How to define cyber-risk appetite as a security leader
In this excerpt from 'The CISO Evolution: Business Knowledge for Cybersecurity Executives,' learn how to define and communicate an enterprise's true cyber-risk appetite.
It's a truth universally acknowledged that virtually every company with internet connectivity assumes some degree of cyber-risk -- the only way to eliminate it entirely is to close up shop. Exactly how much risk an organization shoulders should depend on its risk appetite, according to the Committee of Sponsoring Organizations of the Treadway Commission (COSO), a group that studies enterprise risk management. Clearly and accurately establishing a company's cyber-risk appetite and communicating it in business terms throughout the organization are critical challenges for the CISO.
In this excerpt from Chapter 6 of The CISO Evolution: Business Knowledge for Cybersecurity Executives by authors Matthew K. Sharp and Kyriakos "Rock" Lambros, Lambros explains how to define an organization's cyber-risk appetite, how to differentiate cyber-risk appetite from cyber-risk tolerance and how to communicate all of the these points to the business. He also offers a detailed cyber-risk appetite statement example to illustrate his points.
COSO defines risk appetite as "The types and amount of risk, on a board level, an organization is willing to accept in pursuit of value." Sounds simple enough, but I cannot begin to tell you how many times I have been asked about how an organization goes about defining their risk appetite and, more importantly, their cyber risk appetite. It seems to be an elusive magical purple unicorn because most organizations do not actually codify their risk appetite. Defining a risk appetite is fundamental to risk management and how organizations communicate and react to risk. Managing risk within the boundaries of risk appetite should be consistently shared and addressed throughout the organization as it provides the guardrails against which to manage risk.
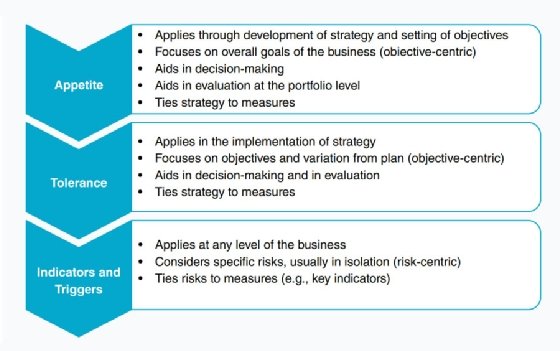
We often interchange the terms risk appetite and risk tolerance, but they are distinctly different. Risk appetite is only part of the overall approach to managing risk. Risk appetite needs to cascade throughout the business as risk decisions must be made at different levels or business units. Each individual level or unit may have different risk tolerances around the risk appetite. While risk appetite refers to how much risk an organization is willing to accept, risk tolerance refers to the boundaries of acceptable variation in performance relative to the business objective. Risk tolerance is a performance metric. Figure 6.1 outlines some of the differences.
You may think of indicators and triggers in this context as the individual risks themselves, and the metrics used to measure them (e.g., key risk indicators). A key risk indicator (KRI) is a measurement of how risky an activity is. It differs from a key performance indicator (KPI) because a KPI is a leading metric while a KRI is a lagging metric. For instance, a KPI may be expressed as "We have patch coverage of 86%," while a KRI may be expressed as "When patch coverage falls below 80%, confirmed incidents rise by 60% month-over-month."
An organization may express its risk appetite as:
Brand is critical for our organization. As such, we have a low-risk appetite for negatively impacting our brand and brand loyalty. We will not make decisions that factor cost above our core beliefs, quality, or component choice. We value sustainability above revenue and growth. We will innovate within these parameters to develop products that meet market demands and have a moderate risk appetite to attain this goal.
The same organization may express one risk tolerance metric as:
We will not procure more than 10% of the critical components required for manufacturing widget "X" from outside of the United States.
So, what does this mean from a cybersecurity risk standpoint? It means do not get lost in the weeds. Providing metrics without the appropriate context is meaningless and will further distance you from being viewed as a strategic partner. You can help set that context by defining a cyber risk tolerance. Defining a cyber risk appetite is not just technical, and it requires discussions across the organization. The CEO, CFO, and the cybersecurity steering committee should all be involved so that cyber risk is tied into enterprise risk and reflects your organization's mission and values. These discussions need to consider how the organizational risk appetite is defined and the types of controls included to prioritize cyber risk management. The cyber risk appetite statement may look like the following when taking into account the example of organizational risk appetite:
It is essential that the cybersecurity risk management program is aligned with the enterprise risk management program and allows the organization to achieve its business goals in a method that complies with applicable laws and regulations. Our organization has defined that it has a low-risk appetite relating to impacts to brand and brand loyalty and moderate risk in sustainably achieving business objectives.
In support of the above, the organization has a low-risk appetite for the loss or breach of its intellectual property and consumer data. Information assets will be classified and protected with the commensurate security controls outlined in the Data Classification and Protection Policy (e.g., restricted, confidential, internal, or public). The organization has a low-risk appetite for a failure of access controls. All access to systems storing or processing data classified as "internal" or above will be controlled via multifactor authentication as outlined in the organization's Access Control policy.
While risk appetite is strategic and broad, risk tolerance is tactical and focused; however, they are closely linked. Per COSO, risk tolerance is the acceptable variation in performance. It describes the range of acceptable risk outcomes related to achieving a specific business objective to ensure the organization continues to operate within its defined risk appetite (depicted by the dotted lines in Figure 6.2). In other words, it helps management determine if a risk is acceptable or unacceptable. A specific risk target does not typically exceed where risk profile intersects risk appetite ("A" in Figure 6.2).
More on The CISO Evolution: Business Knowledge for Cybersecurity Executives
Learn more about this title from Wiley.
Read a Q&A with Lambros and Sharp about the business skills CISOs need to thrive in their challenging roles.
Risk tolerance does not focus on specific risks. Instead, risk tolerance focuses on business objectives and performance. As such, risk tolerance should be aligned, measured, and communicated in terms of business objectives. For example, risk tolerance may be lower for business objectives that are critical to achieving the organization's strategy and higher or less critical business objectives. The organization's existing risk profile is the current level and distribution of risks across the organization.
Risk capacity is the total amount of risk that the organization can absorb in pursuit of its objectives. Risk profile, risk capacity, and risk tolerance all inform an organization's risk appetite determination.

Excerpted with the permission of the publisher, Wiley, The CISO Evolution: Business Knowledge for Cybersecurity Executives by Matthew Sharp and Kyriakos "Rock" Lambros. Copyright 2022 by John Wiley & Sons Ltd. All rights reserved. This book is available wherever books and eBooks are sold.
About the book authors:
Matthew Sharp is the CISO for Logicworks where he leads the information security function. His role includes information security governance, risk management, architecture, and compliance. Previously, Matt served as a strategic advisor to CISOs of Fortune 500 and global institutions.
Kyriakos “Rock” Lambros is the CEO and Founder of RockCyber, LLC. He is a seasoned cybersecurity and information technology executive with expertise in aligning cybersecurity and technology strategy with enterprise business goals.
Editor's note: This article was updated in October 2024 to improve the reader experience.







