
zephyr_p - stock.adobe.com
New 'Thanos' ransomware weaponizes RIPlace evasion technique
Recorded Future's Insikt Group uncovered a new ransomware-as-a-service tool named 'Thanos' that's the first ransomware to use the hard-to-detect RIPlace technique.
Threat researchers at Recorded Future discovered a new ransomware-as-a-service tool, dubbed "Thanos," that is the first to utilize the evasion technique known as RIPlace.
Thanos was put on sale as a RaaS tool "with the ability to generate new Thanos ransomware clients based on 43 different configuration options," according to the report published Wednesday by Recorded Future's Insikt Group.
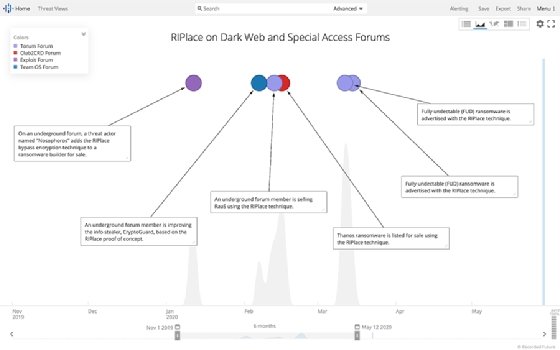
Notably, Thanos is the first ransomware family to advertise its optional utilization of RIPlace, a technique introduced through a proof-of-concept (PoC) exploit in November 2019 by security company Nyotron. At its release, RIPlace bypassed most existing ransomware defense mechanisms, including antivirus and EDR products. But despite this, the evasion wasn't considered a vulnerability because it "had not actually been observed in ransomware at the time of writing," Recorded Future's report said.
As reported by BleepingComputer last November, only Kaspersky Lab and Carbon Black modified their software to defend against the technique. But since January, Recorded Future said, "Insikt Group has observed members of dark web and underground forums implementing the RIPlace technique."
According to its report on RIPlace, Nyotron discovered that file replacement actions using the Rename function in Windows could be abused by calling DefineDosDevice, which is a legacy function that creates a symbolic link or "symlink."
Lindsay Kaye, director of operational outcomes for Recorded Future's Insikt Group, told SearchSecurity that threat actors can use the MS-DOS device name to replace an original file with an encrypted version of that file without altering most antivirus programs.
"As part of the file rename, it called a function that is part of the Windows API that creates a symlink from the file to an arbitrary device. When the rename call then happens, the callback using this passed-in device path returns an error; however, the rename of the file succeeds," Kaye said. "But if the AV detection doesn't handle the callback correctly, it would miss ransomware using this technique."
Insikt Group researchers first discovered the new Thanos ransomware family in January on an exploit forum. According to the Recorded Future report, Thanos was developed by a threat actor known as "Nosophoros" and has code and functions that are similar to another ransomware variant known as Hakbit.
While Nyotron's PoC was eventually weaponized by the Thanos threat actors, Kaye was in favor of the vendor's decision to publicly release RIPlace last year.
"I think at the time, publicizing it was great in that now antivirus companies can say great, now let's make sure it's something we're detecting because if someone's saying here's a new technique, threat actors are going to take advantage of it so now it's something that's not going to be found out after people are victimized. It's out in the open and companies can be aware of it," Kaye said.
Recorded Future's report noted that Thanos appears to have gained traction within the threat actor community and will continue to be deployed and weaponized by both individual cybercriminals and collectives through its RaaS affiliate program.







