The components and objectives of privacy engineering
Privacy engineering helps organizations balance business and privacy needs, while mitigating the impact of data breaches. Learn about its components and objectives.
Data privacy is one of the greatest challenges facing enterprises today. Growing public concern, strict compliance regulations and increased cyber threats are making the integration of privacy into organizations' processes and practices a high priority.
To properly implement privacy, two concepts are emerging: privacy by design and privacy engineering.
"Privacy by design translates privacy requirements into an implementation plan," said William Stallings, author of Information Privacy Engineering and Privacy by Design: Understanding Privacy Threats, Technology, and Regulations Based on Standards and Best Practices. "Privacy engineering is the actual implementation, operation and maintenance."
In the past, privacy often wasn't considered until right before deployment, if at all. Today, privacy must be integrated into the entire development and deployment process. But how?
In this excerpt from Chapter 2 of Information Privacy Engineering and Privacy by Design, learn how to get started with privacy engineering, and discover how security risk assessments and risk management contribute to privacy engineering activities. Download a PDF of Chapter 2 to read more on privacy by design, privacy and security, privacy versus utility and usable privacy.
 Click here to learn more about
Click here to learn more about
Information Privacy
Engineering and Privacy
by Design by William Stallings.
2.3 Privacy Engineering
Privacy engineering encompasses the implementation, deployment, and ongoing operation and management of privacy features and controls in systems. Privacy engineering involves both technical capabilities and management processes. The primary goals of privacy engineering are to:
- Incorporate functionally and management practices to satisfy privacy requirements
- Prevent compromise of PII
- Mitigate the impact of breach of personal data
Although Figure 2.1 shows privacy engineering as being distinct from, and following on, PbD, the term privacy engineering is often used to encompass privacy-related activities throughout the system development life cycle. An example of this is shown in Figure 2.3, adapted from NISTIR 8062.
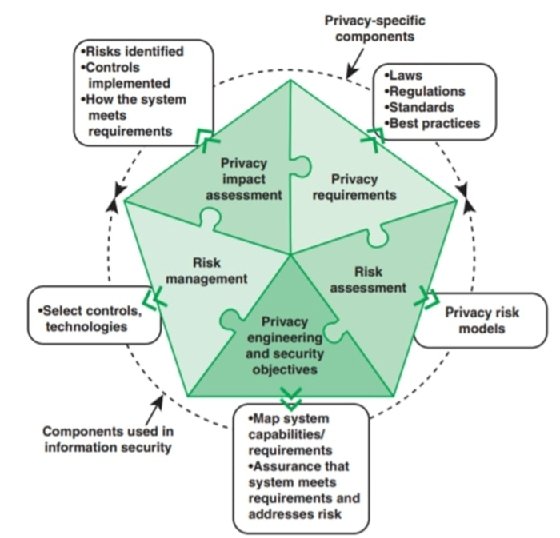
As illustrated in Figure 2.3, the NIST document lists five components of privacy engineering -- two that are specific to the privacy engineering process and three that are components typically used in information security management. The components are:
- Security risk assessment: A security risk is an expectation of loss expressed as the probability that a particular threat will exploit a particular vulnerability with a particular harmful result. Security risk assessment is a process that systematically (a) identifies valuable system resources and threats to those resources, (b) quantifies loss exposures (i.e. loss potential) based on estimated frequencies and costs of occurrence. Thus, risk assessment follows two parallel paths. First, for each threat to a resource, the value of the resource is assessed and the potential impact, or cost, if the threat to that resource becomes a successful threat action. Second, based on the strength of a threat, the probability of the threat becoming an actual threat action. Finally, the potential impact of the threat and the likelihood of its success are factors in determining the risk.
