Third-party risk management: Horror stories? You are not alone
The majority of breaches occur as the result of third parties. MacDonnell Ulsch advises companies to safeguard third-party management agreements.
Cyberattacks leap from the headlines almost daily, yet senior management at some companies still believe their organizations are not potential targets: “Nobody knows who we are, why would anyone want to attack us?”
One consistent breach finding may get their attention: Almost without exception, a third-party vendor or affiliate is involved. It may be the client, or it may be the origination point of the breach.
The third party is often a quasi-insider, enjoying some degree of the trust afforded employees. Based on a relationship’s longevity and personal interactions, third-party trust levels sometimes meet or exceed the level of insider trust.
Unfortunately, the conveyance of trust does not always end well. This is why third-party management and service-level agreements (SLA) are so critical in the management of risk. SLAs are negotiable instruments that reflect the company’s appetite or tolerance for risk; its size and complexity, geographic distribution, type of information managed, as well as the ability to effectively monitor the third-party management program.
Already made in China
When it comes to managing risk, no company is perfect; usually, it’s far from it. In the well-known case of Nortel Networks Inc., the optical networking company’s computer systems and senior management’s emails— including the CEO’s—were compromised by Chinese hackers, for nearly a decade. An employee said he alerted Nortel’s executives that there was a breach in 2004, according to The Wall Street Journal, but outside of changing passwords, his warnings were largely ignored. This ongoing breach resulted in costly and complex litigation during Nortel’s asset sale after it declared bankruptcy in 2009. Companies that acquired Nortel’s intellectual property—Ciena Corp., Avaya Inc. and Ericsson Inc.—found out that their organizations might not have “exclusive rights” to the sensitive information.
Avoiding the often substantial impact of legal, financial, regulatory and reputation risk isn’t trivial. In the best scenario, managing risk is supposed to prevent bad things from happening. The next best outcome is to reduce the impact when a collision of a threat and its intended target prove unavoidable. In the worst case, managing risk is about recovering from an event that proved to be, for whatever reason, both unpreventable and highly effective, translation: expensive.
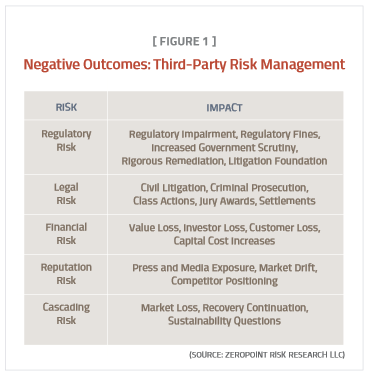
Risk impact can be defined by a variety of metrics: loss of revenue, loss of company value, diminished market share and brand equity, increased cost of capital, higher insurance premiums and civil litigation from investors, shareholders, business partners and others (see Negative Outcomes: Third-Party Risk Management—Figure 1). Heads may roll in the executive suite. Criminal prosecutions often result. (Immunity in a breach is as scarce as hieroglyphics.)
The worst risk impact occurs when companies are clearly not ready for a breach, which is too often the case. The majority of breaches occur as the result of the actions or defensive deficiencies associated with a third-party service provider. One third-party vendor’s deficient antimalware deployment resulted in a massive cyberattack. The impact: extensive, costly regulatory reporting and uncomfortable discussions and negotiations with its corporate customer base. The breach was detected when an employee noticed suspicious firewall log activity. The hackers, however, had covered their infiltration by erasing the majority of their intrusive activities, making the breach even worse and complicating the forensic analysis.
Compliance and third-party management agreements
Third-party management agreements are important instruments in managing legal, regulatory, financial and reputation risk. These contracts, also known as Business Associate Agreements (BAA), are neglected tools for defending against information compromise.
Any company protecting health information, for example, needs to pay particular attention to the changes brought about by the HIPAA Omnibus Final Rule, which was passed in January 2013 and went into effect in March. A number of deadlines for compliance are set for September 23, 2013. Changes include requirements for business associates and subcontractors to comply with the complex security rule. Breach notification changes are also noted in the final rule, as well as enforcement and penalty provisions. The Genetic Information Nondiscrimination Act prohibits health plans from using genetic information as an underwriting consideration. Multiple privacy issues are also noted in the final rule, especially on the use and disclosure of protected health information, including the uses associated with marketing and fundraising. (Similarly, recent changes in the European Union Model Clause affect E.U. companies exporting data overseas, as well as the third-party data importers.)
