Secure service edge strengths drive SASE deployments
Enterprise Strategy Group's John Grady discusses the latest findings in his newly released report and why businesses won’t start a SASE initiative without first implementing SSE.
Network and security convergence has come under closer scrutiny since the sudden COVID-19-induced migration of office workers to remote locations. To accommodate today's new reality of hybrid workforces and the shifting of network controls to the cloud, IT security professionals are implementing a network architecture known as secure access service edge (SASE). It combines VPN and SD-WAN capabilities with cloud-native security functions such as secure web gateways, cloud access security brokers, firewalls and zero-trust network access.
As a result, greater emphasis has been placed almost squarely on the shoulders of network security in the form of security service edge (SSE), which converges network security services delivered from a purpose-built cloud platform. Although considered a subset of the SASE framework, SSE is more the primary enabler of SASE. Most enterprises won't implement an SASE framework without first implementing SSE to converge secure access to public and private applications as well as the broader internet.
This and other key findings are revealed in a report by John Grady, principal analyst at TechTarget's Enterprise Strategy Group (ESG). To gauge the growing importance of SSE in network security, ESG conducted an in-depth survey of 390 IT and security professionals at midmarket and enterprise organizations in the U.S. and Canada. The ESG report, "2023 SASE Series: SSE Leads the Way Toward SASE," asked survey respondents to identify the top drivers of SASE and SSE initiatives, the primary SSE tools and capabilities they're seeking and their progress in support of network and security convergence.
In this interview, Grady discusses the report's key findings, unexpected surprises, SSE's role in aiding and abetting an SASE framework and advice for businesses considering and deploying SSE tools as part of their network and security convergence initiatives.
What does the survey tell us about the importance of SASE and SSE in business?
John Grady: SASE was introduced just before the COVID-19 pandemic. Then suddenly, everyone's working remotely. Most organizations realized they didn't have the security infrastructure to support remote workforces, so that's when SASE really took off and has become more of a critical need over the last 24 months.
Flash forward to where we are now with hybrid use cases. Users and resources are scattered all over the world. The goal of SASE and SSE is to optimize the connectivity and security of all those different entities, enabling consistent protection, centralized management and uniformly distributed enforcement that's closer to the users and entities.
And there's still a big need just to modernize a lot of the security infrastructure. Among those that we surveyed, 68% reported three or more benefits from SASE, and 64% reported reduced costs of some kind -- reduced security solution costs, reduced security operational costs, reduced network solution costs or reduced network operational costs. So, faster problem resolution, ease of management, faster onboarding, reduction in complexity and one other point because it's relevant: 80% of those who have implemented or begun to implement SSE say cybersecurity is easier than it was two years ago, which is a good kind of proof point.
So, is SSE essentially greasing the skids for companies implementing a SASE program?
Grady: Converging networks and security is a big project. There are still a lot of companies that have on-premises secure web gateways with VPN concentrators and network firewalls. When you think about it, it's a lot of tools, and a lot of those capabilities are still on premises. Transitioning those controls to the cloud is a big project, so a lot of organizations are going to pick a lane.
Our research found that 72% of respondents said their organization was going to start with the security or SSE side of SASE first, with 25% focused on the SD-WAN side, and only 4% were going to take a fully converged SASE approach. SSE just simplifies that conversation.
I think most organizations are going to view SSE as a steppingstone toward SASE, although the timeline may vary -- keeping a longer-term converged network and security architecture in mind, while accomplishing shorter-term goals with SSE. But SSE is still a pretty big undertaking to say nothing of the broader SASE initiative when you bring networking into the fold as well. Overall, 57% of respondents believe it will take at least two years to fully adopt SASE, up from 34% in 2021.
Most businesses in the throes of converging networks and security said they're currently working with one or two vendors. Why did they say they'll need to add more vendors after they complete the project?
There's this prevailing belief that working with multiple vendors is going to lead to better security efficacy. Almost half of the respondents felt that way. And there's the reality that managing the tech stack and dealing with already deployed and legacy tools requires relationships with multiple vendors. Maybe you just made some recent purchases and you're locked in for a certain amount of time. Also, it's expensive if you're changing vendors and trying to standardize on one. And they believe you can't get the functionality you need from a single vendor.
But when you look at what's driving interest in SSE, and I think a lot of that holds for SASE as well, those expected benefits in a lot of cases would be better served by reducing the number of vendors you work with. I just think as they start to look longer term and wrap their head around the idea that it's possible to get everything they need from one or two vendors, we'll start to see a shift, and vendor consolidation over time will become an important driver to implement SASE and SSE. In and of itself, vendor consolidation isn't a core driver, but the drivers that organizations are pointing to are in some way served by vendor consolidation.

