
Twin - stock.adobe.com
Snake ransomware poses unique danger to industrial systems
The new ransomware family known as Snake, or Ekans, is designed for organizations with industrial control systems and has already struck at least two enterprises.
While ransomware continues to be a major threat to enterprise IT environments around the world, a new family of ransomware poses a unique danger to companies with industrial control systems.
Snake, also known as Ekans ("snake" spelled backward), follows the classic ransomware formula of encrypting most files on the target network and then charging a ransom to decrypt said files. But what makes Snake unique is that instead of targeting Windows and Linux IT systems like most enterprise-focused ransomware, Snake targets industrial control systems (ICS). Despite this, the threat actors behind Snake are using some of the same techniques as other ransomware groups -- using exposed Remote Desktop Protocol (RDP) instances with weak passwords to gain entry into ICS environments and spread the ransomware.
Snake ransomware was first revealed by threat researchers at endpoint security vendor SentinelOne earlier this year, who observed "target campaigns" against organizations with industrial control and SCADA systems. Two industrial companies were reported to have been hit by Snake in recent weeks: car manufacturer Honda and European power company Enel Group.
Neither Honda or Enel Group confirmed Snake was the type of ransomware that infected their respective systems; however, an independent security research uploaded samples of Snake to VirusTotal that include domains belonging to the two companies. Honda provided the following statement to SearchSecurity regarding the attack.
"Honda has experienced a cyberattack that has affected production operations at some U.S. plants. However, there is no current evidence of loss of personally identifiable information. We have resumed production in most plants and are currently working toward the return to production of our auto and engine plants in Ohio," the statement read.
According to an official statement provided to media by Enel, the power company also recovered from the attack quickly with no customer data released to third parties.
Sophos senior threat researcher Sean Gallagher said Snake has broadened the ransomware threat landscape.
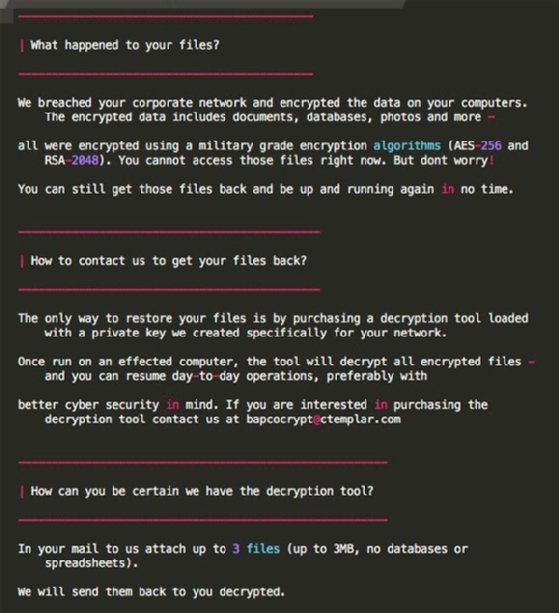
"Ekans adds the additional dimension of attacking industrial control systems, so it places not just back-office but actual manufacturing and production operations at risk as well. While this capability in Ekans is somewhat limited, it could still be harmful to companies that have integrated IT and OT [operational technology] networks. The best way to prevent this is to keep industrial controls on a dedicated network, partitioned from corporate systems and the internet, and to protect all systems based on commercial operating systems with backups and endpoint protection," Gallagher said.
Kirill Kruglov, senior security expert at Kaspersky, said that Kaspersky has seen four organizations with confirmed Snake attacks.
"So far, we have seen four organizations attacked, but multiple targets were attacked in different countries. Since we cannot yet see the full picture, we believe the actual number of organizations attacked could be bigger. We've seen attacks in China, Japan and Germany. In all the cases we are aware of, when the attacked computer was protected by our product, the attack was blocked proactively. But as we know, not all computers in ICS environments are fully protected because of various reasons, so we cannot state that the attack was totally stopped in all the attacked organizations. The computers that do not have sufficient protection in place could potentially have been encrypted by the malware," Kruglov said.
Jim Walter, security researcher at SentinelOne, said that while Snake ransomware is unique because it's designed for ICS, the exploitation methods used by threat actors are similar to those used by other traditional ransomware groups.
"Multiple SNAKE/EKANS campaigns have used exposed and vulnerable RDP servers as the delivery/entry point. Understanding where your ingress points are and hardening them appropriately is one step in the right direction. Any outward exposed host or service should be running the absolute minimum necessary services to decrease the attack surface," Walter said via email.
A number of threat actors and ransomware groups have been setting their sights on exploiting RDP weaknesses over the last year -- particularly during the pandemic.
He also noted that Snake attacks are not "quick 'in-and-out' scenarios." They can take weeks or months, and the process of exfiltrating data prior to a ransomware launch will take the most amount of time, especially since criminal outfits can harvest terabytes of data depending on the target. "But this is also good news for defenders," Walter explained. "If you have full visibility into the exposed ingress points, you can see these types of activities unfolding over time."
Beyond this, Walter said, good cybersecurity hygiene goes a long way. He recommends users be hyper critical when opening messages, following links, and opening attachments, as email and phish delivery is "still the #1 method for distributing malware."







