Product review: Juniper Networks SRX Series UTM appliances
The market-leading Juniper Networks SRX Series of UTM boxes are feature-rich products that may cause implementation headaches.
The Juniper Networks SRX Series of unified threat management boxes is probably the most feature-complete of any UTM product, offering the most options and support for infrequently used security items. Juniper is a thought and market leader in the enterprise UTM market, particularly at the highest end, though its products are used in a wide variety of network security situations.
Product specs
Juniper offers seven different SRX models, from small units for branch offices to large models for supporting the largest of networks. The rated throughput firewalls range from 700 Mbps to 200 Gbps, which are the highest throughput levels I've seen advertised. The smallest units come with eight 10/100 Gigabit Ethernet ports, while the largest ones have a variety of 40, 10 and 1 GbE ports.
Key features
The smaller SRX units come with integrated antimalware and antispam, but these aren't on the larger boxes; the assumption is that larger networks will probably have some other product in place. But if an enterprise needs them, Juniper offers the most choices of any of the boxes I tested, including antimalware scanning and URL filtering. If businesses choose Kaspersky for antimalware, its scanner has to download and will scan everything on the box itself. If enterprises use the Sophos scanner, it is processed in the cloud without impacting the box's CPU or other resources.
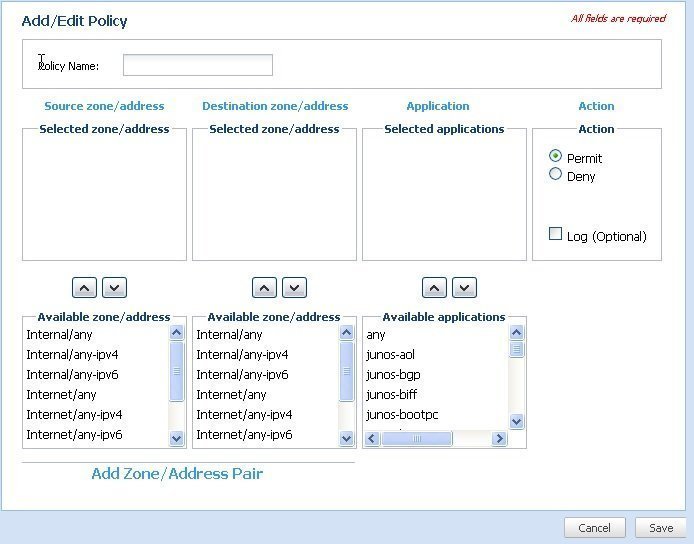
Juniper has also spent some time integrating its world-class applications firewall features into the SRX, making it more competitive and complete than some of the other UTMs. As new threats appear, it is nice to have better applications intelligence at the network perimeter.
Performance
As I said earlier, Juniper is designed for the largest networks and delivers the throughput accordingly. But Juniper is a study in contrasts. Its products have very capable features, but they are hidden away in places that only a real expert will be able to find and use properly. When I did my review, I had the benefit of having a Juniper system engineer sitting at my side and even he needed to search for the right command syntax to complete certain tasks.
However, it's important to note that Juniper UTM boxes can probably do things that no one else can easily do because of their power and flexibility, such as the ability to roll back a particular update to its policies if one is created in error.
But also note...
SearchSecurity's UTM how-to-buy guide
An intro to buying a unified threat management appliance
Product review: Dell SonicWall NSA
Product review: Check Point UTM
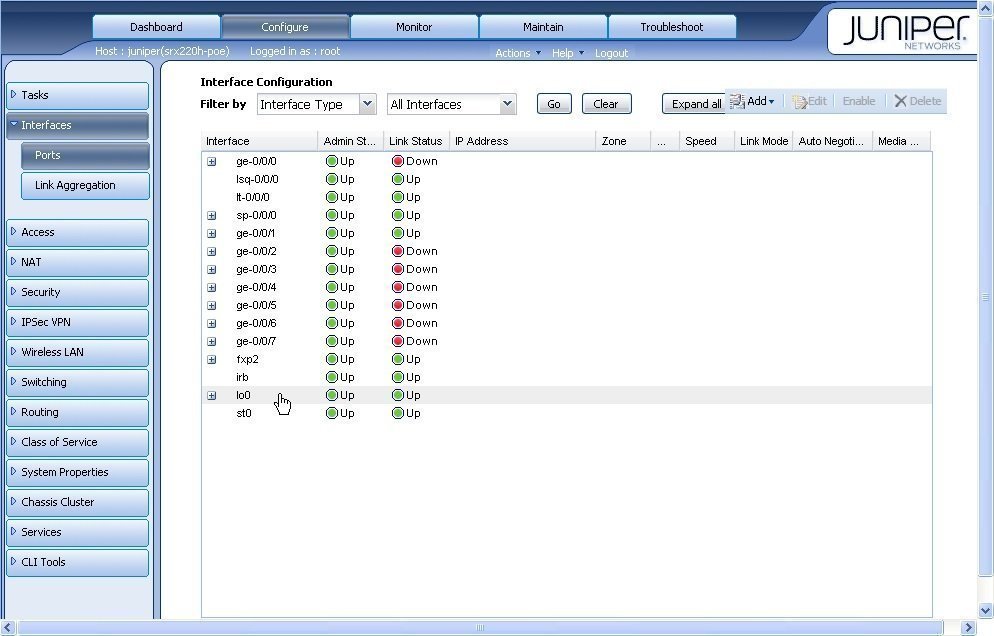
Setting up the SRX is somewhat vexing because of its suffering and vastly incomplete Web-based interface. Juniper actually has three different user interfaces: Web, command line and one that is a holdover from its acquisition of Netscreen's line. Many admins will likely suffer from headaches as they type on the box's command line and have to look up the command syntax. Fortunately, it does have a few setup wizards that will walk users through the initial process, but even so some of the initial routing settings aren't obvious.
Juniper also sells its older Netscreen-based SSG line for smaller networks without some of the integration and security features found in the SRX line. Navigating these two various product lines can be somewhat confusing. The SRX is based on JunOS, the same operating system that runs Juniper's leading firewall line, with the added UTM features.
Pricing
The price points of the SRX line falls between Check Point and SonicWall. The least expensive model costs $2,456 for the first year, $1,700 of which is software licenses for the various modules. The most expensive model costs $59,750 for the first year, of which half is in software costs. Juniper offers three different support contracts under its Juniper Care label that span the range of on-site and off-site options.
|
About the author:
David Strom is a freelance writer and former editor in chief of several information technology publications. He has written for many TechTarget properties since 2000. His blog can be found at strominator.com and is @dstrom on Twitter.
Author's note: The contributor does not have a paid relationship with any of the vendors mentioned in this article.