
lolloj - Fotolia
Threat hunting technology is on the rise, so are threats
Detection of advanced threats is the top challenge for 55% of security operations centers, according to a new survey, as more companies explore threat hunting programs.
More companies are adopting threat hunting functions, according to a recent survey from Crowd Research Partners, but detection of advanced threats remains elusive.
Threat hunting typically involves human security analysts identifying impending incidents or attacks that automated threat detection systems may have missed. The frequency of threats and the potential damage and impact of security incidents continue to outpace the capabilities of security operations centers (SOC), Crowd Research Partners' "2018 Threat Hunting Report" found.
Fifty-eight percent of IT security professionals said cyberthreats against their organizations had doubled during the past 12 months; only 8% indicated threats decreased. SOCs, on average, missed 39% of threats, with the majority of attacks discovered in one to seven days for 58% of organizations. The average dwell time for attackers was 30 days.
The top challenges facing SOCs, according to those surveyed, included the following:
- detection of advanced cyberthreats -- hidden, unknown and emerging threats (55%);
- lack of skilled personnel (43%);
- lack of confidence in threat detection technologies (36%);
- too much time wasted on false alerts (35%);
- slow response time to find or detect advanced threats (31%);
- outdated SIEM and SOC infrastructure (29%); and
- lack of proper reporting tools (28%).
In order to offset some of these challenges, the report found that approximately one-third of the organizations surveyed had outsourced threat hunting to a managed security service provider.
Crowd Research Partners conducted an online survey of more than 461 security and IT professionals in the Information Security Community group on LinkedIn. The survey features respondents from industries such as technology (17%); financial services, banking and insurance (14%); telecommunications (6%); and healthcare (5%). Government cybersecurity professionals represented 20% of those surveyed.
Mix of analysts and tools
According to the survey, 40% of respondents reported that security analysts at their organizations used threat hunting platforms, up 5 percentage points from a similar survey in 2017. Benefits ranged from improved detection of advanced threats to less time spent coordinating events. The top indicators of compromise most frequently investigated by security analysts included behavior anomalies (67%), IP addresses (58%), domain names (46%), denied or flagged connections (46%) and file names (32%).
Security operations centers had more analysts hunting in 2018, at 17%, compared with 14% in 2017. More than half, however, have five or fewer analysts in their SOCs dedicated to threat hunting, the report found.
While security operations centers at some organizations are maturing, along with a greater awareness of threat hunting, 33% of those surveyed indicated limited SOC capabilities when it came to emerging threats; 28% said their SOC was advanced; 24% reported it was compliant, but behind the curve; and only 15% said their SOC was cutting-edge.
Companies used a variety of tools for threat hunting. The top technologies included the following:
- next-generation firewalls, intrusion prevention systems and antivirus software (55%);
- SIEM (50%);
- antiphishing or other messaging security software (49%);
- threat intelligence platforms (39%);
- enrichment and investigation tools (34%); and
- vulnerability management (32%).
The majority of threat hunting was performed in-house (56%). Some companies used a hybrid of in-house and service provider (22%); others outsourced threat hunting (11%). Meanwhile, 11% of survey respondents reported that their organizations did "no proactive threat hunting."
Security analysts at 60% of the organizations said they do not currently use threat hunting platforms or techniques. However, six out of 10 organizations indicated plans to build a threat hunting program in the next three years, according to the "2018 Threat Hunting Report," which is produced in partnership with multiple vendors.
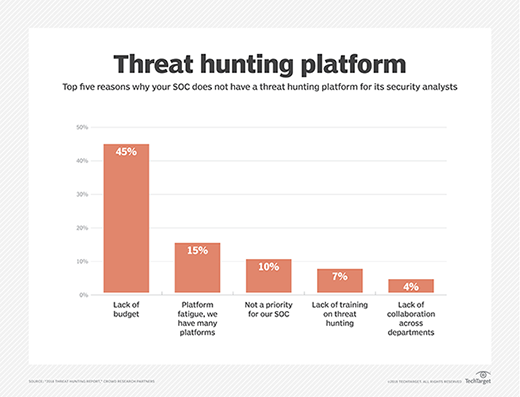
Barriers to adoption ranged from lack of budget (45%) to untrained personnel (7%). The tools desired most often for threat hunting included threat intelligence (69%), user and entity behavior analytics (57%), automatic detection (56%), and machine learning and automated analytics (56%).
According to proponents of threat hunting programs, such as David Bianco, who served as a technology adviser for Sqrrl Data Inc., before the startup company was acquired by Amazon Web Services earlier this year, one of the benefits is security teams can take what they find and use it to improve automated detection.







