No relief in sight for ransomware attacks on hospitals
Despite being off limits for some hackers, hospitals continue to be lucrative targets for ransomware groups because of their valuable data and higher rate of paying ransoms.
Despite an apparent decline in activity against hospitals during 2022, ransomware attacks have continued to endanger medical care and patient health this year and show no signs of abating.
Ransomware gangs typically have not restrained their avarice for healthcare organizations. Despite the pledges of some gangs in 2020 to refrain from attacking medical facilities during the COVID-19 pandemic, ransomware attacks continued to plague the industry across the globe. While U.S. law enforcement agencies have focused more attention on threat groups that target critical infrastructure, that scrutiny -- and potential for causing patient deaths -- has not deterred some ransomware gangs from attacking hospitals.
Cybersecurity vendor Emsisoft recorded 25 ransomware attacks on healthcare organizations, including "hospitals and multi-hospital health systems" in 2022, affecting as many as 290 hospitals across the country. That number is a significant decline from 2021, when Emsisoft observed 68 attacks on healthcare providers.
But U.S. hospitals and medical centers are still popular targets for threat actors. According to Check Point Research, the sector was the most targeted industry for ransomware attacks during the third quarter of 2022.
Attacking the healthcare sector, which often means impairing medical services and jeopardizing patient health, is considered unethical even by some cybercriminals. However, this is no deterrent for some ransomware gangs, especially with the potential value in attacking healthcare. In addition to encrypting IT systems, ransomware actors often target lucrative data in healthcare computer systems.
As electronic healthcare record databases grow by the second, threat actors see the sector as a vast landscape for monetization. In addition, technological advances create endpoints for cyber actors to subsidize from sensitive data on the dark web or via ransom payment.
"The attack threat actors are making a huge amount of money from all cyber attacks. But the healthcare information is so valuable to them," said Deryck Mitchelson, field CISO for EMEA at Check Point Software Technologies. "They can commoditize up very easily on the dark web."
In Sopho's "State of Ransomware in Healthcare 2022" report, the threat detection vendor found that 66% of the 381 healthcare organizations involved in the study were victim to ransomware attacks that year -- an increase of about 50% from 2021. Healthcare computer systems are complicated environments to secure. To maintain swift medical procedures, the necessary safeguards are sometimes neglected, leaving data vulnerable for attackers.
"If you can't issue their medicine in a timely manner in an emergency room or you can't access a record to determine what somebody's allergies might be like, these things are literally life and death choices," said Chester Wisniewski, field CTO of applied research at Sophos. "Often, systems get left a lot more open for the convenience of providing care."
Moreover, infosec experts have long argued that the environment under which medical professionals work leads them to quickly open emails, making them susceptible to phishing attacks.
"They do tend to respond quickly, click on things quickly," said Mitchelson. "They're often walking in between doing things, so they're doing things on the move. That's why phishing emails are something that you see that's one of the highest vectors."
The burden on hospitals
Ransomware attacks come with heavy expenses, as victims frequently experience company downtime where IT and/or power restoration may be required. It can be especially painful for healthcare organizations. Sophos' study showed recovery on average lasted one week and cost healthcare providers an average of $1.85 million in 2022.
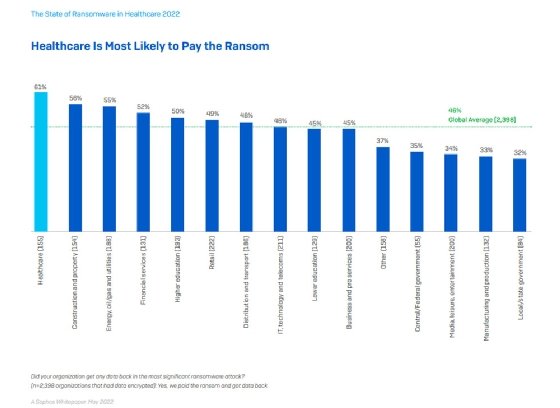
Ransom payments are an additional expense for companies. Sophos' study found the healthcare sector paid a ransom in about 61% of incidents, up from 34% in 2020 and the highest rate of any vertical industry in its 2022 study.
Mitchelson said the payment rate is typically high because U.S. healthcare organizations primarily operate within the private sector, and executive teams can make their own decision to pay a demanded ransom. But in Europe, he said, many healthcare organizations are publicly funded and government operated and, therefore, are much less likely to pay. The situation is like the education sector in the U.S. For example, K-12 schools rarely pay a ransom because they function under the supervision of local governments and require approval to use taxpayer money for such expenditures.
Paying threat actors not only perpetuates a cycle of ransomware targeting on healthcare but also funds their operations, which can improve the cybercrime tools and attacking strategy.
"It tells them that the sector pays, so the chance of them attacking the sector increases," Mitchelson said. "They're able to use the money to invest in developing better ransomware kits that they can deploy or [developing] better ransomware as a service to deliver the payloads or just [hiring] more attackers."
