Grafvision - Fotolia
Readers’ top picks for enterprise firewalls
The companies and key functionality organizations seek out when they upgrade or add firewall technology to their enterprise environments.
With transitions to mobile and cloud underway, many companies continue to focus on building out foundational elements of their information security programs -- 34% of the 4,480 readers surveyed in 2015 indicated plans to invest in firewalls in the next 12 months. About 25% are planning to purchase intrusion detection systems/intrusion prevention systems (IDS/IPS) and 15% are looking at DNS firewalls or DNS security products. Roughly 19% of those surveyed are planning to purchase unified threat management (UTM) systems, which are typically recommended for small to midsize businesses, although the lines between UTM and enterprise firewalls are blurring somewhat.
As companies move from port-based perimeter systems to next-generation firewalls to block and tackle apps and social media content, the requirements for advanced protection in the application-layer, mobile endpoint and cloud are complicating product selection. Which technology providers made the shortlist for enterprise firewalls, according to those surveyed?
On the list
Integration and better performance is the name of the game as firewalls offer greater visibility, next-generation IPS and advanced threat functionality without slowing down the network (or at least that’s the plan). That’s the case with Cisco’s next-generation firewall. The networking giant’s Cisco ASA with Firepower Services, released in 2014, integrates Sourcefire’s IPS and Adaptive Malware Protection (AMP). Cisco ranked highest on the enterprise firewall short list, cited by 57% of those surveyed. Roughly the same percentage indicated that they already have Cisco/Sourcefire technologies in their networks, which may point to some of the migration and integration issues that come along with adopting new firewall technology. Cisco is indeed a top choice for firewall evaluation when security elements are added to an existing Cisco infrastructure, according to Gartner, but the addition of Sourcefire’s Firepower has improved the company’s competitiveness in the firewall space.

Like Cisco, the other shortlisted companies -- Check Point Software Technologies, Palo Alto Networks, Fortinet and Juniper Networks -- serve up wide-ranging portfolios of platforms and functionality for different use cases. All of these vendors offer some level of advanced functionality such as threat intelligence options, mobile security integration, cloud instances for sandboxing, and virtualized firewalls for software-defined networking environments. Palo Alto has partnered with VMware to enable its firewall services to work with the VMware NSX network virtualization platform, in an effort to support a software-defined data center.
Innovative technology to watch: Organizations need to tread carefully when they are extending firewall technology to software-defined virtualization environments, however. “You can’t really do the same things that you do in the physical world,” says David Strom, a networking and communications expert and author, who frequently writes about these topics. “I can create 100 VMs today and turn them off tomorrow, so I need to have a firewall that has flexibility.” That means protection and security policies that can operate in that virtual space and understand that the machine instances will go up and down unpredictably, and that it’s a normal behavior, he says. “Whereas if you saw that in your data center, you would think that someone was trying to take advantage of your network.” Some innovative technologies to watch in the software-defined security space include HyTrust and Catbird Security.
“There’s a need to ‘firewall’ more internally as well as externally -- and putting firewalls between separate groups of data center servers or services or other resources often creates problems of scale for older solution architectures,” says John Burke, CIO and principal research analyst at Nemertes Research. Even in their virtual versions these technologies can be "heavy" and in licensing terms expensive, according to Burke.
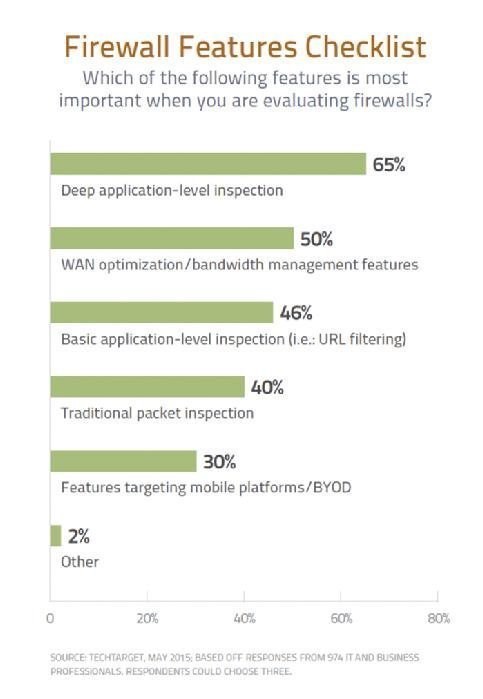
Out with the old: More than 80% of those surveyed said they were looking for app-aware or next-generation firewalls versus traditional technologies. The primary drivers for evaluating new firewall technology:
- Improve performance/speed throughput
- Protect against complex attacks
- Better malware identification
- Select newest tech for planned refresh
Next-generation firewalls all offer some level of application awareness, and the granularity is getting greater. To that end, 65% of readers indicated that they are seeking deep level packet inspection. “It’s not enough to block a port or a particular IP address, but to understand how applications are interacting with the network and how you want to control access to specific applications,” says Strom. “Palo Alto pioneered this many years ago and other people have clearly gotten on board.” Most firewalls have also become much better at geolocation, enabling administrators to block or control access by country or specific circumstances, such as the same user ID logging in from multiple IP addresses in widespread locations.
With all of technology choices and environmental changes, “we see several things going on that should be making folks pay close attention to what they decide to do on their next firewall purchase,” says Nemertes’ Burke. “One is an increasing need to have security solutions that work well as a set -- a unified ecosystem that can work together at a higher level than simply all dumping their logs to the same place.”