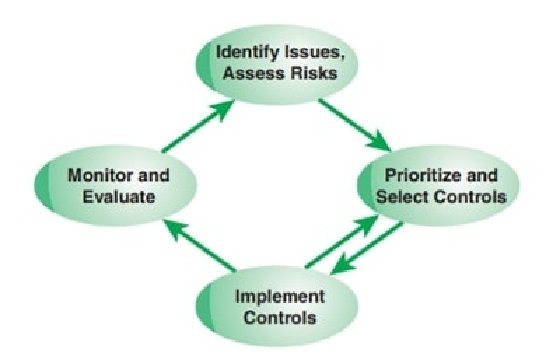
- Risk management: NIST SP 800-37 (Risk Management Framework for Information Systems and Organizations) states that risk management includes a disciplined, structured, and flexible process for organizational asset valuation; security and privacy control selection, implementation, and assessment; system and control authorizations; and continues monitoring. It also includes enterprise-level activities to help better prepare organizations to execute the RMF at the system level. Risk management is an interactive process, as illustrated in Figure 2.4, based on one in ITU-T X.1055 (Risk management and risk profile guidelines for telecommunication organizations), consisting of four steps:
- Assess risk based on assets, threats, vulnerabilities, and existing controls. From these inputs determine impact and likelihood and then the level of risk. This is the risk assessment component described in the preceding bullet.
- Identify potential security controls to reduce risk, prioritize their use, and select controls for implementation.
- Allocate resources, roles, and responsibilities and implement controls.
- Monitor and evaluate risk treatment effectiveness.
Check out a Q&A with author William Stallings to learn how privacy engineering and privacy by design operate together to balance privacy with utility and usability.
In the context of privacy engineering, the emphasis is on privacy risk and the implementation of privacy controls. Chapter 11 discusses risk management.
- Privacy requirements: There are system requirements that have privacy relevance. System privacy requirements define the protection capabilities provided by the system, the performance and behavioral characteristics exhibited by the system, and the evidence used to determine that the system privacy requirements have been satisfied. Privacy requirements are derived from a variety of sources including laws, regulations, standards, and stakeholder expectations. Chapter 3 examines privacy requirements.
- Privacy impact assessment: The NIST Computer Security Glossary (https://csrc.nist.gov/ glossary) defines a PIA as an analysis of how information is handled: (i) to ensure handling conforms to applicable legal, regulatory, and policy requirements regarding privacy; (ii) to determine the risks and effects of collecting, maintaining, and disseminating information in identifiable form in an electronic information system; and (iii) to examine and evaluate protections and alternative processes for handling information to mitigate potential privacy risks. In essence, PIA consists of privacy risk assessment followed by a selection of privacy and security controls to reduce the risk. Chapter 11 examines the PIA.
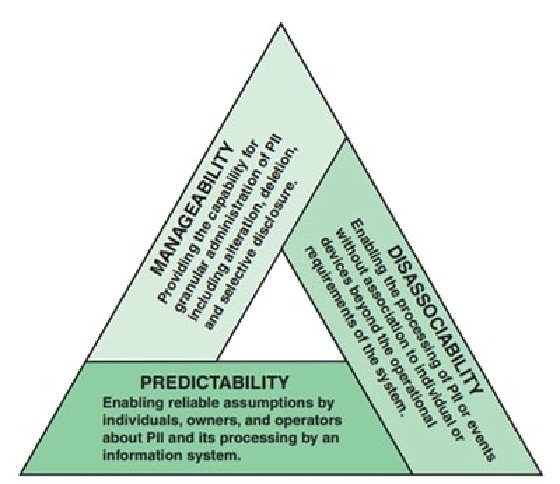
- Privacy engineering and security objectives: Information security risk assessment focuses on meeting the common security objectives, including confidentiality, integrity, and availability (Figure 1.1). Similarly, privacy engineering objectives focus on the types of capabilities the system needs in order to demonstrate implementation of an organization's privacy policies and system privacy requirements. NISTIR 8062 proposes three privacy objectives, illustrated in Figure 2.5. Chapter 3 expands on this topic.
 William Stallings
William Stallings
About the author
William Stallings has made a unique contribution to understanding the broad sweep of technical developments in computer security, computer networking and computer architecture. With more than 30 years of experience, he has been a technical contributor, technical manager and executive with several high-technology firms. Stallings has authored 18 textbooks and, counting revised editions, a total of 70 books on various aspects of these subjects. He holds a Ph.D. from MIT in computer science and a Bachelor of Science in electrical engineering from Notre Dame.