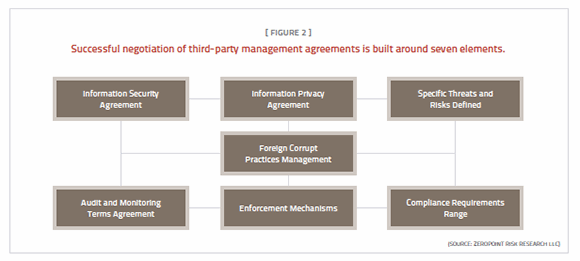
Contract negotiators, attorneys and others with experience managing the SLA process address certain issues reasonably well: performance-related requirements, and even some regulatory requirements. Companies can further protect their information assets by ensuring that the following components are included in the negotiation of all third-party management agreements: information security, information privacy, threat and risk analysis, compliance obligation range, enforcement mechanisms, internal audit access and disclosure requirements, and foreign corrupt practices management (Figure 2). Focusing on these seven elements will increase the efficiency and effectiveness of third-party management agreements while creating an effective risk management framework.
Third-party management agreements may not be enough to protect organizations from elaborate cyberfraud, however. In one occurrence, the third-party vendor hired independent contractor employees who did not exist. Well, one did. Ingeniously, this individual invented identities and acquired cell phone numbers, addresses, social security numbers and so on. On paper, “the employees” certainly seemed like real people—each one passed a background information check. An address in the background check forms seemed out of place, but that didn’t prevent them from getting hired. Personally identifying information (PII) was stolen in this scam and sold to organized crime and narcotics traffickers in a foreign country, resulting in financial fraud. The breach was detected due to suspicious behaviors exhibited by the independent contractor behind the felony crime.
Responsibility and reporting
It is important to remember that the principal company or covered entity that engages a third party is always responsible for ensuring the integrity of information. While various regulations may also hold third-parties accountable, never assume that the obligation of compliance is assignable to another company. When negotiating an SLA, the company must require the third-party service provider to both assume responsibility for compliance with all applicable regulations, and to specify the timeframe in which to report a breach to the company. This can get tricky, and the contract language is important. Always confer with corporate legal counsel on this issue.
First, be sure to define what a breach is. An incident or event is not necessarily a breach of regulation. Is the event a breach of policy and procedure, security or regulation? Some contracts require the third party to notify the principal company of a security policy breach within 24 hours of the incident. Maintaining tight control over the reporting requirements of the third party under agreement is vital. It is also recommended that the company pre-emptively engage the third party by asking, in writing, about any security incidents at the third party, and receive a response in writing.
Assets at risk
It is not always discernible what information is at risk in a cyberbreach, especially right away. One third-party vendor responded to a breach based on an assumption that the organization did not possess any regulated data, when in fact, it did. What the company thought was just a matter of tightening security in the initial stages of the breach, evolved into a serious reportable event.
Every third-party provider should know what data is in its possession. This is an absolutely critical determinant of how that data must be protected. While few mandates exist regarding the protection of intellectual property and trade secret assets—this is typically limited to contractual obligations cited in customer contracts and insurer’s policies— personal information must be protected according to statute and regulation.
Many breaches of regulated data are never reported, however. Sometimes, a decision is reached not to report on the basis that the breach did not meet certain requirements—the exact definition of PII or protected health information (PHI). A breach that isn’t reportable in the United States may be disclosed in other countries based on different regulations.
Managing risk by regulation has significant drawbacks, yet many companies continue to do just that. Here’s the problem. Many regulations are written upon the back of mandatory minimum requirements. While it’s better than nothing (and there are those companies that fail to meet even these basic requirements), it’s not where the industry needs to be. This practice is unacceptable in other industries. No one wants a pilot who’s met only the minimum regulatory threshold.
Baseline for proprietary information
Of course, not all companies or third parties are in the business of managing regulated information. What about managing the risk associated with unregulated data—proprietary information, intellectual property and trade secrets? In a world where brand counts, protecting the brand is ensuring a company’s future. Brand protection is critical because the mission of nation-state espionage and commercial economic and technology competitors is to steal valuable business information. The financial loss is staggering, with some estimates surpassing a trillion dollars a year, and about a third of those losses are in the United States (Figure 3).
One third-party management strategy is to borrow from the requirements used in regulated data management deployments. Most companies, whether large or small, are required to at least protect employee and customer information in a manner consistent with U.S. federal and state requirements. Require third parties to use that baseline to extend protection to intellectual property and trade secrets of value, bearing in mind that this approach, while better than nothing, is a minimum based upon regulatory requirements.
