SD-WAN deployments feed SASE network and security convergence
Enterprise Strategy Group's Bob Laliberte discusses the latest findings in his newly released report and why SD-WAN's direct cloud connectivity feeds SASE business initiatives.
Businesses are implementing a network architecture known as secure access service edge (SASE) to provide the network and security convergence necessary to accommodate today’s hybrid and remote workforces and the accelerated shift of network controls to the cloud. SASE (secure access service edge) is network architecture that combines VPN and SD-WAN capabilities with cloud-native security functions such as secure web gateways, cloud access security brokers, firewalls and zero-trust network access (ZTNA).
SD-WAN is no stranger to organizations that have been using the networking technology in one form or another for remote and branch locations during the past several years, especially since the COVID-19 pandemic when companies expanded their digital transformation and cloud migration efforts. Most enterprises planning or in the process of implementing a SASE framework are somewhat divided between first going with SD-WAN for direct access to cloud-based applications or SSE (security service edge) for secure access to public and private applications as well as the internet.
This and other key findings are revealed in a report by Bob Laliberte, principal analyst at TechTarget’s Enterprise Strategy Group (ESG). To gauge the growing importance of SASE, SD-WAN and SSE in network and security convergence, ESG conducted an in-depth survey of 374 networking professionals at organizations in the U.S. and Canada involved with networking technology and processes and familiar with SD-WAN and SASE technologies. The ESG report, "A Network Perspective on SASE and SD-WAN," asked survey respondents to identify the major issues confronting network professionals.
In this interview, Laliberte discusses the report's key findings, what's driving SD-WAN adoption, SD-WAN’s role in aiding and abetting SASE strategies, and advice for businesses considering and deploying SASE as part of their initiatives to converge network optimization and security controls.
How has SD-WAN changed the way data centers operate and businesses communicate?
 Bob Laliberte
Bob Laliberte
Bob Laliberte: There's a lot of organizations that have had SD-WAN for a number of years now. And by that, I mean five to six years easily. Prior to a lot of cloud adoption, all applications were housed in a data center. All the connections to those applications from outside were directed at the data center.
So, you created a hub-and-spoke network connected to what would typically be castle and moat security. All your applications were in the castle. You built a big perimeter of security around it as organizations started to digitally transform and take advantage of public clouds and deploying applications there.
What they found is with all their workers and the remote and branch offices, they're still connecting to those clouds by going into the data center up to the cloud, back to the data center, back to the remote -- what they refer to as hair-pinning. Obviously, that's not great, especially if you have long distances between your data center and remote employees. It leads to a lot of poor experiences, complaints, tickets, lost productivity. SD-WAN enabled organizations to have direct internet access from those remote branches.
What does the survey tell us about SD-WAN's value to organizations?
Laliberte: The biggest benefit of SD-WAN is it enables organizations to directly access their cloud-based applications from any location and provide perspective on that. The other thing it did -- and this was really highlighted at the early stages of SD-WAN -- it was all about reducing the cost of network connectivity and providing additional bandwidth.
In the old days, with the hub and spoke, there were typically two MPLS (multiprotocol label switching) links -- one was primary, one was a secondary back up. Everything ran over that primary, and if there was a problem, then it would all fail over to that secondary link. You were paying a lot of money for that secondary link, but you weren't using it. SD-WAN brought in a lot of dynamic control to allow organizations to take full advantage of both pipes and then prioritize which applications they want to be able to ensure had good performance -- even if one of those links failed and everything had collapsed.
People felt more confident with using broadband connections. I have talked to end users who have said, "Yep, it was great. The other day I lost both my primary links. They failed over to 4G and I didn't get one ticket. I didn't get one complaint. Nobody knew the difference. The critical apps continued to run until they were able to restore those primary links."
So, SD-WAN has come a long way in modernizing the network connections. Not only to the data center, to the public clouds, but to other locations as well, and to do so securely. Being able to segment the traffic and prioritize it also provided some security because now if something got into the network, it would be able to see what else is traversing it.
With SD-WAN, you also saw the early foundations of SASE where all the SD-WAN vendors were partnering with the firewall and ZTNA organizations to do single click for those right to provision security applications on the premises before the cloud became all the rage.
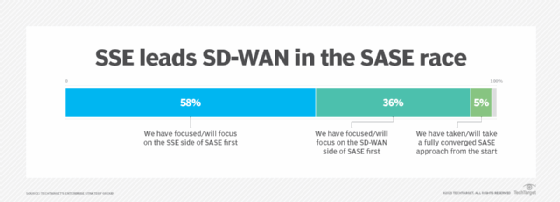
Among the key findings in the report, what were the most significant?
