MDM vs. MAM: What are the key differences?
Mobile workers are productive and even essential to business success. But IT has to protect corporate apps and data -- as well as worker privacy -- via MDM, MAM or both.
BYOD sets up a huge productivity improvement for workers and a huge challenge for IT staff. IT departments need to secure business applications and data on personal mobile devices without affecting personal data. They also must deploy devices, patches and updates and account for lost devices.
Apple's introduction of the iPhone in 2007 caused a paradigm shift in how IT departments manage user devices in a corporate environment. IT staff totally controlled PCs, laptops and tablets, enforcing security, hardware and software policies. Smartphones, sophisticated mobile devices and related apps created BYOD, where employees use their personal mobile devices for work.
Mobility management products have evolved over the years to protect mobile devices, apps and software, as well as content, and address other security concerns. Unified endpoint management (UEM) products combine the ability to manage desktops, laptops and tablets along with mobile devices and software. Categories of mobile management products include the following:
- mobile device management (MDM) to manage corporate-owned devices;
- mobile application management (MAM) to control corporate-owned software;
- mobile email management (MEM) to enforce security and policies for corporate email on mobile devices;
- enterprise mobility management (EMM) for all mobile management, including MDM and MAM;
- UEM for EMM plus desktops, laptops and tablets under IT's oversight;
- mobile information management (MIM) for device-agnostic mobile data security; and
- identity and access management to handle login and security configuration and management.
MDM and MAM are at the core of mobility management tools (see Figure 1). IT management must determine which products they need based on the features, strengths and weaknesses of MDM vs. MAM. Understand how these mobile strategies differ and can complement one another.

What is MDM?
MDM products evolved as a means to centrally control mobile endpoints. For years, IT had mature tools, such as Microsoft's Group Policy Object for Windows PCs, but lacked policy enforcement in a comprehensive fashion on mobile devices.
MDM products are deployed to enforce policies on corporate-owned mobile devices but also work in BYOD settings. MDM products are becoming more flexible as options to secure personal data on devices. MDM can ensure device encryption, a strong PIN code and that the device screen-locks after a certain idle period. IT organizations can use an MDM tool to remotely wipe a mobile device if it is lost or stolen. With a BYOD strategy, this might be the limit of what IT staff can do with MDM.
The full gamut of MDM functionality includes GPS tracking, as well as an inventory of installed applications and other items. Employees resist this kind of corporate oversight on their personal devices. Conversely, with company-owned devices, an MDM strategy might incorporate these higher functions. Mobile platforms in education are another good example of where heavier device management makes sense.
Many companies have some form of MDM in the corporate environment. A $1.69 billion industry in 2017, MDM has grown to $4.3 billion in 2020 and is expected to reach $15.7 billion by 2025, according to research by MarketsandMarkets. This growth is fueled, in part, by the exponential increase in the mobile workforce during the COVID-19 global pandemic.
Cloud-based SaaS versions of MDM products are expected to grow in the next five years. Cloud-based MDM tools are accessed over the internet, rather than installed and maintained in the corporate data center.
What is MAM?
IT organizations can set policy on a more granular level with MAM vs. with MDM. MAM products address MDM's shortcomings in BYOD because MAM deemphasizes the device and focuses on the application level.
MAM tools secure web browsers, email clients and other applications so that employees can do work tasks on personal devices. They also can provide an internal app store of private, approved and licensed public applications, such as Evernote and Salesforce.
Other MAM features include the following:
- app configuration;
- app catalog;
- volume licensing support;
- app updating;
- app performance monitoring;
- default and custom policies; and
- app security by keeping corporate and personal data separate.
Mobile users who need access to the corporate intranet or other internal website can do so via a securely wrapped web browser that doesn't require a VPN client. They can work on a containerized email client that the organization manages, regardless of where the client is running and of who owns the device.
Vendors might offer a MAM product that focuses on email as an MEM tool. MEM products can deliver a vendor-supplied email client or provide a management framework around the native email clients built into iOS and Android. MEM technologies set policy on email forwarding and encrypting and otherwise protect corporate information.
MDM vs. MAM: Differences and similarities
The line between MDM and MAM has blurred as the enterprise mobility market matures. While these two technologies originally were marketed as separate products, they are usually both included in EMM or UEM product suites. While MDM is commonly listed as a feature in EMM and UEM products, MAM might only be identified by features.
The key differences and similarities between MDM and MAM include the following.
Use case. MDM makes sense if the corporate IT organization has complete control over the device. A company-issued smartphone or tablet, for instance, is simply a mobile version of the company-issued laptop. This is typically not true for BYOD devices. MAM is common for BYOD devices, controlling only certain applications, such as enterprise apps and ones used solely for business purposes.
App management. MDM controls apps by controlling the device. MAM controls apps with specific features, such as a vendor-supplied app catalog, which customers typically can modify.
MAM and MDM both provide app wrapping and app containerization features. Through these technologies, IT staff can control, secure and update apps on managed devices.
User and group authentication and authorization. Access management, including for third-party product integrations, is typically included in enterprise mobility product suites. These capabilities are part of MAM and MDM.
In UEM and EMM products, MAM and MDM are typically not purchased separately. Both MDM and MAM, along with security and other packages, fall into these product lines. Examples include the following:
- IBM MaaS360;
- ManageEngine Desktop Central;
- Microsoft Intune;
- Citrix Endpoint Management;
- VMware Workspace One; and
- Hexnode MDM.
Jamf for Apple devices also has specific MDM and MAM offerings.
