ICS kill chain: Adapting the cyber kill chain to ICS environments
As IT/OT convergence continues to gain traction, industrial control system security cannot be ignored. Performing pen tests based on the ICS Kill Chain can help.
A cybersecurity kill chain is a framework that helps security teams understand the sequence of events during an external attack. Derived from the military concept that identifies the steps in a military attack, a cyber kill chain breaks a cyber attack into steps to help security analysts understand the behaviors and tactics of threat actors.
SANS Institute released the Industrial Control System Kill Chain in 2015 to help analysts understand attackers' behaviors and tactics specifically in ICS attacks. Based on Lockheed Martin's IT Cyber Kill Chain, the ICS Cyber Kill Chain accounts for specific ICS security threats and the layered nature of ICS environments today.
The ICS Kill Chain is especially useful when conducting risk assessments and pen tests against ICS environments. In Chapter 17, "Penetration Testing ICS Environments," of Industrial Cybersecurity, Second Edition, author Pascal Ackerman describes the ICS Kill Chain, including its evolution from the cyber kill chain, steps and phases, as well as how to base pen tests on the ICS Kill Chain. Download a PDF of Chapter 17 for more on ICS pen tests.
The ICS Cyber Kill Chain
Due to its unique features and deployment, the ICS requires considerable knowledge about the target's industry -- the ICS environment -- to be able to carry out a successful attack. These unique challenges of an industrial control system require the attacker to avoid interfering with the multitude of sensors and controls and automation devices while performing the attack, as well as being able to pivot through multiple layers of networks that are usually found in such environments (the internet to enterprise networks, to the industrial network to enclaves, and so on).
To put these unique challenges into perspective, the SANS Institute (https://www.sans.org/about/) published a report in 2015 that adapts the Cyber Kill Chain to industrial control system environments. This report expands upon the original Intrusion Kill Chain stages by, among other things, dividing the stages into two distinct phases, with the purpose of articulating the ICS characteristics. The following diagram shows the first phase of the ICS Kill Chain:

This first phase is quite similar to the original Kill Chain model and corresponds to what was traditionally called espionage or intelligence operations. Phase 1 reflects the activities and processes of a structured and targeted attack campaign aimed at obtaining the initial foothold into an organization's enterprise/business network. Within this model, the following stages take place:
- Planning: This is the first stage of the first phase of the attack and includes reconnaissance tasks that aim to collect relevant information about the target. Typically, this involves the attacker perfuming targeted research using open source intelligence (OSINT). The reconnaissance process leverages publicly available information such as search engines, corporate blogs, product notes, employee's social media and support forum posts, as well as the use of Shodan and Censys type tools. All these efforts aim to identify the target's public presence and potential weak spots.
- Preparation: The objective of the preparation stage is to plan out the attack path to gain an initial foothold into the target network. This stage may include both preparing the exploit to use in following stages, as well as selecting the victim system(s) for the attack. During this phase, the appropriate tools for the exploit and target will be selected and tested. Both the distinct tasks explained in this stage may take place, but neither is necessarily performed here.
- Intrusion: The intrusion stage includes any attempts to access the target networks and systems, regardless of whether these attempts are successful. If the attacker does successfully gain access to the target's network or systems, the attacker shall then try to exploit the target with the purpose of installing some form of persistence into the target environment to ensure their future access.
- Management and enablement: After successfully intruding the target network, the attacker will want to manage the access they've obtained. For this purpose, the attacker often deploys one or more command and control (C2) systems. This allows the attacker to set up reliable channels in the victim's (enterprise) network by means of implants. We looked at the PoshC2 command and control structure back in Chapter 16, Red Team/Blue Team Exercises.
- Sustainment, entrenchment, development, and execution: In this stage, the attacker will try to accomplish the goals and objectives of the first phase of an industrial cyberattack. Common objectives of the first phase include finding the industrial systems or equipment that are going to be part of reaching the second-phase objectives. If the target has a segmented network, the objective is to find a way to pivot into the industrial segment/network. Successfully completing this stage indicates the beginning of the second phase of the attack.
