
alphaspirit - Fotolia
GitHub security features tackle data exposures, vulnerabilities
In in effort to curb accidental data exposures in repositories, GitHub unveiled a new 'secret' scanning tool that examines public and private code repositories for sensitive data.
GitHub Wednesday unveiled new security features aimed at addressing software vulnerabilities and accidental exposures of confidential data.
During the GitHub Satellite 2020 virtual event, the cloud-based software development platform announced two new security services in beta: code scanning and "secret" scanning. Grey Baker, director of product management at GitHub, told SearchSecurity the scanning tools are part of a concerted effort to improve security features, which began with the company's acquisition of Semmle, a code analysis vendor, in September.
Code scanning, which is now available as a native tool for GitHub, automatically scans software upon being uploaded to a repository and alerts organizations about any potential security flaws in the code.
"We've been doing a lot of work in security over the last few years," Baker said. "Now we're moving from making it easier to react to vulnerabilities to making it easier to prevent those vulnerabilities in the first place."
Baker highlighted a recent example with Uber. The ride-sharing company received a report of a critical vulnerability through its bug bounty platform, and after running the code scanning feature (which has been rolled out to some GitHub Advanced Security customers), Uber's security team discovered 11 other instances of the vulnerability in its systems. Rob Fletcher, head of application security at Uber, said in a press statement that the discovery led to "significant cost savings" for the company.
In addition, Baker said customers can open source and share their scanning queries so that other organizations can use them to find similar vulnerabilities and flaws in their own code. "It makes security feel like more of a collaborative endeavor, and that's part of our vision," he said.
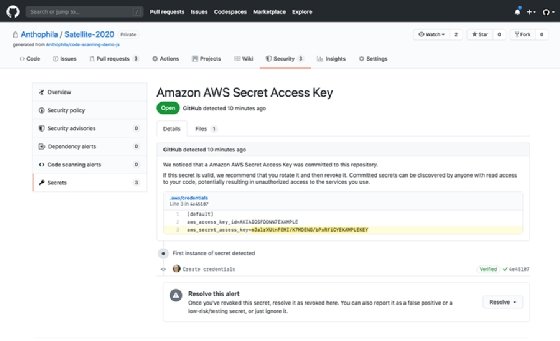
Scanning for secrets
Secret scanning was formerly known as token scanning and available to all public repositories since being introduced in 2018, but the tool was revamped and will be made available to all private repositories as well. In addition to searching for potentially exposed authentication tokens, the tool also looks for other types of file formats and confidential data.
Baker said the features were designed to prevent incidents like the AWS' accidental exposure of private encryption keys and customer credentials in a public GitHub repository earlier this year. He added that while making GitHub repositories private can reduce exposures, it doesn't fully eliminate leaks.
"Even if your repo is private, I don't think you want everyone in the entire company having access to private keys," he said.