One of the presumed benefits of MDM and MAM is improved security. However, CISOs and other infosec professionals are realizing that MDM and MAM are not a panacea to the complex mobile security question. Data is the prize for hacking any device, and mobility changes little in that equation. MDM and MAM address data security by encrypting the device or the specific document at rest. Once the device is unlocked and the data is in use, however, little prevents data leaks. Companies need to promote secure consumption of data, regardless of where it is located or being consumed.
App security for BYOD and COPE
BYOD challenges corporate IT staff to secure business apps on potentially insecure devices. Allowing personal email and other software installed by the employee on corporate-owned devices -- whether personally enabled or not -- is equally challenging. How is IT supposed to protect corporate data in both BYOD and corporate-owned, personally enabled (COPE) scenarios?
IT teams might be confused about the approach and whether MDM or MAM is the answer. Myths include the following:
- MDM does not allow users to put personal apps and data on the device.
- MAM only applies to BYOD devices.
- App wrappers and containers only exist in MAM setups.
Part of this confusion is caused by fast-changing mobile technology. Not long ago, the above statements were true.
Currently, the following statements are facts:
- COPE devices can use MDM or another device-centric management strategy and tools and still permit users to run personal apps.
- Personally owned devices, primarily populated with personal apps and data, can safely and securely host corporate apps and data.
- IT admins can remotely update, control and wipe apps and data from a mobile device without affecting a user's personal apps. This is true on COPE and BYOD setups.
- App wrapping and app containerization are available for MDM and MAM.
- MAM provides tools for regulatory controls and enforcement.
Application wrappers and application containers
Application wrapping and application containerization (see Figure 2) enable the flexibility in MAM and MDM for personal and corporate apps and data to coexist. While wrappers and containers are similar, there are differences between these approaches.
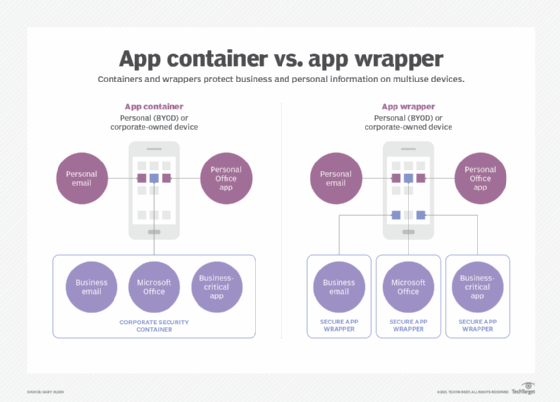
App containerization. Some UEM products provide an SDK for customers to develop code-based containers directly into the apps. Tool vendors also might supply the containers.
These containers enable the mobility management tool to work with the apps. They separate the app securely from the device user's personal data.
App wrapping. Wrappers work via dynamic libraries layered over the application's compiled code. Customers can define custom security encryption for an application. Some mobility management tools offer an SDK for customers to build wrappers.
Containerization works on a group of applications, while wrappers work on a single-application basis. Wrappers do not require access to source code via the management console. While wrapping is an easy way to bolster application security, it lacks features and capabilities of containerization.
Table 1 shows comprehensive UEM products that offer app wrapping and containerization.
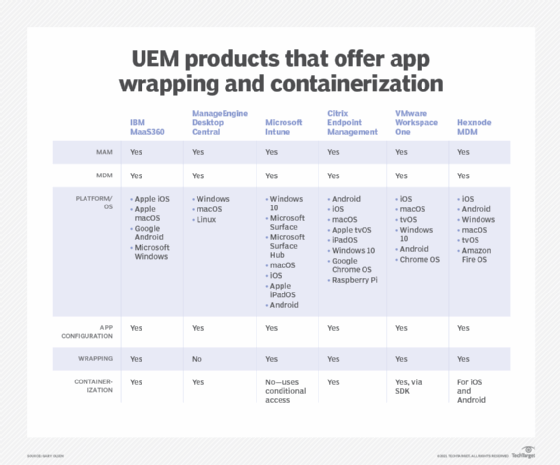
Comparing these products demonstrates that both MDM and MAM, through app wrapping and containerization, can solve a business's mobility management problems. The choice depends on if IT wants to control the devices, among other factors.
Virtualized mobile access
Another approach to mobile management is a corporate workspace accessed via a virtualized remote desktop or Windows application. Desktop virtualization products, such as Citrix Virtual Apps and Desktops or VMware Horizon, work on mobile devices. With these products, the data is never directly accessed from, or left on, the device itself. Desktop virtualization's appeal is this security.
A drawback of virtualized mobile access is that many of the consumerized platforms don't provide an optimal experience on handheld devices. Remote desktops or applications frequently need a keyboard, mouse and large display for effective use. The virtually presented application or desktop is not available offline, but workers on the go commonly find themselves without internet access. Additionally, while the data may start in the remote workspace, there is no guarantee that it will remain there. A user can simply copy a file to Dropbox or forward a sensitive document to Gmail, for example, and bypass IT's controls.
MIM for information and user policy
Mobile information management manages information and how mobile devices use it. Information, in the form of data, can be almost anything: email, documents, photos or video. Organizations that fall under local, federal and international regulations have much to worry about if that data is breached or leaked.
A blend of MDM, MAM and MIM functionality is grouped as enterprise mobility management or unified mobility management. Many products blur the lines among device, application and information management, making them effective for diverse use cases. Carefully review products to match corporate needs.






