
PiChris - Fotolia
Words to go: Types of phishing scams
IT teams must take proactive measures to address security awareness when it comes to email. Learn about the types of phishing scams to mitigate risk.
IT professionals know the stakes are high when it comes to email phishing security. Phishing is deceptively dangerous because suspicious links are hyperlinked within email text and can be hard to distinguish as dubious by an untrained eye. It takes only one click to affect or even compromise the whole network. This is complicated by the fact that many types of phishing scams are not easily eliminated by software alone. It takes a combination of threat detection systems, security awareness training and a vigilant security team to create a solid defense against phishing threats.
Given the ubiquity of email as a communications channel at enterprises around the world, it's easy to imagine email as an attractive attack method to hackers. Email security must keep up with the potential for phishing attacks in a changing world, where mobile devices are becoming more popular in the enterprise and phishing becomes more sophisticated through social engineering. Refer to this list of email phishing security terms to avoid complacency when it comes to email security in the enterprise.
Phishing test. To minimize risk from phishing attacks, organizations may implement an email phishing test. This involves distribution of a harmless email spoof to employees, usually engineered by IT within the organization. The email poses no actual risk to employees, but it serves to identify who does and doesn't understand email phishing security. IT is supplied with information on how users interact with the email.
Of course, real email phishing can harm the organization, but a test phishing email identifies areas of weakness in education and email security awareness. Email phishing security test results may necessitate training among the staff if it is discovered that individuals lack the expertise needed to identify potential phishing risks.
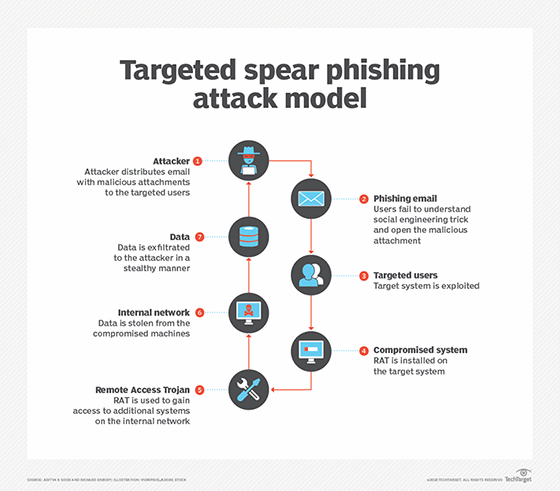
Spear phishing. A spear-phishing attack is a type of email spoofing designed to look like it was sent from a user's manager within an organization. The intent of spear phishing is often to acquire critical information, such as trade secrets or client information. Because perpetrators typically initiate attacks for specific financial or strategic gain, they are usually not random hackers.
Unsuspecting targets may be fooled by name recognition of trusted names or brands. Spear-phishing attacks target a particular person or group of people, usually low-level to midlevel employees. This makes it different from other types of phishing scams that are characterized by mass email distribution to an indiscriminate pool of users.
Whale phishing. A whale phishing incident is a type of phishing scam that targets high-level company executives, like CFOs or CEOs. The term whaling is used to describe the size of the attack. Whaling targets are larger authorities within the organization. Attackers often intend to steal sensitive information from the organization. Employees in high-level positions have the most access to this critical data, which makes them natural targets in this type of phishing attack.
Whale phishing creates email messages that look like they are from a trusted brand or client to manipulate the victim into enacting wire or data transfers to the attacker, for example. These email messages are branded with personal or professional information pertinent to the target -- such as job title, name or other details -- gleaned from a variety of sources via social engineering. The level of personalization provides the victim with a false sense of security.
Social engineering. Social engineering is an attack vector used by threat actors to present themselves as trusted individuals or sources. This attack vector requires research on the target. The attacker may mine personal information on employees from public social media accounts and other intelligence on employee structure.
Attackers manipulate people in the organization into breaking understood security procedures and policies, often preying on the person's intention to be helpful. For example, attackers may identify themselves to a target as a known peer or co-worker in crisis who urgently requires sensitive data or access to a network. Social engineering attacks are often the preliminary step in a coordinated campaign to infiltrate the network or distribute malicious software.
Insider threat. An insider threat describes a threat to data or other security from within the organization, most likely from an employee or former employee. Customers, contractors or temporary staff can also pose an insider threat. Insider threats are categorized as either malicious or accidental.
Insider threat damage can come in many forms, including the theft of important information, financial fraud, identity theft, and data corruption or deletion. It can also introduce malware to the system through a virus, worm or Trojan horse. Cybersecurity awareness training is used to prevent accidental insider threats. IT professionals use spyware scanning programs, firewalls and antivirus programs as defense mechanisms against insider threats.
Mobile phishing. Under many circumstances, employees can access organizational networks with a mobile device. Increased use of mobile devices in the enterprise presents a unique email security risk called mobile phishing. One critical difference from other types of phishing is that users may preview an email on a traditional desktop or laptop computer by hovering over an email with a mouse. This ability sometimes alerts email users to the threat of email phishing scam. This function is not available on a mobile device, however.
Year after year since 2011, the number of users who receive and select mobile phishing URLs has grown by 85%, according to mobile threat defense vendor Lookout. Once the phishing email reaches the device endpoint, users themselves are the ones making security decisions, not IT. IT needs to account for this changing reality and implement email filtering and endpoint protection.






