Ransomware negotiation: Does it work, and should you try it?
Negotiating with the criminals who are holding your data for ransom is a daunting and stressful endeavor. Experts weigh in on the risks and the potential outcomes.
Industry surveys suggest that, while the number of ransomware attacks continues to rise, businesses aren't paying ransoms as often -- or in as large amounts -- as in the past.
A February 2025 report from cyberincident response firm Coveware reported that 25% of companies hit in the last quarter of 2024 paid a ransom. That was an all-time low, Coveware said, and marked "a significant milestone in the fight against ransomware." The report also found that the median payment was $110,890, down 45% from the prior quarter.
Similarly, Chainalysis, a blockchain analytics company, estimated that ransomware groups collected a total of $813 million in payments in 2024, a 35% decline from 2023's $1.25 billion.
Those numbers indicate some positive news on the cybersecurity front, but they don't make a successful ransomware attack any less of a crisis when it's your organization that's been struck. You'll need to scramble to respond, assess the damage and confront a hugely important question: Do we pay a ransom?
"If your organization is a victim of ransomware, and there is an infection despite your controls, the questions become: First, 'Do we have to pay this?' and 'Are we at the mercy of the ransomware operators?'" said Lee Kim, senior principal of cybersecurity and privacy at the Healthcare Information and Management Systems Society (HIMSS) North America. Answering those questions, Kim and others said, is not an easy task and involves complex considerations.
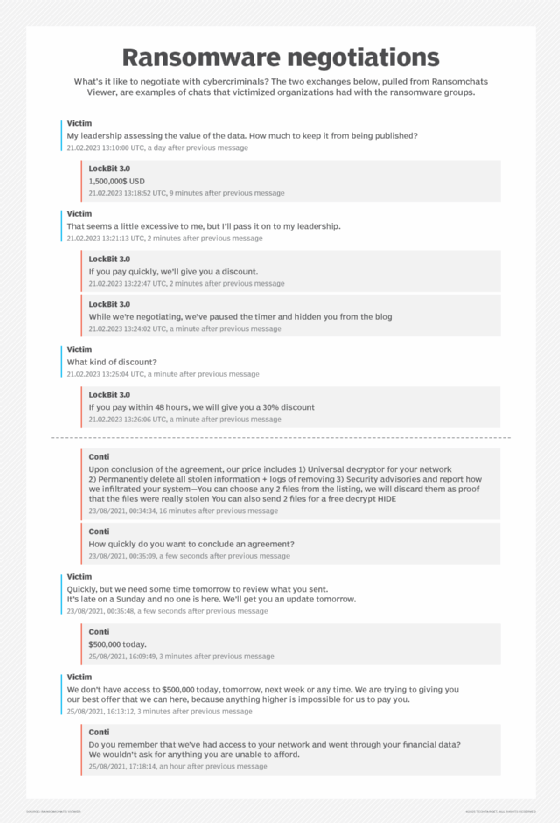
Are ransomware negotiations legal?
The FBI does not encourage ransomware payments. Paying a ransom does not guarantee your organization will get its data back, and, in the FBI's view, payments encourage perpetrators to target more victims and offer an incentive for others to get involved in this type of crime.
Some countries even prohibit paying ransoms. Many nations, including the United States, prohibit payments that would end up in certain countries and other foreign entities. The U.S. Treasury Department's Office of Foreign Assets Control administers and enforces economic and trade sanctions against foreign countries, regimes and individuals deemed a threat.
Several U.S. states, including Florida, North Carolina and Tennessee, have passed laws that prohibit public sector entities from paying ransoms. North Carolina's law forbids public entities from negotiating with threat actors.
How does ransomware negotiation work?
Ransomware attacks can happen days or even months after threat actors have breached an organization's defenses. After doing some reconnaissance, the attackers strike, locking devices, encrypting data and/or extracting data that they threaten to release -- unless the victimized organization pays a ransom.
Ransomware groups might contact the organization via a text file or email. Some reach out through voicemail, while others direct their targets to chat apps or sites on the dark web. It's at this point that a victimized organization must decide whether to engage the hackers in negotiations, said Kyriakos Vassilakos, assistant section chief of the FBI Cyber Division.
The FBI has worked with organizations whose own executives handle the negotiations as well as organizations that use incident response vendors and professional ransomware negotiators. Vassilakos said the FBI does not advocate for one option over the other.
The role of ransomware negotiators
Although threat actors sometimes warn victims against involving others, Vassilakos recommends making one call right away. "Bring in the FBI as early as possible."
In addition to investigating the attack, the FBI can provide expert advice and sometimes even decryption keys. Vassilakos stressed that the FBI keeps victim information confidential.
Others recommend that victim organizations hire experienced ransomware negotiators. Kim noted that a victim's cyber liability insurance policy usually specifies that the organization hires a professional negotiator in the event of a ransomware attack. The insurer might also dictate which negotiator to retain.
Melissa K. Ventrone, leader of the cybersecurity, data protection and privacy practice at international law firm Clark Hill, said negotiations involve technical, legal and financial components that are better handled by seasoned professionals. Negotiators will know how to run checks to ensure payments don't violate national sanctions, and they'll have experience handling the cryptocurrency necessary to make a ransom payment.
Ventrone, whose firm has been involved in ransomware responses but hires vendors to provide negotiators, said executives at victim organizations who try to negotiate on their own learn quickly that they're in over their heads.