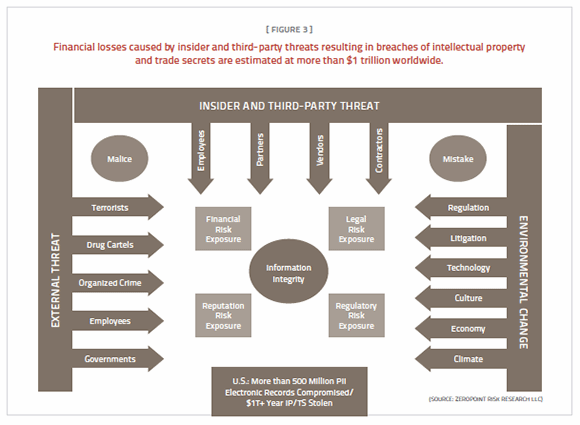
What do all of these breached companies have in common—and especially third parties? It isn’t the type of information that was exposed—PII, PHI, intellectual property and trade secrets. It’s that these organizations didn’t manage risk effectively, from their definitions of risk management to communication gaps between IT and executive management and the board. (The further they are from the point of the breach, the less they understand the breach and its impact.)
Spend now or later
Inside ‘Jobs’
Insider threats can take advantage of high trust levels to hatch elaborate schemes. A group of employees working for a large U.S. technology company decided to use their employer’s technology assets for personal gain. They had access to desktop and laptop computers that were coming off lease, being sold or otherwise recycled. These units were stockpiled in unused offices, unsecured rooms and even in hallways.
The employees signed into the data center using these machines and built their own data management network, underneath the raised floor of the corporate data center. They started “competing” for external business with their employer. This crime went undetected for about a year.
It was eventually detected, but not because of all the technology company’s monitoring hardware and software. A security guard outside of the data center figured it out. The guard noticed that these workers consistently checked into the data center when everyone else was logging out—at the end of the day and on weekends. He became suspicious.
It’s worth noting that many employees who get caught committing fraud against the company are not criminally or even civilly prosecuted. Prosecutions result in a public record—and negative publicity. Which brings up the issue of background investigations: Many people who engage in illegal actions get terminated and soon apply for other jobs in the industry. Meaningful background investigations are woefully absent, and $49 background checks are often inadequate.
There’s a reason that a top secret security clearance can take two years to complete. In 2012, according to The Washington Post, about 500,000 private contractors had federal clearance for “handling top-secret materials” at some level.
Many companies would rather spend on recovery and remediation than on prevention through risk management and optimization of SLAs. (That may not be what statistics indicate, but that’s what we see.) For one thing, after a breach, budget immediately materializes. The message from executive management is usually this: “Fix this and then do what you need to do to keep this from happening again.” Sometimes, the company embraces a more strategic risk management solution in the aftermath of a breach. Other times, though, the focus is very tactical and concentrated on IT security fixes in the absence of a real risk management approach.
Regardless of whether the breach originated at a third party or at the principal company, a key determinant in the post-breach report is who’s in charge of the breach investigation. When executive management, especially the general counsel and the board are involved, there’s a greater likelihood that a more effective risk management program will result. But not always: by the time many companies finish paying the bills associated with a breach, they’re sometimes seeking fiscal restraint and recovering from the financial cost of the breach. This often leads to, “Let’s try and do the rest of this mitigation in-house.” That’s usually a mistake, depending on individual breach circumstances, and the cooperativeness of any third-party vendor involved.
Enterprise Towers of Babel
As much as anything, managing risk is about effective communication.
Take the CISO who happens to ride in an elevator with a member of the board of directors: “We’ve got a BYOD issue that led to a BAA infosec incident.”
Board member thinks “Why can’t this elevator move faster?”
Speak the language of business and risk. This sounds simplistic, but what if the CISO said:
“One of our outside service provider’s employees had some of our client data on an iPad that was stolen, and now it looks like we’re going to have to report this event to regulators in 40 countries. I hate to think what the impact of this is going to be.”
Board member: “Tell me more about this.”
Think about the relationship of security to the management of risk. Risk is a potential condition of concern to many people in the organization. Many executives that will be responsive to the language of risk are not responsive to the language of technology and information security. Chief executives, chief risk officers (which are often chief financial officers), internal legal counsel, internal auditors, privacy officers and compliance officers have an interest in managing risk and are usually responsive. Also, employees with a vested interest in the company’s reputation, including sales and marketing, are often responsive. Conveying the risk message appropriately, though, is necessary to get anyone’s attention.
Speaking technology and security will secure the job. Speaking risk will secure budget and your future.
About the author:
MacDonnell Ulsch is the CEO and chief analyst at ZeroPoint Risk Research LLC, in Boston, Mass., and advises commercial and government clients. He is the author of THREAT! Managing Risk in a Hostile World. The working title of his upcoming book is CYBER SABRES: Defending the Future Against Enemies Near and Far.
Send comments on this column to [email protected].