When the attacker has successfully compromised the target, phase 1 of the ICS cyberattack is considered complete. The attack will continue with the second phase. Note that in some cases, phase 1 of an attack is not implemented. This can be the case where access to the industrial network is gained some other way, such as through an internet exposed ICS system or device or if the attacker comes in through a supply chain compromise, such as a breached vendor or engineering/support company.
The following diagram shows the second phase of a typical ICS cyberattack:

In the second phase, knowledge that was collected during the first phase of the attack is used to prepare the attack on the ICS environment. This phase could follow directly after successfully completing phase 1, but a delay between phases is possible.
Typically, the following stages are part of the second phase of the Cyber Kill Chain:
- Planning: During the planning stage of the second phase, the attackers will plan the attack path, choose and define any tools and exploits that will be used, and generally try to make sure they develop their capabilities so that they successfully complete the unique challenges for the target's ICS environment.
- Validation: During the validation stage, the attacker will certify the (new) capabilities required for the ICS attacker in an identical or similar environment as the victim's ICS setup. The idea is that by practicing the attack on a simulation of the victim's environment, the attackers get the chance to test, plan, prepare, and practice the attack, with the hope to avoid mistakes that can prevent them from reaching their objectives. This is a great challenge for the attackers, since simulating an entire system such as those used in ICS environments is a highly complex and time-consuming task.
- ICS attack: This is the final stage of the ICS Cyber Kill Chain. During this stage, the attackers will perform the ultimate objective of the entire cyberattack. This is what the attack is all about. The objective can vary from stealing secret information, disrupting the production process, industrial espionage, hacktivism goals, or even more sinister objective such as causing damage or harm to the environment or employees.
With that, we've explained the ICS Cyber Kill Chain, detailing how attackers go through distinct attack phases and stages to reach a certain objective. Next, we will learn how to use this model while performing penetration testing engagements.
Pentest methodology based on the ICS Kill Chain
So, how does this fit into the task at hand; that is, performing ICS penetration test engagements? Let's look at a high-level overview of the ICS Cyber Kill Chain:
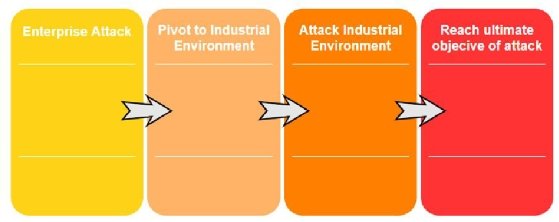
Here, we can see that there are four main steps:
- Getting into the enterprise network (unless we are lucky enough to find internet exposed industrial equipment).
- Find a way to pivot into the industrial environment.
- Find a path to the objective by attacking and exploiting the industrial environment.
- Once the path has been laid out, fulfill the ultimate objective of the attack.
To make our penetration test engagement as accurate as possible to the real-world attack approach, we shall tailor the engagement around these four main steps. The specific implementation (tools, techniques, and procedures used) of the engagement should be tailored to the target organization and environment and take into account aspects such as rules of engagement (what is off limits, when, what, how, and so on), the target's ICS environment, and other unique characteristics.
More on Industrial Cybersecurity
Check out an interview where Ackerman explains the basics of ICS security monitoring.
Plus, learn about the concept of the industrial DMZ from Ackerman.
About the author
Pascal Ackerman is a seasoned industrial security professional with a degree in electrical engineering and more than 20 years of experience in industrial network design and support, information and network security, risk assessments, pen testing, threat hunting and forensics. His passion lies in analyzing new and existing threats to ICS environments, and he fights cyber adversaries both from his home base and while traveling the world with his family as a digital nomad. Ackerman wrote the previous edition of this book and has been a reviewer and technical consultant of many security books.







