
Lance Bellers - Fotolia
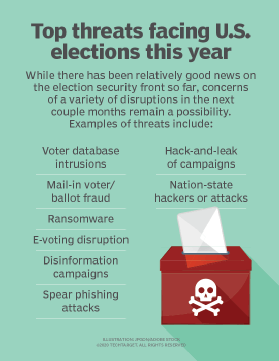
Disinformation, mail-in ballots top election security concerns
While there have been no major cyberattacks this election season, threat actors are waging disinformation campaigns around hot-button issues like mail-in ballots.
Infosec experts generally feel the U.S. is better positioned to defend against election security threats this year, but concerns remain about the next couple months and beyond.
The FBI and the Cybersecurity and Infrastructure Security Agency (CISA) last week announced that they have not observed any voter database intrusions or hacks of voting systems this year. While there have been no direct cyberattacks or hack-and-leaks of campaigns, advanced persistent threat (APT) groups continue to focus on the U.S. elections by spreading disinformation through channels like social media networks. And experts warn that with less than two months to go before election day, the threat of major cyberattacks still exists.
While nation-state threats are a real concern, Cybereason's virtual election security simulation last month demonstrated that elections are vulnerable to anyone looking to cause chaos. During the virtual event, titled "Operation Blackout," Cybereason's red team members played the role of hackers in a simulated attack, and actual law enforcement officials drew off their experience to respond to disruptions. In the end, they determined that it doesn't take very much time, money or effort to cause some level of confusion.
But the biggest threat is still the human factor and the risk of falling for spear phishing attacks, said Mark Testoni, CEO of SAP NS2.
 Christopher Krebs
Christopher Krebs
"Remember all that data back in 2016 -- they got inside the Democratic National Committees' email server systems. People have become more cognizant of that, but it is still a huge threat," Testoni said. "It's still the No. 1 threat for breaches, so I think awareness in general is greater to the cyberthreat than it was and political parties are much more in tuned than back in 2016. Nobody wants a repeat of 2016 just in general."
Going further back in election history, new types of voting emerged in the wake of the 2000 election which continue to evolve. One issue that year, according to the Better Identity Coalition coordinator Jeremy Grant, who spoke at an e-voting panel last month, was with the hanging chad in Florida. But new voting technology has introduced other problems, he said.
"People said let's go digital. The emergence of new voting machine providers who were doing things digitally claimed they were doing great security and frankly didn't pay a lick of attention to it," Grant said. "We're still in this phase today where for the most part those vendors have taken a very pretentious approach with the security communication that has people on guard."
Some improvements have been made on that front; for example, Election Systems & Software, the largest vendor of U.S. voting equipment, unveiled its first vulnerability disclosure program at Black Hat 2020 last month, which featured a heavy focus on election security. But there are other weaknesses and potential threats beyond current disinformation campaigns that loom ahead of November. Christopher Krebs, director of CISA, said during his Black Hat session that one of his biggest concerns is ransomware attacks on local governments and their election infrastructure.
But as recent threat activity has shown, APTs can use relatively simple disinformation campaigns to create confusion and chaos, while decreasing trust in U.S. elections.
Mail-in ballot controversy
While the world moves toward digital voting systems, mail-in ballots are still essential as indicated by the recent United States Postal Service (USPS) disruptions. Proposed changes by the USPS, including shorter hours and fewer mailboxes, just weeks away from Election Day, caused concerns for mail-in voters. After 21 states announced plans to sue the USPS, changes were postponed until after the election.
Infosec experts don't expect the postal service slowdowns to have a direct effect on election security in November. However, threat actors are already attempting to use the controversy to their advantage.
Last week, the Department of Homeland Security (DHS) notified state and local law enforcement of possible new misinformation campaigns. A DHS intelligence bulletin, first reported by ABC News, warned of Russian disinformation on mail-in voting. "We assess that Russia is likely to continue amplifying criticisms of vote-by-mail and shifting voting processes amidst the COVID-19 pandemic to undermine public trust in the electoral process," the bulletin said.
Testoni said mail-in ballots have worked effectively in the past and don't pose a major threat to election because election infrastructure is distributed across so many states and localities that coordinating an attack at scale would be extremely challenging. However, he said there's still the potential for threat actors to cause disruption around the topic through disinformation campaigns.
Bill Harrod, federal CTO at MobileIron, said there are steps voters can take to address postal service disruptions. "The vagaries of the U.S. Postal Service may result in some unease about the timeliness of the delivery of completed ballots, and the best way to mitigate that is to act early, request, complete and return your mail-in ballot as early as possible," he said in an email to SearchSecurity.
The impact of not giving citizens the right to vote by mail or electronically would be negative, Agora CEO Leonardo Gammar said during a virtual e-voting panel last month.