Laliberte: The interesting takeaway is that most SASE deployments continue to be led by SSE. The security side tends to be the leader. Even when we asked the networking team and even when organizations said they already had more SD-WAN deployed than they do SSE, they're still saying their security is obviously an incredibly important initiative in improving cybersecurity. Every year we do a technology spending intention survey and ask what are the most important initiatives. The last several years, it's always been improving cybersecurity. And that's especially true when you think about what's happened with hybrid workforces. It becomes even more imperative.
Back in the old days, you had the castle and moat, and you did the perimeter. But now those applications are distributed to clouds, they're distributed to edge locations. Your employees are distributed all over the place, so that security aspect has just ratcheted up a whole other level. Almost three-fourths of organizations said they consider home employees and their homes as corporate endpoints that need to be protected and monitored. It's not just about connecting remote employees. The key is secure connectivity.
One of the other takeaways from the report was that 73% of organizations find network complexity is definitely increasing. As things get more distributed, the network becomes more critical to the environment because everything's got to be connected. In the network environment, there's a lot more complexity because now you've got to connect up to all the cloud locations.
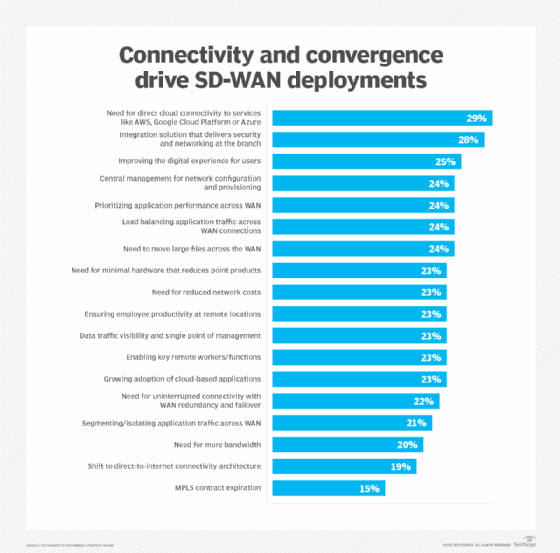
Given the increase in network complexity, what's driving users to choose SD-WAN when starting a SASE program?
Laliberte: Direct cloud connectivity is absolutely the top driver and that coincides with the research that we've done as well. So being able to deliver not just the networking component but the security, whether that's through segmentation, whether that's through integration with the firewall or ZTNA.
I think organizations on the networking side are also very focused on user experiences. And so that's typically related to performance. It's not about quality of service anymore, it's about quality of excellence. It's about what experience the end user had.
Another driver for SD-WAN is cloud-based centralized management because you've got such a distributed environment. You don't want to have to roll trucks and people to provision. It was one of those operational efficiency things of how to effectively manage a distributed environment at scale with fewer resources.
Another important driver is the vast majority of organizations want to consume SD-WAN as a managed service. They're used to consuming their networking as a service, the MPLS links, everything else. The other component to that is they don't want to deal with each of the bandwidth providers, especially if they've got a highly distributed environment that's global, if they can outsource that to either a telco or an MSP. I would brand them more co-managed. They want to be able to set the policies around which applications get prioritization.
You're controlling the policies that are implemented, but you're letting the managed service provider deal with all the upgrades, patches, dealing with the internet service providers, so when there's an issue, you don't have to be the one figuring out who's the provider in that country. It's really removing that headache of management and enabling them to focus on making sure the experience and the applications are delivering good performance.
While SASE is all about network and security convergence, is there a rivalry between networking professionals who favor SD-WAN connectivity and security teams who see SSE as the prime mover in adopting SASE, and do both factions need to get on the same page?
Laliberte: I think they certainly need to. Networking and security go together. This is the peanut butter and chocolate story coming together. You have to have the connectivity and that's why you need the security. But if there's no network connecting anything, then you probably don't need SSE. I'm not saying networks are more important than security. But for all this to work, everything needs to be connected.
How long it takes to get there could be a while because you've got these ingrained silos and rivalries for the budget. Who's getting assigned the money. And that's where sometimes these cloud centers of excellence play an interesting role because the funds get diverted to that group and they decide as a team how the monies get carved up.
When we asked networking professionals if they already had SD-WAN, 55% said they had implemented or begun to implement it and 33% said they were actively planning and would be doing that. Yet even those respondents who said that they had implemented SD-WAN came back and said, "We're going to start with SSE." It's just an understanding that they've got the connections, the SD-WAN's deployed, and so the emphasis needs to be on securing the connections.
