
Repeat ransomware attacks: Why organizations fall victim
Some organizations get hit with ransomware multiple times. Threat researchers explain why repeat attacks happen and how victims can prevent it from occurring again.
Getting hit with ransomware once is a nightmare for any organization, but for some enterprises and governments it's been a recurring nightmare.
Repeat ransomware attacks have become a common occurrence in recent years. According to a 2017 report from data protection vendor Druva, 50% of the 832 IT professionals surveyed said their organization had been hit with ransomware multiple times. In its 2018 global survey of 2,700 IT managers, endpoint security vendor Sophos found that most organizations suffered multiple attacks with the average number being two per year.
It's unclear how many organizations have suffered multiple attacks, as enterprises often decline to publicly disclose ransomware incidents. However, in recent weeks some enterprises have disclosed repeat attacks. Two such enterprises include Toll Group, an Australian logistics company, and Pitney Bowes, a shipping technology company; both were hit most recently in May.
Threat researchers say there are several causes behind such incidents, ranging from poor cybersecurity postures and lingering vulnerabilities to persistent threat actors that maintain access to victims' environments after the first attack.
Poor cybersecurity posture
John Shier, Sophos senior security advisor, told SearchSecurity the reason some organizations get hit with ransomware multiple times is deceptively simple. "In most cases, it's simply a matter of not fixing the underlying issues that led to the original breach," Shier said via email. "This is especially true in the case of opportunistic attacks. If you have Internet-facing computers that are unprotected or vulnerable, they will be found and abused."
Toll Group, for example, was hit by ransomware twice in three months. The two incidents were not connected, a spokesperson for Toll Group told SearchSecurity, and were "based on different forms of ransomware." The latter attack, which happened in May, involved Nefilim, a relatively new variant of ransomware.
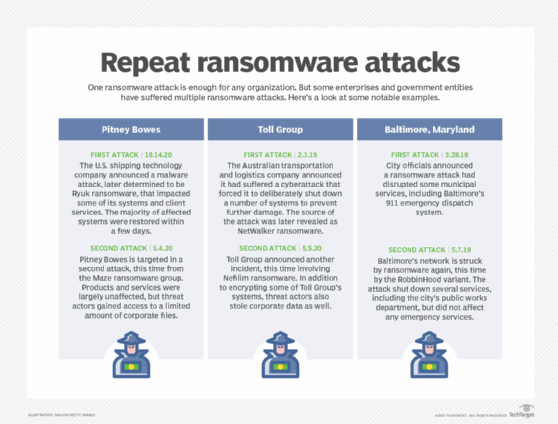
Repeated ransomware attacks can also vary in terms of effect. Pitney Bowes was hit twice in seven months -- once in May, and once this past October. Last year's Ryuk ransomware attack, according to the company's public statement, encrypted "some systems" on Oct. 12 and caused disruption to company services. "We have restored the majority of our operations and services to our clients globally. Again, we've seen no evidence that client or employee data has been improperly accessed from the Pitney Bowes network globally. In consultation with our security advisers we do not believe clients or employees are at risk," the statement read.
But in May, Pitney Bowes revealed the second incident involved Maze ransomware. The company was able to detect the hackers and prevent the ransomware from executing.
"Recently, we detected a security incident related to Maze ransomware. We are investigating the scope of the attack, specifically the type of data that had been accessed, which appears to be limited. Working with our third-party security consultants, we immediately took critical steps to thwart the attack before data could be encrypted. At this point, there is no evidence of further unauthorized access to our IT systems. The investigation remains ongoing," the company's statement read.
It's unclear how new threat actors were able to gain access to Pitney Bowes and Toll Group's environments, but Raj Samani, McAfee fellow and chief scientist, offered the following perspective.
"Those organizations that get hit multiple times are likely those that do not secure their systems. Typically, ransomware groups, and particularly those groups that target businesses (and can therefore demand high ransoms) exploit common security oversights," he said. "Failure to address these common oversights will likely result with infection, and then re-infection."
It's also not uncommon for multiple threat groups to have simultaneous access to the same network. "Sophos recently investigated a ransomware attack where two separate groups had gained independent access to the same company's network," Shier said. "One gang waited patiently for the other to complete their actions before they struck a second time."
Persistent threat actors
While many security experts point to weak security postures, others, like Emsisoft threat analyst Brett Callow, point to situations where backdoors are created that allow continued access. In the ransomware attack involving the Colorado Department of Transportation (DoT), threat actors maintained their access with Trickbot after infecting the DoT. Luckily, the incident response team was able to detect the Trickbot infection during the forensic investigation, which likely prevented another attack.
"While it's unusual for companies to be hit by ransomware more than once, it's certainly not without precedent. In some cases, it's simply coincidental, but in most it is not. Actors frequently create backdoors to provide them with continued access to the network post-incident. The backdoors are typically 'owned' by affiliates who may change allegiance or sell or trade them with other groups," Callow said. "Consequently, a successful attack by one group could potentially result in a successful attack by another. This is one of the reasons that we strongly recommend that companies rebuild their networks after a ransomware incident rather than simply decrypting their data."
Avoiding repeat attacks
Shier said that there is no hard-and-fast rule for who is most likely to get hit multiple times, and that the majority of attacks start opportunistically. However, he said, "many businesses are still ill-equipped to deal with a ransomware attack. Local governments and healthcare organizations are particularly vulnerable due to lack of resources (both people and product), and the reporting requirements that regulate them make it seem like the problem is much more disproportionate. Small businesses are just as likely to get hit as large ones, but the ability to recover is not proportional."
Then there's the question of how an organization can prevent ransomware from happening again.
"Understanding the root cause of a ransomware attack is of paramount importance. Importantly, the root cause might not have been ransomware -- it was just the most visible. In many cases, ransomware is the byproduct of another undetected infection. Investigating and remediating the underlying cause of any cyberattack is crucial to preventing subsequent attacks," Schier said. "Implementing modern endpoint security software will help prevent future attacks, but so will ensuring that other controls, like backups, are in place to provide additional recovery capability against novel attacks."
Samani, meanwhile, said defending against ransomware and all cyberattacks is an ongoing process. "Continuously ensuring that an organization has secured their environment is essential," he said. "There is no point in only doing this after an attack, but there has to be mechanisms to ensure that the environment is continuously monitored to ensure that the organization is not exposed."






