
lolloj - Fotolia
Ransomware threat tops Verizon Data Breach Report
After years of climbing the ranks in the Verizon Data Breach Investigations Report, the ransomware threat has finally taken the top spot as the most prevalent malware type.
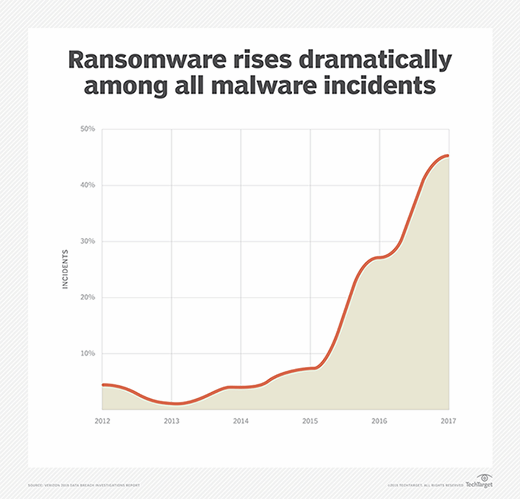
Ransomware is finally king of the hill -- albeit an ignominious hill -- as the most prevalent type of malware found in attacks, according to the 2018 Verizon Data Breach Investigations Report.
In the 2014 Verizon DBIR, the ransomware threat ranked as the 22nd most common malware type in data breaches. In 2017's DBIR, ransomware had jumped up to the fifth most common type of malware. Now, in the 2018 Verizon DBIR, ransomware has ascended to the top of the list.
Verizon gathered data from 67 contributing organizations in 65 countries that reported more than 53,000 incidents and more than 2,200 breaches in 2017. After parsing the data, Verizon found that 39% of data breaches involving malware used ransomware, which was double the proportion of the ransomware incidents year over year. According to the DBIR, the growth of the ransomware threat shouldn't be much of a surprise because the attack requires "little risk or cost to the adversary involved," doesn't require monetizing stolen data and is versatile enough to be deployed across many devices or in targeted attacks.
Itsik Mantin, lead scientist at Imperva, agreed that the "flourishing of ransomware is anything but surprising."
"In recent years we've seen the ransomware economy going through industrialization, allowing attackers to build ransomware campaigns from building blocks they purchase or obtain in darknet forums, with the leading infection vector of 2017 being with no doubt EthernalBlue that was used in several ransomware campaigns like WannaCry," Mantin told SearchSecurity.
James Stickland, CEO of Veridium, said the ransomware threat is unlikely to go away because "the cracks are Grand-Canyon-sized in enterprise security patching and architecture."
"Data is king, and what enterprises fear is losing client data or intellectual property, all of which will continue to be held to ransom," Stickland told SearchSecurity. "Many hacks have provided access to data that was of little or no value, but with access comes brand disruption and trust. It's easy pickings, unless data is segregated, and policies enforced with the keys to the doors; well-guarded."
Pretexting and phishing
Beyond the ransomware threat, Verizon found social attacks were still working well for malicious actors. pretexting was an issue Verizon highlighted in the 2017 DBIR as a threat on the rise, and the attack method nearly tripled over the past year, going from 61 incidents in the 2017 report to 170 this year.
"One of the differences between pretexting and phishing events is the lack of reliance on malware installation in the former for the attacker to meet their end goal," Verizon wrote. "Malware was found in less than 10% of incidents that featured pretexting in contrast to phishing incidents where malware was present over two-thirds of the time. So, pretexting is less about gaining a foothold and more about acquiring information directly from the actions taken by the target."
According to Verizon, there can be a gray area in splitting pretexting from phishing so the telecom giant decided to classify pretexting cases as incidents where there was a dialogue between attacker and target with the intent of obtaining information or influencing behavior. Alternatively, a campaign mainly aimed at baiting users into clicking a malicious link fell into the phishing category.
Despite the lack of malware in pretexting schemes, Verizon found 114 confirmed data breaches from the 170 incidents reported last year, 95% of which were financially motivated. The success rate for threat actors wasn't as high with phishing (1,192 incidents, 236 confirmed data breaches), but the DBIR noted the motivation of these schemes was "split between financial (59%) and espionage (41%)."
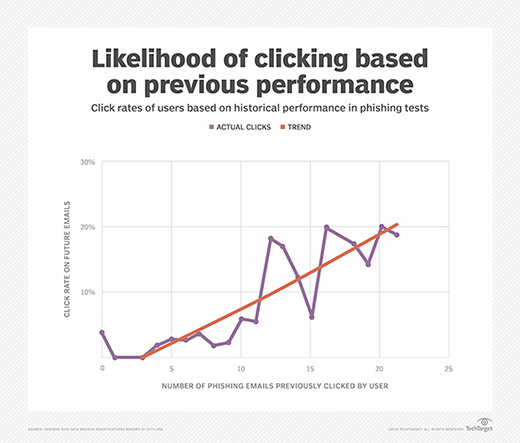
Verizon tried to find a silver lining in the phishing data by noting that 78% of people don't click a phishing link all year. However, Verizon quickly reasserted the dark cloud. "Unfortunately, on average 4% of people in any given phishing campaign will click it, and the vampire only needs one person to let them in," the DBIR report stated.
Verizon also noted that although only 4% of people may click a phishing link, that trouble is exacerbated because those who clicked phishing links were more likely to click again in the future. Worse, "only 17% of phishing campaigns were reported."