But if businesses eventually depend on one or two vendors long-term, does that dependency create inherent problems?
It can. But I think it's becoming untenable to have so many vendors. We've done research showing that the vendors and the products they supply to enterprise IT can number in the dozens. There's a point of diminishing returns, but I do want to stress it doesn't have to be just one vendor.
SASE and SSE are about integration, ease of management, ease of deployment, streamlined operations and streamlined vendor management. The idea of SASE and SSE is certainly to start to consolidate where you can. I think that there's still some education that needs to take place and just some time that needs to go by on the user side to be confident that a one- or two-vendor SASE approach will work for them.
Did you come away with any surprises from the report?
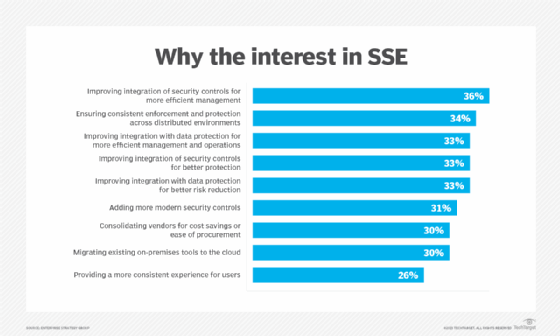
You hope there's some cost savings involved with implementing SSE, but that's further down the list of reasons security professionals are interested in it. We thought maybe that would rank a lot higher because of the macro environment, but I think it's good. I think folks are looking at SSE for the right reasons, which is improving their security, improving user protection, modernizing their security stack -- things like that, as opposed to it's going to save me money.
 John Grady
John Grady
Also, there's this newer area called SaaS security posture management, or SPM, which is basically identifying misconfigurations in SaaS applications. And in SaaS applications, some of the SASE vendors have started to provide functionality in that area. But it's still pretty early. When we asked what capabilities are most important in CASB [cloud access security broker] as part of an SSE architecture, the top response was identifying and remediating misconfigurations. That finding shows how important this functionality is because everything else on this list is what SASE's been doing for years: protecting data, managing control, threat protection and visibility into unsanctioned SaaS app usage. It's just interesting how much the functionality issue resonated.
There was one other interesting piece concerning network and security convergence from an organizational perspective in terms of the data. We asked what actions your organization is going to take or plans to take to improve collaboration across the different groups responsible for network and security. Creating a center of excellence (CoE) that's focused on network and security convergence topped the list at 44%, but it's still very early. Only 9% say they've already done that, 17% say they're actively implementing a CoE program and the rest are kind of interested or planning to do so. For perspective, we have cloud centers of excellence, we've seen it with zero trust, and now it seems we're moving into network and security centers of excellence to support SASE.

How would you advise organizations planning or implementing SSE initiatives?
Grady: For most organizations, it's worthwhile to define your initial path, because it's going to be a lot. Take inventory across your networking security, what you have in place, what you're using now, where the greatest pain points are, what you're looking to get out of it, and determine your starting point.
Then you're looking at vendors. You're obviously going to consider who you're already working with. But use it as an opportunity to consider other vendors as well. Hopefully you're looking for a long-term partner as you're rolling out SSE, so don't limit yourself to those you're already working with. One of the considerations is who can support you in both the short term and the long term.
You may be starting with a specific part of SSE. Maybe it's tools providers for ZTNA [zero trust network access] and SWG [security web gateway]. Do they have the capabilities or roadmap to get to maybe digital experience management or remote browser isolation, and do you see yourself potentially using those tools in the future?
But at the same time, don't get analysis paralysis. If you haven't started, start your planning and get going as soon as you can.
Vendors will need to shepherd users toward the idea of vendor consolidation. The reasons businesses are looking toward SASE all point to a single- or two-vendor approach. So, vendors should focus on the benefits of that consolidation and how it can help businesses achieve their goals rather than just the consolidation itself and the fact that an analyst says SASE is ideally delivered from one vendor.
Vendors also need to show technology partnerships and how they can provide flexibility. Everyone's not going to move everything to the cloud all at once, so vendors need to provide hybrid options. When considering SSE initiatives, IT professionals surveyed said the most important attribute was hybrid options to connect on-premises and cloud solutions to help transition to fully cloud-delivered over time.
Read the full survey results
Enterprise Strategy Group subscribers can click here for a report on the survey covered in this Q&A.
Editor's note: This interview has been edited for clarity and length.






