
stock.adobe.com
5 application security threats and how to prevent them
The most widely known application security threats are sometimes the most common exploits. Here is a list of the top app threats and their appropriate security responses.
The most common application security threats are those most known to cybersecurity experts. So, why do these vulnerabilities persist? Often, it is because organizations do not take enough precaution to prevent them.
Developers, security teams, managers and organizations should use this list of known application attack vectors to their advantage. By becoming more security-aware at every level, companies can better avoid security incidents and their potentially costly damage.
SQL injection vulnerabilities
SQL injection is among the worst application security threats. Not only do SQL injections leave sensitive data exposed, but they also enable remote access and control of affected systems. Outsourcing web application development and hosting, as well as lack of adequate continuous security testing, contributes to its persistence.
To combat SQL injection, organizations must start by acknowledging it. Mitigation requires the right tools and sophisticated vulnerability and penetration testing (pen testing). Commercial vulnerability scanners and source code analyzers detect application security threats, such as SQL injection. Note, organizations should use multiple analyzers because no single scanner will uncover everything.
Learn more about how to detect and prevent SQL injection to avoid data breaches.
Cross-site scripting attacks
Cross-site scripting (XSS) vulnerabilities are essential for successful application hackers, system administrators and pen testers to understand. They're not new -- in fact, XSS vulnerabilities have been exploited for more than two decades. Successful XSS attacks enable bad actors to steal or forge cookies to impersonate valid users. As a result, attackers can use privileged accounts to do everything from alter content to carry out remote code execution.
There are three types of XSS attacks: reflected, Document Object Model-based and stored XSS exploits. Learn how validating user input, escaping special characters and encoding output, as well as avoiding certain sinks, can prevent XSS attacks.
Buffer overflow attacks
Buffer overflow attacks, often the result of bad programming, are a favorite exploit for bad actors. They take place in a fixed-length block of memory or buffer. When a program or process attempts to input more data than the buffer is designed to hold, it will overflow -- enabling attackers to crash, control or modify the system.
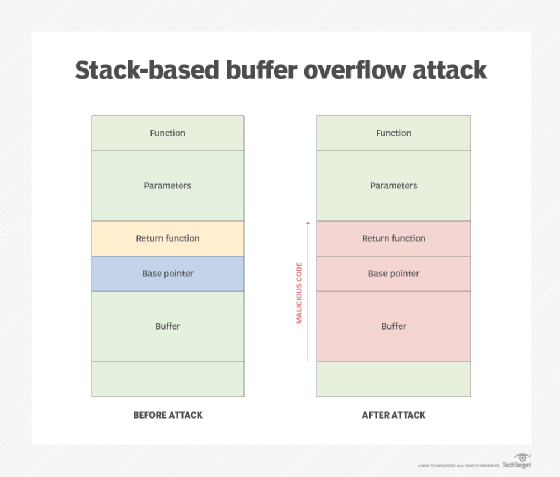
Most commercial applications have patches available to mitigate buffer vulnerabilities. But applications developed in-house are just as susceptible to buffer overflow, and vulnerabilities may fly under the patching radar.
Read up on the four kinds of buffer overflow attacks and how to defend against them.
CSRF attacks
A cross-site request forgery (CSRF) occurs when an intruder disguised as a legitimate user attacks a website or application. The bad actor manipulates an authenticated user, who is often unaware of the attack, into executing unauthorized actions. Users may be duped into sending HTTP requests, enabling sensitive data to be returned to the hacker. Potential damage includes modified firewall settings, fraudulent financial transactions or email address changes. If the forgery victim is an administrator, a CSRF attack can put the entire application at risk.
CSRF attacks, sometimes described as reverse XSS attacks, are more challenging to prevent than XSS. For one, they are less common. It can also be difficult to confirm whether a user's HTTP request was intentional.
Security measures to prevent CSRF -- for example, frequent authentication requests -- may be met with user aggravation. Cryptographic tokens can be used to provide persistent authentication.
Find out more about the anatomy of a CSRF attack and how to reduce risk.
Broken access control vulnerabilities
Access control is a security measure that determines and regulates which users and processes can view or use resources in a given environment. It is designed to reduce risk to an organization. Broken access control occurs when there is a lack of or insufficient central access control. Even in situations where organizations are secure from unauthenticated users, bad actors can masquerade as a user trusted by the system -- for example, when there are gaps in a system's access control that can lead to a hacker's or malicious insider's admittance to sensitive data or resources. International hackers took advantage of this application security threat in 2012; they infiltrated a South Carolina Department of Revenue server's broken access control via a simple spear-phishing attack, exposing an estimated 3.8 million Social Security numbers and nearly 400,000 credit and debit card numbers.
Organizations must prioritize access control. Beef up security by implementing the principle of least privilege and role-based access control, which limit user access rights to the bare minimum necessary for job function. Ensure developers include access control units and orchestrate a solid identity and access management (IAM) framework to manage digital identities.
Consult this three-part guide to IAM best practices, which includes how to manage nonusers and cloud, to avoid potential consequences of broken access control.