"We struggle a lot in Europe, and I think it's the same in the U.S. The young generations are not really keen on queuing for hours and going to polling stations," Gammar said. "So, by not giving us the option to vote from a distance is going to make the election process less credible in my opinion."
Online voting is gaining momentum as a remote option, especially after the COVID-19 global pandemic. Okta co-founder Frederic Kerrest said e-voting could easily dovetail existing mail-in or in person voting methods, providing an easier process, but there are still concerns about integrity and security.
"More than half of Americans are worried e-voting is insecure, so we have to get it right," Kerrest said. "If we authenticate voter's identities when they vote by any method, we'll ensure every voter is voting one time and only for themselves and help prevent voter fraud. Concerns about backup, about fraud -- these are tractable problems that have to be solved and we have to go solve them."
Improving election security
One important combatant to prevent methods of disruption is simply communication. Federal agencies like DHS and CISA have touted increased transparency and communication about election security threats so that voters, as well as election officials and elected leaders, are fully informed about threat activity. In a report this summer titled, "What to expect when you're electing," Matt Olney, director of threat intelligence at Cisco Talos, recommended establishing "clear communications channels between the vendor, state and counties to ensure problems are handled quickly and information is properly disseminated."
Other security experts agreed. "When I look at the attack surface and the risks from nation-states that would be doing anything they could to take advantage of a big juicy target like the U.S. having something that's maybe not as secure, I think that you'll need smart people from all corners," Grant said.
One of those corners includes the state, local and city governments.
"The security and resilience of voting infrastructure vary greatly. Each state legislature is responsible for conducting elections in their jurisdiction. As a result, there is a huge number of disparate and complex rules and regulations governed by the state and enacted at the local level," Harrod said.
Law enforcement also plays a role in assisting with communication, especially when it comes to misinformation campaigns. A critical takeaway from Cybereason's virtual election simulation was that law enforcement must create open lines of communication between government departments, media sources and social media companies.
In addition, open discussion between the infosec community and voting vendors is also important.
"I shouldn't even say two sides -- they're both looking for the same thing. History in the past 20 years, a good chunk of what I would call the cybersecurity community, has become very frustrated with the tech providers in this space," Grant said. "In some cases, we've seen them attacking the security researchers who are finding the real vulnerabilities that can create risk. Security experts aren't adversaries. They should be embraced as partners."
Two other adversaries -- the political parties -- should also be on the same page when it comes to election security. Harrod said in general the two campaigns are taking cybersecurity threats more seriously than in earlier years.
"There is a greater focus on mitigating cyber risks," Harrod said. "Both of the campaigns have been briefed by the Department of Homeland Security on the likelihood of cyberattacks, and I am certain they are working to educate all of the campaign staff and address the threats from phishing, social engineering, password management and general cyber hygiene."
While money is the engine that drives the campaign and every dollar spent on cybersecurity is a dollar that cannot be committed to advertising, there are fundamental cybersecurity protections to invest in, Harrod said.
"I would encourage both campaigns to invest in things including antiphishing and mobile threat protection, strong authentication, encrypting all communications, virtual private networks for all apps and enforcement of security policies on all mobile devices."
Lessons were also learned from the widespread adoption of electronic voting machines years ago that can be applied today. While it aimed to minimize cyber risks by casting ballots electronically, using the machine to record and tabulate results which were then reported to a centralized point, it also highlighted the importance of having a paper trail.
"These machines were shown to be insecure and subject to tampering and altercation without detection," Harrod said. "Today, most states have a paper ballot or a paper receipt process that can be used in the audit and validation process. Many states have put in place procedures for risk-limited audits. This provides for a much greater assurance for the voting process and that ballots are correctly counted, providing the necessary controls to detect and correct any anomalies."
Moving forward
Many state, local and city governments are shifting their most critical technology online, and in time that may include election systems.
"I'd love it if by 2024, the election in North America and the U.S. is something that could be done online," Kerrest said. "We need to have technology in place to secure results of the election and this is where identity solution comes into play. These things should all be open sourced anyway. People should be able to look at the code so we can be aggressive about cybersecurity. Aggressive about privacy. There are good ways of doing this as a group -- a lot of examples we can lean on."
The key, many security experts said, will be establishing a better working relationship between voting system vendors and security researchers. While constructive conversations between the infosec community and voting vendors are moving in a more positive direction, they still need work, Grant said.
"If we can't do it today, we can at least lay out that this is something we want and make a list of very real concerns that are out there and start to think about constructive ways to address them," he said."[But] as long as the two sides are at an adversarial role with each other, we're not going to make it anywhere."