Stickland suggested people might be wary of reporting phishing attacks because of embarrassment.
"If there was less [of a] stigma on phishing that you have been duped, then I think there would be more reports," Stickland said. "Reduce the negative feeling and create a nonjudgmental armistice on phishing. That way, more people will report."
Richard Ford, chief scientist at Forcepoint, said it's important to let people be people.
"That doesn't mean that I should go around clicking like a madman with no training from the IT team but I also have sympathy for those employees who are not computer security experts and who make mistakes. I like to think of it as safety, not security, where we are the crash barriers that are in place for when things inevitably go wrong," Ford said. "Phishing protection is table stakes at the security game today. Everyone should be using it, and it should be turned on pretty aggressively company-wide, regardless of how users tend to act. Anyone can make a mistake, and your defenses should be ready for that."
The following organizations contributed to the Verizon DBIR 2018 (* indicates new contributor):
Akamai Technologies
Arbor Networks
AsTech Consulting
AttackIQ*
BeyondTrust
BitSight*
Bit-x-bit*
Center for Internet Security
CERT/CC*
CERT Insider Threat Center
Champlain College's Senator Patrick Leahy Center for Digital Investigation
Check Point Software Technologies
Chubb
Cisco Security Services
Computer Incident Response Center Luxembourg (CIRCL)
CrowdStrike
Cybercrime Central Unit of the Guardia Civil (Spain)*
CyberSecurity Malaysia, an agency under the Ministry of Science, Technology and Innovation (MOSTI)
Cyentia Institute*
Cylance
Dell*
DFDR Forensics
Digital Edge*
DSS*
Edgescan*
Emergence Insurance*
Fortinet
G-C Partners*
GRA Quantum
Graphistry*
Grey Noise*
Industrial Control Systems Cyber Emergency Response Team (ICS-CERT)
Interset
Irish Reporting and Information Security Service (IRISS-CERT)
ICSA Labs*
Japan Computer Emergency Response (JPCERT/CC)
Kaspersky Lab
KnowBe4
Lares Consulting
LIFARS
Lookout*
Malicious Streams*
McAfee
Mishcon de Reya
MWR InfoSecurity
National Cybersecurity and Communications Integration Center (NCCIC)
NetDiligence
OpenText (formerly Guidance Software)*
Palo Alto Networks
Proofpoint*
Pwnie Express
Qualys
Rapid7
S21sec
Social-Engineer Inc.
Swisscom
Tripwire
U.S. Secret Service
U.S. Computer Emergency Readiness Team (US-CERT)
VERIS Community Database
Verizon DoS Defense
Verizon Network Operations and Engineering
Verizon Professional Services*
Verizon Threat Research Advisory Center*
Vestige Ltd
Winston & Strawn LLP
Zscaler*
Bob Rudis, chief data scientist at Rapid7, said a big issue with phishing reporting is friction.
"The easier it is to report phishing campaigns, the more likely an individual will do so. Even having a forward address can provide sufficient friction to thwart even the most intrepid employee. If possible, adding a button to email clients that support customization to make it dirt simple to report phishing will definitely drive up response rates," Rudis told SearchSecurity. "The gamification route can also reap rewards. Develop leaderboards, badges, et cetera and tap into the dopamine reactions video games and social media platforms do to keep people invested in helping secure your organization."
Random findings and a word on bias
Regardless of whether an enterprise is dealing with a ransomware threat or another attack method, the Verizon DBIR noted that response times continue to lag well behind an attacker's speed in exfiltrating data.
"When breaches are successful, the time to compromise continues to be very short. While we cannot determine how much time is spent in intelligence gathering or other adversary preparations, the time from first action in an event chain to initial compromise of an asset is most often measured in seconds or minutes. The discovery time is likelier to be weeks or months," Verizon wrote in the report. "The discovery time is also very dependent on the type of attack, with payment card compromises often discovered based on the fraudulent use of the stolen data (typically weeks or months) as opposed to a stolen laptop which is discovered when the victim realizes they have been burglarized."
The Verizon DBIR also tried to debunk some common misconceptions, such as the idea that DDoS attacks are often used as cover for other malicious activity.
"This year's dataset only had one breach that involved a DoS, and in that one, the breach was a compromised asset used to help launch a DDoS, not the other way around," Verizon wrote. "In fact, we've never had a year with more than single-digit breaches in the Denial of Service pattern. Like the aliens, they may be out there, but we aren't seeing them."
Lastly, Verizon admitted in the report that there could be sampling bias with its DBIR data because the company doesn't know the total number of data breaches across all organizations in a year and many breaches are either unreported or never detected. Verizon has admitted this in the past but still asserts the DBIR contains valuable data, especially for industry-specific threats.
Mantin said he believes the Verizon DBIR is "strongly biased towards noisy attacks, and deprives other threats like data theft and recruitment of hijacked machines to variety of purposes like cryptomining and joining a botnet."
"As opposed to data theft, ransomware is a noisy attack, noticed by the victim in 100% of the cases. The majority of the data theft attacks go undetected without the victim knowing he or she was attacked -- a fact that holds for both insider and external data breaches," Mantin said. "Thus, even if from the victim's perspective, ransomware is the most prevalent attack, and this victim may not know he or she has five hidden malwares crawling in his organization, collecting and exfiltrating stolen data, collecting credentials and taking over machines, and maybe few hundred of an organization's desktops might be mining crypto-currencies for anonymous accounts, or waiting for command to join a DDoS attack on a joint target."





