
peshkov - stock.adobe.com
3 leading multifactor authentication tool providers
Compare top MFA providers Cisco, Okta and Ping Identity. Learn product features and pricing tiers, and get advice on selecting a product for your organization's security needs.
One of the leading and most effective security measures today is multifactor authentication. This foundational identity security technology is essential to verifying users and protecting logins.
Finding the MFA tool that best suits your company's needs can be overwhelming. Various vendors sell MFA products, each offering multiple options and services.
Here, learn about three top MFA providers: Cisco, Okta and Ping Identity. Also, get advice on how to choose the best MFA tool for your organization.
What is MFA and why is it important?
MFA is a security technology that requires users to input two or more methods of verifying their identity before they can access an account or network.
MFA involves the following factors:
- Knowledge factor. This is something the user knows -- for example, a password, passphrase or PIN.
- Possession factor. This is something the user has -- for example, a security token.
- Inherence factor. This is something the user is -- for example, biometrics, such as fingerprints or facial scans.
Requiring multiple authentication measures provides a layered defense that makes it difficult for malicious actors to compromise users' accounts. If an attacker knows a user's password, for example, they must still bypass another factor -- or more -- to breach the account.
3 leading MFA providers to consider
Following is information on MFA tools from Cisco, Okta and Ping Identity, including their features, tiers and pricing.
Cisco
Cisco offers several products in the identity, authentication and authorization space, including Cisco Identity Services Engine (ISE), a network access control platform, and Cisco Duo, an identity and access management software that includes an MFA component. The two products are sold separately and integrate for added security.
Duo comes in four editions:
- Free provides basic MFA capabilities but no other features. It is available to groups of 10 users or fewer.
- Essentials, at $3 per user per month, supports phishing-resistant MFA, single sign-on (SSO) and passwordless authentication. These features make this edition safer and more convenient for users.
- Advantage costs $6 per user per month. It includes Essentials capabilities, as well as identity security posture management (ISPM), identity threat detection and response, and risk-based authentication (RBA). Also known as step-up authentication, RBA enables Duo to change forms of authentication it accepts based on its risk analysis of the current situation and the company's security policies. Users who attempt to access highly sensitive resources, for example, might be required to provide additional or stronger authentication factors.
- Premier costs $9 per user per month. It includes Advantage features, plus zero-trust access and VPN-less remote access.
Okta
Okta offers two identity management applications with MFA components: Okta Platform and Auth0 Platform.
Okta Platform supports an array of identity-related services. Its adaptive MFA component supports RBA by relying on MFA that considers a variety of attributes, such as the user's device, geographic location and behavior. Okta Platform and its adaptive MFA feature also support SSO.
Okta Platform integrates with Okta FastPass, zero-trust software that features phishing-resistant authentication, RBA and passwordless authentication.
Auth0 Platform is specifically tailored for customer authentication on apps and websites. Like Okta Platform, the software supports MFA, passwordless authentication, SSO and, if needed, RBA for customers.
Okta Platform comes in four editions:
- Starter is $6 per user per month for SSO and MFA.
- Essentials, at $17 per user per month, includes Starter features, plus adaptive MFA, lifecycle management, access governance and privileged access management.
- Professional includes Essentials offerings, plus device access, identity threat protection with Okta AI, ISPM and sandboxing capabilities. Contact Okta for Professional pricing.
- Enterprise offers Professional features, as well as API access management, access gateways and machine-to-machine tokens. Contact Okta for Enterprise pricing.
Auth0 offers B2B and B2C editions, available at monthly or yearly billing. Visit Auth0 for B2B pricing. B2C is available in four tiers:
- Free for up to 25,000 monthly active users, includes passwordless with text, email, passkeys and one-time passwords (OTPs).
- Essentials, starting at $35 per month for up to 500 monthly active users, includes MFA with Duo or OTPs, role-based access control and passwordless authentication.
- Professional, starting at $240 per month for up to 1,000 monthly active users, includes Essentials features, plus MFA with phone, email, WebAuthn and the Auth0 Guardian app.
- Enterprise includes custom user and SSO tiers and enterprise support. Contact Auth0 for pricing.
Ping Identity
Ping Identity offers several MFA products, including PingOne MFA and PingID. Both can be used as part of the vendor's Ping Identity Platform.
PingOne for Workforce, which integrates with Microsoft environments, offers two editions:
- Essential, at $3 per user per month, offers SSO, MFA and directory for SaaS apps.
- Plus, at $6 per user per month, offers Essential features, plus adaptive MFA and passwordless authentication.
PingOne for Customers enables organizations to authenticate customers accessing their apps and websites. It also supports passwordless authentication, RBA and other validation methods. It has two editions:
- Essential, starting at $35,000 annually, offers SSO and user management.
- Plus, starting at $50,000 annually, offers Essential features, as well as adaptive MFA, embedded MFA in mobile apps and API access management.
PingID helps organizations authenticate their employees, contractors, partners and other third parties. It can be used standalone or as part of Ping Identity Platform and other Ping products. PingID features include MFA, passwordless authentication, SSO and RBA. It also supports MFA for devices that are temporarily offline. Contact Ping Identity for PingID pricing.
How to choose the best MFA tool for your organization
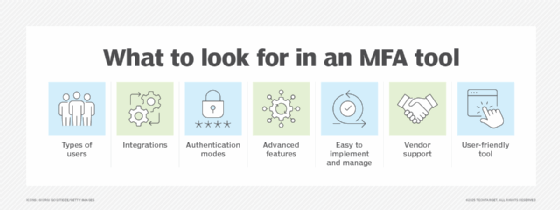
Every organization has a unique set of authentication requirements and preferences. To that end, no best MFA tool exists. Organizations considering MFA tools should ask the following questions:
- Who will be authenticated through this tool -- customers, employees or both? Any others? First, identify the legal, regulatory and contractual requirements that apply to those users. Second, determine the organizational resources they access once authenticated.
- How many existing identity, authentication and authorization technologies must integrate with the MFA tool? It's important to test any integrations in advance so any issues can be identified and resolved before acquiring MFA software.
- What authentication factors and methods do the MFA tools need to support? Examine existing biometrics, hardware tokens, cryptographic keys and other elements. Consider not only those factors and methods supported today, but those that will be rolled out as authentication technologies progress.
- How secure is the MFA tool and its associated technologies? MFA is an obvious target for attackers. Ensure the MFA vendor selected actively maintains its software and its product was built under secure software development practices.
- How well supported is the MFA tool? Consider not just the vendor's technical support offerings, but its documentation, forums and other resources designed to provide advice and user assistance.
- How user-friendly is the tool? Users often view MFA as time-consuming and cumbersome. Be sure the vendor offers clear, easy-to-use MFA methods that meet various users' needs.
Editor's note: The author conducted market research to find MFA tools that are in widespread use, still actively developed and have received many recent positive reviews on reputable review sites.
Karen Scarfone is principal consultant at Scarfone Cybersecurity in Clifton, Va. She provides cybersecurity publication consulting to organizations and was formerly a senior computer scientist for NIST.







