Risk Management Framework
In this excerpt from chapter 3 of Risk Management Framework, author James Broad discusses the four components of risk management.
The following is an excerpt from the book Risk Management Framework written by James Broad and published by Syngress. This section from chapter 3 provides an overview of risk management and its four components.
 RISK MANAGEMENT
RISK MANAGEMENT
To fully understand and successfully implement the risk management framework, one must have a complete understanding of how the organizational multi-tiered risk management process is structured and used. This chapter discusses these concepts and how the RMF and organizational risk management techniques are interrelated. The chapter covers the three tiers of a typical multi-tiered organizational risk management process and describes the components of organizational risk management. It also introduces the risk executive (function) and explains this component's relationship to the RMF and risk management. Risk management is an extensive topic; this chapter only touches on the high points of the process. Several universities offer undergraduate degrees, postgraduate certificates, master's degrees, and even doctoral degrees in risk management. For-profit, non-profit, and not-for-profit organizations also have large investments of time, money, people and other resources in risk management that delve deeply into the theory and processes that encompass complete risk management. The intention of this chapter is not to make the reader an expert in risk management, but rather to introduce the basic components of risk management as defined by NIST and associate these with the RMF.
RISK MANAGEMENT AND THE RMF
Risk management and the risk management framework seem to be the same thing, but it is important to understand the distinction between the two. The risk management process is specifically detailed by NIST in three different volumes. NIST SP 800-30, Guide for Conducting Risk Assessments, provides an overview of how risk management fits into the system development life cycle (SDLC) and describes how to conduct risk assessments and how to mitigate risks. NIST SP 800-37 discusses the risk management framework that is the subject of this book; the guide is discussed in great detail in coming chapters. Finally, NIST SP 800-39, Managing Information Security Risk, defines the multi-tiered, organization-wide approach to risk management that is discussed in this chapter.
Risk Management Framework
Author: James Broad
Learn more about Risk Management Framework from publisher Syngress.
At checkout, use discount code PBTY14 for 25% off
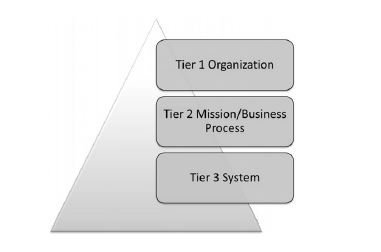
The older certification and accreditation (C&A) process had a number of shortcomings, including looking at risk only from the information systems perspective. This view focused on evaluating risks as they impacted a specific system, in a vacuum and does not address how the systems risks will impact larger business unit or the organization itself. In developing the RMF, members of the Joint Task Force Transformation Initiative, including members from NIST, determined that the best approach to risk management is to view risks at not only the system level, but also at the business unit level and the organizational level. This approach includes determining how the organizational risk picture may be impacted if a specific system is placed into the production environment. This evaluation takes place at three levels: the organizational level, or tier 1; the mission and business process level, or tier 2; and the system level, or tier 3, as illustrated in Figure 3-1. This holistic, multi-tiered, organizational view of risk assists senior leaders in determining how to effectively and efficiently manage risk in the most cost-effective manner across the entire organization.
COMPONENTS OF RISK MANAGEMENT
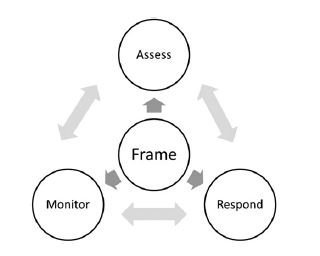
Effective risk management is composed of four basic components: framing the risk, assessing the risk, responding to the risk, and monitoring the risk. Each component is interrelated and lines of communication go between them. The output from one component becomes the input to another component. Risk management is a process that must be ingrained across the entire organization, involving information system owners, developers, engineers, and administrators at the tactical level; mid-level planners and managers at the business unit level; and the organization's most senior leaders, who view risk at the strategic level as it impacts the entire organization. The leaders define the environment in which risk-based decisions are made and set the risk management process on a framework by developing a risk management strategy.
Read the full excerpt
Download the PDF of chapter 3 to learn more!
