutions, Homer said.
According to the research by Absolute, "remote learning is creating tech support challenges that are taking away valuable time for teachers to "teach." The data showed 9 out of 10 teachers reported spending more time troubleshooting technology problems.
"They're are not understanding what the threats are that makes them vulnerable. Enabling these collaboration applications, having these machines outside the school system and the implications around that, it's no surprise that many have already been attacked," he said. "We know Zoom is being targeted. These are applications that have not seen widescale usage. What's worrisome is there's no increase in spending or budget or staff to combat this looming threat."
Morphisec performed a demonstration where threat researchers broke into Zoom and were able to use it as an information stealer to scrape credentials and actually record sessions unbeknownst to users. "They are easy to crack because they haven't been used in enterprise and mission-critical type environments up until now. And you can go right down the line whether it's Slack or Webex," Homer said.
According to Absolute data, there was a 141% increase in collaboration software, including BlueJeans, Skype, Microsoft Teams and many popular tools.
One reason K-12 is an easy target is the weak security posture, Conner said. Remote learning is only amplifying the dangers. "Schools are not always the best at cybersecurity or backing up. And now, it's extremely distributed networks."
Conner also said many challenges facing the new school year simply come down to a lack of funds for K-12 school systems.
"A best practice would be to really start to segment the networks. Put different applications and identities in different levels of security. If you're an admin or associated with financials, you need to be in a much more secure platform, not just at the school but at your home," Conner said.
Absolute data indicates that 46% of schools have at least one device that uses rogue or nonauthorized VPN or web proxy applications, "but it only takes one vulnerable device to create a security incident."
The rush to get remote learning up and running also resulted in ill-preparedness, Homer said. "Everyone from the superintendent to the board of trustees are deeply concerned about ransomware, they just don't have a good plan on how to prevent it and prevent some of these attacks because they've been so focused on enabling distance learning," he said.
Attackers recognize these flaws, making schools an even easier target.
"They have their business model, too. They can go after K-12, which they know are not patching their systems, they're vulnerable to using these collaboration applications and go after them. It's much easier with known exploits than they can with an enterprise company that has a robust, layered Defense in depth strategy."