Therefore, it's not ideal for healthcare organizations to pay, especially with the additional and inevitable remediation and recovery costs. However, without the proper safeguards and best practices, such as regularly patching systems, employing effective backups and establishing an incident response procedure, organizations can find themselves in a quandary. The pressure of quickly recovering from an attack and resuming patient care often means paying a ransom.
Compounding the problem for U.S. hospitals is that most do not have large cybersecurity budgets. T.J. Ramsey, director of threat operations at Fortified Health Security, said investing in quality medical equipment and assistance typically offsets any urgency for healthcare organizations to update systems and create backups. Healthcare systems do not have the funding to heavily invest in these cybersecurity defenses.
"Healthcare in general -- even major hospitals -- often operate on a budget of 2 to 5% in total of their net patient revenue," Ramsey said. "Patient care, preservation of human life and the delivery of medical services is going to be the number one concern for anybody."
Patient information and health at risk
Deficiencies in cybersecurity not only rack up costs for health centers, but they also lead to compromises of patient data and personal health information (PHI). This has become increasingly common over recent years.
Fortified Health Security found 51.4 million records were breached in 2022, an increase from 49.4 million in 2021.
Jama Health Forum conducted a study on 374 ransomware attacks on healthcare delivery organizations from 2016 to 2021. It found that threat actors exposed the PHI of more patients as time progressed. To make matters worse, the study showed the likelihood in restoring encrypted or stolen data from backups decreased over that period. On average, only one out of five organizations could restore their data from backups.
Some of these attacks impacted hundreds of thousands of patients. In April, Yuma Regional Medical Center in Arizona suffered a ransomware attack in which threat actors obtained the PHI of 737,448 patients; files were encrypted and exfiltrated from systems.
CommonSpirit Health, an umbrella organization with 150 hospitals and 2,000 healthcare sites, also took a big hit last fall when a ransomware attack compromised PHI of 623,774 past and current patients. The ransomware attack on CommonSpirit caused procedural disruptions like inaccessibility to patient portals, cancellation of appointments and redirection of ambulances to other hospitals.
More than that, some health systems argue that attacks are directly causing a loss of human life. According to the Ponemon Institute, 22% of healthcare organizations claim that ransomware attacks led to an increase in patient mortality rates in 2022. While some patient deaths have resulted in legal action and law enforcement investigations, there are no confirmed cases as of yet that directly attribute fatalities to an attack.
Are ransomware actors apologetic?
The dire impacts of ransomware sometimes cause threat groups to retreat in the name of reputability. Last December, ransomware group LockBit hacked into SickKids, a children's hospital in Canada, which delayed disclosure of lab and imaging results for patients and families resulted.
Two days later, LockBit apologized to the hospital, blaming the attack on a rogue affiliate. The group returned the decryption key at no cost.
Like many other security professionals, Ramsey found the apology insincere. "You have to remember we're dealing with a criminal element here," said Ramsey. "They might feign apologies or [play] to their emotional side there. We're a caring species; we, by default, want to be helpful to one another. But at the same time, you're dealing with the bad guys here."
Other ransomware gangs have apologized for their invasions in the past. In 2021, ransomware gang Conti attacked Ireland's public health system, compromising 54 hospitals and 4,000 other healthcare locations. Amid intense law enforcement pressure, the group provided the decryption key for free.
Despite that gesture, the now-defunct Conti group was known to attack healthcare systems. Jeremy Kennelly, Mandiant senior manager of financial crimes analysis at Google Cloud, said that one third of publicized attacks by UNC2727, a cybercrime group associated with Conti ransomware, were against the healthcare sector. Even with the occasional apologies and amends, there are currently no indications that ransomware groups will cease attacks on healthcare organizations.
Will Hive's defeat have an impact?
In January, the FBI announced that it had infiltrated the Hive ransomware gang's network and obtain decryption keys for hundreds of victims, saving them $130 million in ransom payments. Authorities also seized the gang's infrastructure and took down its dark web site.
Hive ransomware, notorious for their attacks on healthcare, was first observed in June 2021. Since then, Hive has affected over 1,500 victims globally and accumulated $100 million in ransom exchanges. In December, Hive claimed responsibility for a ransomware attack on Lake Charles Memorial Health System, which compromised nearly 270,000 patient records.
While it represents a major victory in the fight against ransomware, the Hive takedown may not have much of an impact on the overall threat landscape. Threat researchers believe the upward trend of attacks will only continue to grow this year. In 2023, there have already been several ransomware attacks on healthcare organizations, including a recent attack on Atlantic General Hospital in Maryland.
In addition, the ransomware as a service (RaaS) market has demonstrated resilience over the years, with many operators shutting down their sites and later forming new RaaS gangs with different names but similar code and tactics. Affiliate hackers working for Hive may simply shift to Vice Society, Lock Bin or another competing RaaS.
"It's just causing a small amount of disruption until they all continue and go again," Mitchelson said. "There are clear trends that there are more and more criminals within these gangs. The numbers are actually going up, and the groups are thriving despite us taking them down."