Every year, the cyber threat grows worse. And that's bad enough. Now you've got generative AI. Here's a botnet. Give me 30 versions of it. So, the real threat is the security SSE side and why organizations have to focus so much time and energy on it.
I don't think anyone on the network side is upset that people are saying we're going to start our SASE program with SSE and not SD-WAN. The funny part is when the security teams have issues, most of the time they're coming to the network team to see what's happening in the network traffic?
Given the impacts of COVID-19, remote and hybrid workforces, increasingly distributed environments, and inflation, how far along are companies in their pursuit of universal and seamless network connectivity?
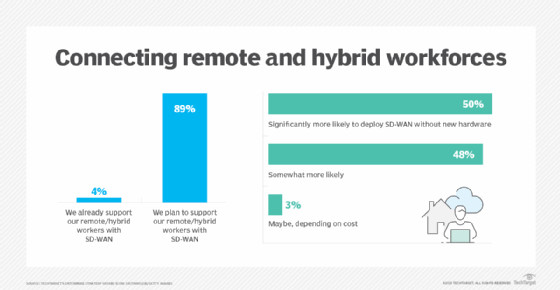
Laliberte: I think they're in fairly good shape. I think SD-WAN has a much better shot of becoming ubiquitous because everyone's going to connect the cloud apps. Everyone wants to take advantage of more cost-effective network connections, but also have that high level of availability. That's only improved with 5G coming out because now 5G could be used for two things. One is a primary connection to a corporate location, but also whether SD-WAN would be deployed to home users. During the pandemic, certain groups of home users got it -- call center employees, executives and healthcare --because they were doing so much remote and they wanted to have the performance and quality.
The dilemma is that you're deploying AI technology to take advantage of multiple connections, but most people only had a single broadband connection coming into their house. So 5G now provides an interesting dual path for SD-WAN for home use. I'll be watching to see over time whether SD-WAN to the home user now becomes much more of a reality with multiple connection points that companies can leverage to do that.
So, does this mean network infrastructure and connectivity will be dominated by 5G broadband technology in the not-too-distant future with perhaps some casualties among the many technologies currently used to connect distributed environments?
Laliberte: SD-WAN will be around for a while. I don't see anything replacing it. For the last two years I've been throwing 5G responses into my questions. And as is typical with new technology like this, there's a little bit of a halo effect and an aspirational response: "I don't know what it is, but I'm going to use that." While 5G does provide benefits for the consumer, most believe it can be monetized for the enterprise, meaning that the enterprise could see valuable advantages of going to 5G.
The big part about 5G is that it doesn't just have to be a backup. It can actually be a primary link where you've got that connectivity. Obviously, 5G is going to depend on what spectrum the providers are using in that area. It will determine what level of capacity the links are capable of holding, but certainly for home use, 5G makes a ton of sense for businesses.
Internet broadband has much higher bandwidth, but when working from home with internet broadband, sometimes it's there, sometimes it's not. I have actually seen over the last couple years organizations saying, "I know I had dual broadband, but I think I'm going to put an MPLS link in there and make sure all my steady state traffic stuff I need is going over that." There's been a flight back to quality and performance over cost. So, I think you're going to see a continued mix of networking technologies.
How would you advise users who are planning or implementing a SASE program?
Laliberte: If organizations are in the process of implementing SASE, it all depends on whether they've got it deployed or they're going to be deploying -- two big differences. If they've already got it, they've made their bet. Then it's a question of what level of integration, what partnerships does that company have?
There are single SASE vendors that would probably merit consideration by organizations. But that doesn't mean a wholesale swap out. It usually means "I'll take this chapter and that chapter today, and maybe down the road when that depreciates, I'll add a lot of this, predicated on the fact that it's going to be able to deliver the same level of security efficacy as I had before."
The one thing that we've always said to vendors who are playing in this space is that you've got to be flexible. You're trying to go in and you're selling the book, but you're delivering one chapter at a time because there may be a lot of components to SASE networking. When I think about the SD-WAN space, it's really about that operational efficiency, it's about security and it's about delivering the best experiences they can to their end users.
Read the full survey results
Enterprise Strategy Group subscribers can click here for a report on the survey covered in this Q&A.
Editor's note: This interview has been edited for clarity and length.
Ron Karjian is an industry editor and writer at TechTarget covering business analytics, artificial intelligence, data management, security and enterprise applications.







