Information Security
- Editor's letterWhat a proactive cybersecurity stance means in 2019
- Cover storyBattling nation-state cyberattacks in a federal leadership vacuum
- InfographicCutting SecOps breach response time is key to success
- FeatureTop 10 CISO concerns for 2019 span a wide range of issues
- ColumnCISO tackles banking cybersecurity and changing roles
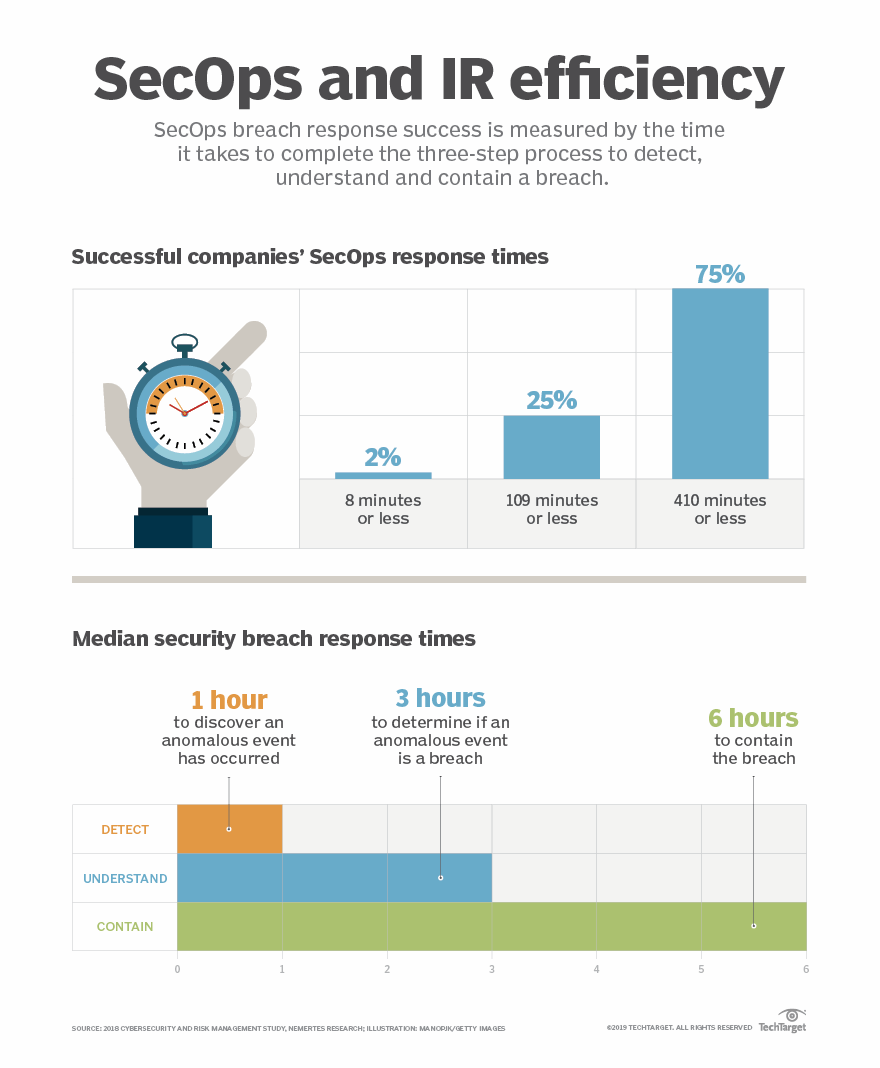
Cutting SecOps breach response time is key to success
A new survey measures the success of security operations breach response by how long it takes to complete a three-step process to detect, understand and contain incidents.Many companies measure the success of their security operations by how many threats their systems thwart. But even if 95% are stopped, what about the 5% that do get through? A more effective measure of SecOps maturity is how long it takes to detect, understand and contain breaches that actually happen, said Nemertes Research CEO Johna Johnson.
Security teams must address three phases in sequence to gauge their SecOps success: detect an event that may be good or bad, determine whether the event is an actual attack and seal off the affected system.
After talking to leaders at 625 companies in 12 countries, the Nemertes 2018 Cybersecurity and Risk Management Study revealed vast differences in the time it takes SecOps teams to contain breaches. The top 2% of companies -- primarily financial services, aerospace companies and a few major universities -- can accomplish all three steps in 8 minutes or less. But many organizations take days, weeks or even months to analyze and address a threat, Johnson said.