Framing the Risk
Leaders in the organizational tier establish the risk framework that the organization will use to define risk assumptions, risk constraints, risk tolerances, and risk priorities. Defining risk assumptions includes determining the likelihood that a vulnerability, threat, or occurrence could impact the organization and what the consequences or impact would be if it were to occur. Issues in the enterprise that restrict or slow risk assessments, risk response, or risk monitoring are categorized as risk constraints. Risk tolerances are those possible events or occurrences whose impacts on the organization are acceptable; often these risks are deemed acceptable because of the excessive cost of countering them. Finally, risk priorities are those events that must be protected against and systems that have a reduced risk tolerance. Many organizations prioritize system risk acceptance based on whether or not systems support critical business or mission functions, as these systems have the lowest risk tolerance and highest risk priority.
Figure 3-2 illustrates the interaction that each of the components of the risk management process has with each other. The risk framework helps to inform and drive each component of the risk management process assessment, monitoring, and response. By evaluating sources of threat information, either from open source information or through classified briefings (depending on the organization or environment), the risk management process is framed and acceptable values are developed for risk assumptions, risk constraints, risk tolerances, and risk priorities. The framing process also includes external risk relationships with other organizations that will accept the transfer of risk. For example, insurance carriers and stakeholders may be impacted by the organization's risk management process, as may suppliers, customers, served populations, mission/business partners, and service providers. These stakeholders can be either providers of risk management processes or consumers of the organization's protections from risk. Risk framing results in a critical output for the organization -- the risk management strategy -- which, like the risk assessment, is an input for the risk response component.
Risk Assessment
The risk assessment aims to draw a risk picture for the organization. This includes threats directed at the organization, the internal and external vulnerabilities the organization faces, and the harm that will come to the organization if a threat exploits a given vulnerability. The likelihood of the harm occurring is also evaluated and calculated in the risk assessment.
The organization's leaders determine various components in the risk assessment strategy, including the tools, techniques, and methodologies that will be used to develop the risk assessment; assumptions and constraints to the risk assessment; and the roles and responsibilities for various positions within the risk management process. The leadership also defines assumptions related to the risk picture, how risk and threat information is collected, the frequency of risk assessments at each tier, and how risk assessments are conducted. Risk assessment results can drive changes to other components of the risk management process.
Risk Response
More on risk management from SearchSecurity
Enterprise risk management: Metrics and assessments
Risk assessment vs. risk analysis vs. risk management
risk management: Baseline management and control
The security risk management lifecycle framework
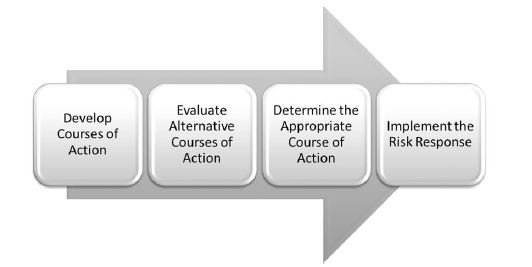
This component determines how the organization responds to a risk once it is identified. This identification normally is an input to the risk response from the risk assessment component in the form of the determination of risk, but can also come from the risk frame in the form of the risk management strategy described earlier. The risk response serves to provide an organization-wide, consistent response that addresses the risk frame. This includes developing courses of action, evaluating alternative courses of action, determining the appropriate course or courses of action, and implementing the risk response based on the selection. These steps are illustrated in Figure 3-3. The selection made has the potential to change the organization's risk procedure and, once made, the other components of the risk management process need to be evaluated for necessary changes.
Monitoring Risk
The final component of risk management determines how the organization monitors risk over time. This component validates that the risk program has implemented the planned risk response and that information security plans are derived from traceable mission/business functions. It also determines the effectiveness of ongoing risk response plans and determines and identifies changes in the environment that will impact the risk profile of the organization. The risk program can be modified as needed to respond to changes identified in the monitoring process. These changes initiate updates to the organization's risk assessment, risk response, and risk frame components.
About the author:
James Broad (CISSP, C|EH, CPTS, Security+, MBA) is the President and owner of Cyber-Recon, LLC, where he and his team of consultants specialize in Information Security, Information Assurance, Certification and Accreditation and offer other security consultancy services to corporate and government clients. As a security professional with over 20 years of real-world IT experience, James is an expert in many areas of IT security, specializing in security engineering, penetration testing, vulnerability analysis and research. He has provided security services in the nation's most critical sectors including defense, law enforcement, intelligence, finance and healthcare.