Paul Caron, head of cybersecurity for the Americas at S-RM, a global corporate intelligence and cybersecurity consultancy, said the pros typically have law enforcement, military and/or intelligence experience.
Executives at a victimized organization likely will be trying to manage a crisis on little sleep and under high stress. A professional negotiator won't have those pressures and distractions, Caron said. They can focus on the back and forth with the cybercriminals.
Professionals also bring knowledge gathered from prior negotiations, which can aid in resolving the situation more favorably for their client, Caron added.
Kim, a lawyer, said she advises ransomware victims to hire negotiators. In such high-stakes scenarios, most victims can't be as analytical or objective as they should be when negotiating. They might, for example, let slip a detail that could be used against them.
When to consider negotiating with ransomware attackers
While the FBI's position is against paying ransoms, Vassilakos said authorities understand that paying is a business decision.
"The entities have to make the decision that's in their best interests," Vassilakos said, adding that past ransomware attacks have destroyed organizations.
Other legal, security and business leaders share that view, explaining that a ransomware attack forces executives to weigh the cost of paying a ransom against their ability to recover from the attack without paying. Questions to consider include how long the recovery would take, how much that recovery would cost, the value of any lost data and the impact of downtime.
An organization's cyber insurance policy also factors into the decision on whether to negotiate, and policies typically address the point directly, experts said.
Even if an organization won't pay a ransom, negotiations with their attackers might still provide a benefit. Negotiations, which take at least 24 hours and usually longer, can give organizations valuable time to investigate the damage. Ventrone and others said the extra time enables a business to determine whether decryption keys can be located through other channels, whether backup files are sufficient and whether recovery is feasible without paying a ransom.
What are the benefits of ransomware negotiation?
Victim organizations may find that negotiating with the bad actors could yield advantages, experts said. These include the following:
- A lower ransom. Ventrone said payments can range from several thousand dollars to millions.
- A pause to the damage. "If you're communicating with them in the middle of an attack, they'll stop the attack, and they won't launch secondary attacks. That gives the company time to close back doors and time to recover," Ventrone said.
- More time to evaluate the extent of the attack. The time required for negotiation gives teams the opportunity to identify the type of attack, the exact damage, which data is encrypted or extirpated and whether decryption keys are available from the FBI or the No More Ransom project, Kim said.
- A security report. Some threat actors offer to give victimized organizations information about the security gaps they exploited to infiltrate systems. It is possible this information might help to improve cyber defenses, but in some cases the supposed guidance is generic and of little practical use.
- Verification of damage done and that decryption will work. Ventrone said skilled negotiators can elicit proof that the ransomware group has, in fact, stolen what they claim to have stolen. Negotiators should also be able to get the attackers to demonstrate that the decryption methods they provide will actually work.
- Information to share with law enforcement and/or the security community. Caron noted that negotiations could yield useful information, such as the threat actors' country of origin and tactics.
What are the dangers of ransomware negotiation?
Organizations that choose to negotiate with threat actors need to understand the downsides. Engaging with threat actors, according to the U.S. Cybersecurity and Infrastructure Security Agency (CISA), carries important risks, including the following:
- There's no guarantee that an organization will regain access to its data. CISA noted that, in some cases, cybercriminals don't provide decryption keys, even after they've been paid a ransom.
- Cybercriminals could target an organization more than once. Some victims have been extorted to pay more, CISA said, even after paying the original ransom.
- Negotiating might reinforce bad behavior. Businesses that cooperate with hackers might inadvertently encourage others to engage in this criminal activity.
Ethical questions are part of the conversation. "The money is going to criminals," Ventrone said. "The money is not going to 'good'; it's going to 'bad.' So, to the extent we can, we talk to clients about whether that is something they want to consider."
Ransomware negotiation strategies
In partnership with the FBI, the National Security Agency and the Multi-State Information Sharing and Analysis Center (MS-ISAC), CISA developed a guide that offers advice on how to respond to a ransomware attack, advising victim organizations on steps to take during each of the following key stages of an incident:
- Ransomware detection and analysis.
- Reporting and notification.
- Containment and eradication.
- Recovery and post-incident activity.
While lawyers, security professionals and professional negotiators do not disclose the specific tactics they have seen or used in ransomware negotiations, they say negotiations should focus on several goals. Beyond negotiating a lower ransom, Caron said, negotiators should seek to get details on the data that the threat actors targeted as well as proof that the data was taken. They should try to learn the identities and locations of the threat actors as well as other information that can help future victims.
Caron said negotiators work to get ransomware groups to demonstrate that they have the capabilities to decrypt the files they had encrypted. Plus, negotiators use strategies to pace the negotiations to benefit the victims -- that is, whether to proceed swiftly, if the objective is to resume operations as quickly as possible, or move more slowly to gain more time for investigation.
Likelihood of ransomware negotiation success
CISA and others warn that negotiating and paying a ransom to criminals provides no guarantee that there will be a satisfactory outcome, despite what threat actors might promise.
Still, there are indications of a certain self-interested honor among thieves. Ventrone and Caron said they have found that victims who negotiated ransoms usually get what they pay for and are not re-victimized.
"Most of the threat actors, if you pay a ransom, will not attack you again. It's a matter of their reputation. They're making sure they're going to honor their promise so [future victims] will pay ransoms," Ventrone said.
Mary K. Pratt is an award-winning freelance journalist with a focus on covering enterprise IT and cybersecurity management.







